4.3 Case Study 3
Securing and Archiving Data
Outline
A human rights NGO, based in a developing country, is providing free legal assistance to victims of human rights violations. They have collected the cases and assisted the town’s citizens for five years. Recently, they began to make a submission to the regional human rights court on a particularly complicated and sensitive case of police brutality to one of their clients. Last week, they received two threats from an unknown person – one was by telephone demanding they ceased their work immediately and another - worded by a local policeman. He said that the material they were collecting was considered dangerous to national security interests and could be confiscated at any time. The NGO lawyers are convinced that this is not true and is simply a method of intimidation. They are perfectly satisfied that the case falls within national laws and international agreements. The NGO wishes to pursue this case to the end and has applied to a funder for a small grant to help them increase the security of collected information.
The office is located in a well-protected building, with easy access to a busy street. The NGO has an established reputation within the local community and official circles. Their neighbours are always happy to assist and to keep an eye out for intruders. During its five-year operation, office security has not been compromised, the staff feel confident about their location and have established strict policies regarding the handling of office keys and client visits. Recent changes in the local government worry the NGO, as they fear that the police will be given permission to raid their office and confiscate case-related documents. They are prepared to challenge any such action in court but are concerned that the content of the confiscated material could compromise the security of many people. They decide to secure collected information against this possibility. It has also been decided to protect all case-related information collected since their establishment.
The office has one computer and the staff possess little technical skill. The computer has internet connection through a dial-up modem and the office purchases Internet cards with temporary connection details. This computer has long since ceased to function properly as it is plagued by viruses. The office cupboards are full of paper relating to cases the NGO has worked on in the past. The grant from the funder came to the sum of 1500USD.
Threats and Vulnerabilities
The NGO staff realise that the main threat they face is having their submission to the court compromised should the police confiscate their case material. This could possibly endanger their clients and witnesses. This threat can be realised by either:
- confiscation of all documents with a warrant
- illegal confiscation of documents by force
In either case, the outcome will be the same and the information must be protected against both eventualities. The NGO must not only protect this information but ensure that case details remain in their possession so that the work can continue. The NGO makes a list of their vulnerabilities to have a better understanding of what areas need the most attention.
- notes of cases of violations that exist on paper only are not secure
- the computer is not functioning because of viruses
- pirated/unlicensed software may be used as an excuse for computer confiscation
- files stored on computers are not secure against hackers
- there’s no backup system for documents in case they get confiscated or lost
Solutions
Access to information
It is decided to eliminate the risk, posed by the information that exists only on paper, by transferring it to the computer. The cases on paper will then be destroyed and all the data will be stored electronically, with the possibility of printing the required document upon request.
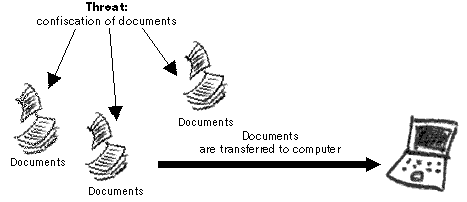
Paper documents are scanned to a computer
The information, currently held on paper, must also be stored securely while it is being computerised. For this purpose, a safe will be purchased
and all important documents will be kept in it prior to their computerisation, after which they will be destroyed
(the staff decide that the safest method to do that will be by burning).
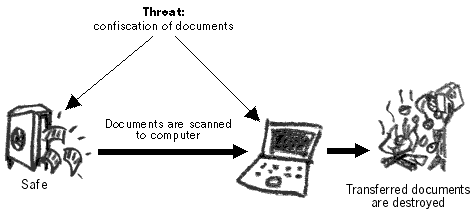
Redundant paper documents are destroyed
Computers
The NGO staff decide that their current computer is too old and may not be able to handle the large amount of information that will be needed to store all the scanned documents. After searching around the Internet and speaking with their friends, they realise that it is possible to buy a removable hard drive with large storage capacity. It is essentially a hard disk that can be carried around and plugged into any computer.
To protect the data stored on the computer, the staff are recommended to use encryption. Although no one is really sure how to encrypt, they obtain a copy of the Digital Security Toolkit
. It appears that the TrueCrypt program will be able to encrypt an entire hard drive so that no one will be able to access it without a password. They decide to encrypt the removable hard disk using TrueCrypt. If the removable hard drive is confiscated, the data on it stays encrypted.
Since all the information is centralised, it is essential that a backup system is created, in case the removable hard drive gets damaged or confiscated. The backup medium will be a DVD writer. At the end of each day, a DVD backup of the removable hard drive will be made and taken off site. Since the information on the hard drive is encrypted, it will remain encrypted on the DVDs.
