|
Digital Security and Privacy for Human Rights Defenders |
2.9 Malicious software and Spam
Abstract
Malware is a term used to describe software that damages your computer and compromises your security and the confidentiality of your information. It can be broken up into several categories, including viruses and spyware. Millions of computers around the world have been infected by a virus or spyware, causing huge problems in the industry. The Internet has become the most widely used medium for spreading malware, and we are always battling to protect ourselves from myriads of old and newly written malicious infections. The word ‘spam’ is used to describe undesired and unsolicited email messages, sent in bulk around the Internet and to our email accounts. This chapter will explain the differences between various types of malware, the history of famous infections and will provide assistance as well as a guide to how to protect against them. VirusesSimilar to a human virus, computer viruses infect computers and other technical devices with the intent of changing their stability, operation or integrity. They are usually small pieces of software code that are executed on your computer following a specific action you take. They also have a tendency to re-create and multiply. You can receive a virus in an email, on a inserted floppy disk or other removable media, by browsing to specific websites and sometimes just by being connected to the Internet. HistoryThe first recognised instance of a spreadable computer virus was the Elk Cloner. It was written around 1982 by a 15-year-old high school student Rich Skrenta and was aimed at Apple II systems. Elk Cloner spread by infecting the Apple II’s operating system and was transmitted on floppy disks. When the computer was booted from an infected floppy, a copy of the virus would automatically start. Whenever a new floppy disk was inserted into an infected computer, the virus copied itself to it, thereby allowing itself to spread. It did not cause specific harm to the computer, but was merely an annoyance. On every 50th booting, the virus would display a short ‘poem’:
Elk Cloner: The program with a personality
It will get on all your disks It will infiltrate your chips Yes it’s Cloner! It will stick to you like glue It will modify ram too Send in the Cloner!65 The first virus to infect a PC was called (c)Brain and was written by Basit and Amjad Farooq Alvi, two Pakistani software developers. They wanted to stop the piracy of the medical software they had written and claimed that the virus only existed to prevent breach of copyright. Originally, viruses were spread by floppy disks inserted into various computer systems. The Internet has provided a new means of spreading viruses around with the greatest of ease. The first well-known case was the Morris Worm, written by Robert Tappan Morris in 1998. It was estimated to have infected around 6,000 computers worldwide66 and caused between 10 and 100 million USD of damage. Morris received 3 years of probation and had to pay 10,000 USD in fines. The devastating effect the virus had on the Internet led to the creation of a new industry for countering similar attacks and resulted in the formation of CERT (Computer Emergency Response Team), a US federal-funded research institute and development centre (http://www.cert.org). The month of August 2003 was the worst ever for damages from viruses - the result of a simultaneous attack from the Blaster and Sobig worms. Causing untold damage around the world, it severely crippled Internet speeds. The writer of the Blaster virus, 18 year-old Jeffrey Lee Parson from Minnesota, was eventually caught and jailed for 18 months. The MyDoom virus of 2004 accounted for 1 in 12 of every email sent on the Internet and was able to co-ordinate the biggest denial of service attack67, involving more then 1 million computers from all over the globe. Malware variationsThere are numerous types of malware, and each has a specific method of operation and distribution.
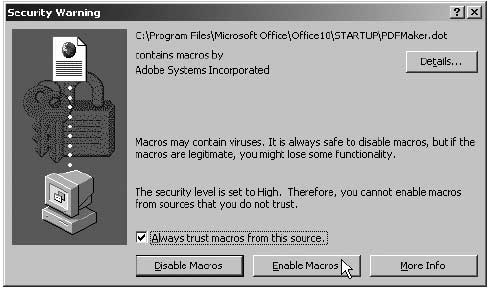
A warning of a macro inside an Adobe PDF document Always choose to ‘Disable Macros’ in your document. In your organisation, introduce a policy of saving all Word files in Rich Text Format (.rtf) and all Excel files as .csv. These file types do not carry macros.