Transferral of paper documents to electronic files is done by a scanner. It is estimated that one person operating a computer and scanner can digitise 100 pages per day. If so, the work can be completed within two weeks.
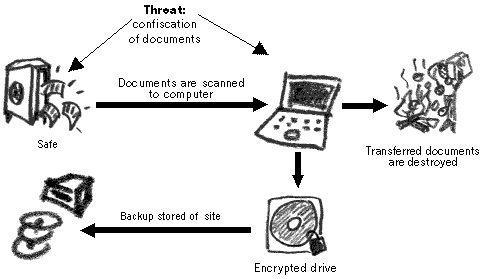
Electronic documents are protected from loss with the creation of a backup mechanism
Software
The NGO decides to purchase a copy of Microsoft Windows XP Home edition. The justification for this purchase is to ensure that all proprietary software on their computer is properly licensed. Instead of using a pirated version of Microsoft Office, they obtain a copy of the TheOpenCD (comes in package with the Digital Security Toolkit
) and decide to use Open Office and the GIMP program for scanning files. All other necessary software: anti-virus, firewall, encryption and DVD-burning - is also in the Box and is entirely free and open-source. The NGO therefore cannot get into trouble for using illegally obtained software.
Detailed responses to threats
Hardware: A staff member is sent to the nearest city to purchase a scanner, a removable hard drive and a removable DVD writer. These are readily available at most computer shops. The items purchased are of reputable brand and on the expensive side. An A4 scanner is priced at 150 USD, the removable hard drive with 100 gigabyte capacity costs 250 USD, and a removable DVD re-writer – 250USD as well.
Software: A copy of Microsoft Windows XP Home edition is also found in the computer shop retailing at 96USD. The staff member asks whether the computer shop could provide a technician to install all the hardware and software. There is a technician available and he will do the job for 100USD. The Digital Security Toolkit
is ordered through the website http://orders.ngoinabox.org. The Box also contains the OpenCD.
The computer technician installs a fresh copy of Windows XP and erases
all previous data. This is advisable to get rid of all the viruses and
malfunctions that previously resided on the computer. He also attaches
the DVD writer, the scanner and the removable hard drive. He then
installs the following software:
| SOFTWARE | PURPOSE | SOURCE |
| Open Office | Open Office Word processing, spreadsheets, presentations, database (fully compatible with Microsoft Office documents) | The OpenCD |
| GIMP | Image-editing and scanning | The OpenCD |
| Avast 4 | Anti-Virus | Secure NGO in a Box |
| Spybot | Anti-Spyware | Secure NGO in a Box | |
| Zone Alarm (internet computer) | Firewall | Secure NGO in a Box | |
| TrueCrypt (data computer) | Disk encryption | Secure NGO in a Box | |
| DeepBurner (data computer) | DVD writing software | Secure NGO in a Box | |
Encryption: The TrueCrypt program will encrypt the removable hard drive in such a way, that it could be easily copied onto a DVD at the end of each day. The staff create partitions on the removable hard drive, each sized at 4 gigabytes (which complements the amount of storage space on a DVD).
The encrypted partition is protected by a password, known only to the operational staff. The same password will be necessary to open this partition from the DVD. The password containing 12 characters and comprising both letters and numbers is chosen. It is not written down anywhere and is memorised by all those requiring access.
Backup: At the end of each day, the dismounted partition, now a file, is copied to the DVD. It is better to re-write the previous version of the file (for this, you will need to purchase a re-writeable DVD recorder and re-writeable DVD disks).
The backup DVD is kept off-site – at one of the employees’ home. At the end of each week, a separate backup is made and kept at an undisclosed location. This is an additional backup measure, in case the removable hard drive and daily backups are confiscated.
Budget
| A4 Scanner | 150 USD |
| Removable hard drive | 250 USD |
| Removable DVD re-writer | 250 USD |
| 10 DVD re-writeable disks | 50 USD |
| Microsoft Windows XP | 96 USD |
| Computer services | 100 USD |
| Safe | 300 USD |
|
Total: 1,145 USD
|
There is more money left in the budget, in case a new printer or additional DVD disks need to be purchased.
The advantage of this system is the increased security of all the documents collected by the NGO. After the initial period of digitising paper documents, there will be no data readily accessible to an outsider. The entire collection of documents will be easily transferable between computers. Even if all equipment is confiscated or damaged, the staff will only require the DVD disk with a backup and another computer with the TrueCrypt program installed. Of course, someone must know the password!
|