Viruses are known to be spreading to mobile phones and personal organisers. Technically, any electronic medium with a processing unit can be infected by a virus. Virus hoaxes have also gained notoriety because of their crippling effects on companies and users. They are usually spread by email and warn you of an impeding new virus attack. They may also try to persuade you to click a link in the email, which will ‘help you to secure your computer system’. Albeit not terribly damaging, virus hoaxes slow down the Internet connection and fill email boxes with unnecessary email. An organisational policy that pro-actively prevents downloading and executing of viruses is required. Some of it can be done at the program level, by setting specific settings to make your programs more robust against viruses and by obtaining and running anti-virus, anti-spyware and firewall software. All software, including fixes for Windows, must be actively sought and updated. This will increase your protection against newly written malware. The main approach to tackling malware is at the policy level. You need to:
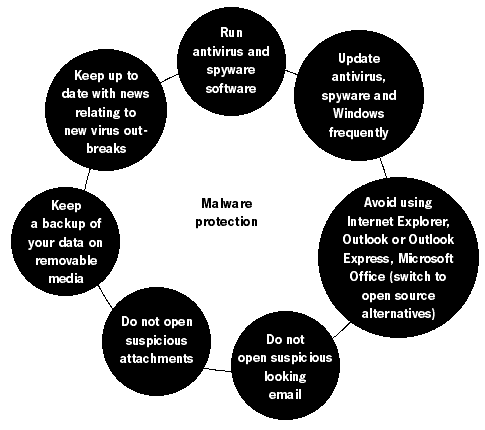
The most important rule is to be aware and vigilant. Take the required precautions but do not let the existence of anti-virus or anti-spyware programs give you a false sense of security. As you might have guessed from the above, it is a never-ending battle. Viruses spread not because of their clever programming, but because of the carelessness and nonchalance of the user. SpamSpam is the process of sending bulk and unsolicited emails. They normally take the form of advertising or nonsense messages that often fill up our email boxes. Spam is an activity aimed at increasing the profits of companies, and increasingly of spam gangs. It is a lucrative method, for the costs of mass distribution are minimal - far cheaper then postal junk mail and other means of mass advertising. Spam now accounts for 50% of all Internet activity and is an enormous problem to individuals and to businesses. This section will tell you how to reduce the amount of spam in your email box.Many on-line companies provide lists of their customers’ email addresses to organisations specialising in sending unsolicited commercial email (spam). Other companies mine email addresses from messages posted on mailing lists, newsgroups, or domain name registration data. In a test by the US Federal Trade Commission, an email address, posted in a chat room, began receiving spam within eight minutes of submitting a post69. HistoryThe term spam is derived from the British comedy series ‘Monty Python’. One of the episodes, ‘SPAM Sketch’, is set in a café where everything on the menu includes SPAM luncheon meat. As the waiter recites the SPAM-filled menu, a chorus of Viking patrons drowns out all conversation with a “SPAM, SPAM, SPAM, SPAM” refrain thus ‘SPAMming’ all other noises. The obsession with SPAM goes back to food rationing in Britain during and after World War II. SPAM (a ham substitute made from processed meat) was one of the few foods that was not restricted and was widely available, so by the end of the rationing period the British had been rather fed up with ‘luncheon meat’.70The concept of spamming as an advertising technique was first introduced in 1994 by two New York immigration lawyers wishing to promote their services through mass emailing. They argued it was a viable and justified new method of marketing and labelled their critics as “anti-commercial radicals”. Since then, the popularity of ‘spamming’ grew very quickly. Preventing spamThere are several methods of reducing the amount of spam you receive, although you may never be able to get rid of it completely. If you are using a webmail account (like Hotmail or Yahoo), the provider should have automatic spam filtering software installed. Some email programs (like Mozilla Thunderbird) have a built-in spam filter that learns what email you would classify as spam, and stops similar emails from cluttering up your inbox. Be aware that spam keeps being downloaded, but is automatically moved to the Junk folder.
The main method of spam prevention is not to reply or to click on any links in the spam message. Even if you are upset by the amount of spam and wish to reply to the message with a complaint or a request to stop the spamming, you are simply confirming the existence of your email address and labelling yourself as someone who reads spam and reacts to it. Never purchase anything advertised in spam messages. Even if it is legitimate, you’ll end up further funding the spammer market.
If you are sending a large group email, insert the contacts into the ‘Bcc’ field. This will hide the existence of the mass email and prevent spammers from using the list for their purposes. Also, switch off the email preview option in your email program. When an email is previewed, it may alert the spammers that your address exists and you have read the message.
If your account is already facing massive spamming and the filters are simply not working any more, you have no other option but open a new email account and be more vigilant. 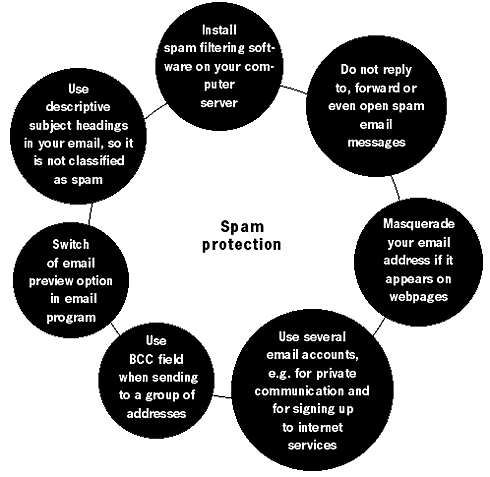
65
66
67
68
69
70 |
