|
Digital Security and Privacy for Human Rights Defenders |
2.6 Circumvention of Internet censorship and filtering
Abstract
This chapter will show you different methods of bypassing Internet censorship and protecting yourself from keyword filtering. In other words, it will explain how to access blocked websites, how to conceal from surveillance agents whatever you are reading or sending on the Internet, and how to hide your presence from Internet monitoring. For non-technical readers, it is advisable to first review the previous chapter on ‘Internet surveillance and monitoring’ as well as the ‘Internet explained’ appendices, in order to understand this section in full. Many tools and strategies to circumvent Internet restrictions are in existence today. This chapter will introduce you to only a few of them. With time, many well-known tools and websites could also get censored by surveillance agents in your country. To maintain your right to the freedom of the Internet, you will have to find new websites and tools that offer similar services. This can usually be achieved by extensive web searching and via communication with your peers. The purpose of this chapter is to make you aware of current services and strategies to use in the future. Proxy serversIt is relatively easy to block access to a website from a particular country, but it is also not that difficult to bypass these blocks. If you are not allowed to access bbc.co.uk, you can ask another computer (proxy) to fetch the website for us. Thus you will effectively be accessing only the proxy and therefore won’t be restricted by your country’s filtering rules. There are thousands of such proxies, and their mission is to be the intermediary between a client’s computer and a host website. Since there are many countries in the world which do not block access to websites on human rights, independent journalism, religion, etc., you can use the proxies set up in them to get access to information which is blocked in your country.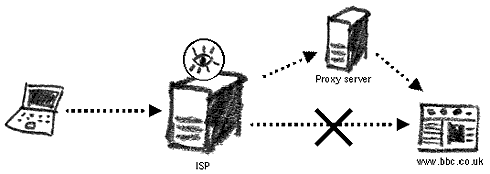
Re-routing a censored connection through a proxy server Proxy servers are divided into several categories. It is important to know the functions and security provided by the proxy server you select to use. Please remember that you cannot conceal the information you are sending and receiving from the proxy server itself. CGI proxyThe simplest type of proxy server is CGI proxy. The coding for proxy server operations is built into a web page and you can use its services simply by browsing the Internet directly through it. Two famous CGI proxies are Anonymizer and The Cloak. Their popularity has led many countries that practise Internet filtering to block access to these sites as well. There are many other public CGI proxies that you can find my entering the keywords ‘CGI proxy’ or ‘nph-proxy’ into a search engine.

Remember that if the Internet connection is not encrypted (HTTP), it is still possible to read the data you are sending or receiving. HTTP proxyThis is a standard proxy that will fetch a blocked website for you. It is possible for surveillance to see that you are connecting to a proxy server and the website you are trying to access through it.Both the CGI and HTTP proxy servers can be further secured by having one or both of the following elements: HTTPS (or SSL) proxyAn encrypted tunnel is created between you and the proxy server and surveillance agencies cannot know the destination website, but only see that you are connecting to the proxy server itself. This is a more secure option when using a proxy, but you should be aware of Man-in-the-Middle attacks (see ‘Encryption on the Internet’ chapter) and know that information you send and receive is not hidden from the proxy server provider.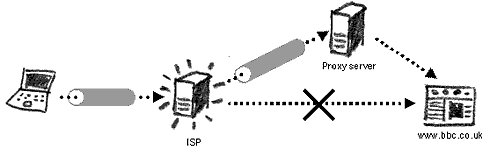
Encrypting your connection over SSL to the proxy server Anonymous proxyYour connection to the proxy server is not encrypted but the proxy is set up so that it hides your origin at the destination website and reveals only that the website is communicating with the proxy server itself.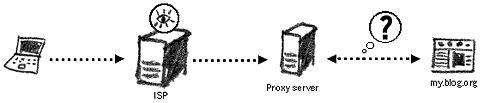
The visited website does not know the origin (the real IP address) of your computer Here’s a list of websites that collect current information about new proxy servers you could connect to. These lists contain a range of standard HTTP, secure and anonymous proxies.
These websites will show you a range of different proxy servers. They will always consist of an IP address and port number. You will need to insert these details manually into your web browser. Internet ExplorerTo insert a proxy server into your Internet Explorer web browser, on the menu bar:
Select: Tools > Options Insert the proxy IP address and port number into the relevant windows of the ‘HTTP’ line. Mozilla FirefoxTo insert a proxy server into your Mozilla Firefox web browser, on the menu bar:
Select: Tools > Options 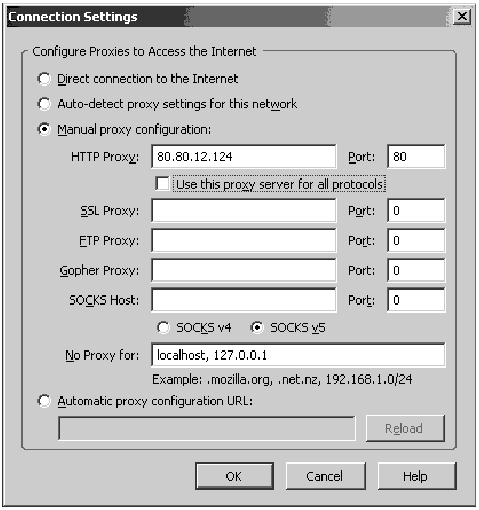
Setting a proxy server in Mozilla Firefox
Insert the proxy IP address and port number into the relevant windows of the ‘HTTP’ line. 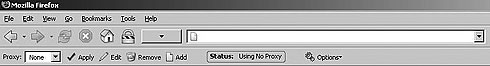
The switchproxy toolbar in Mozilla Firefox 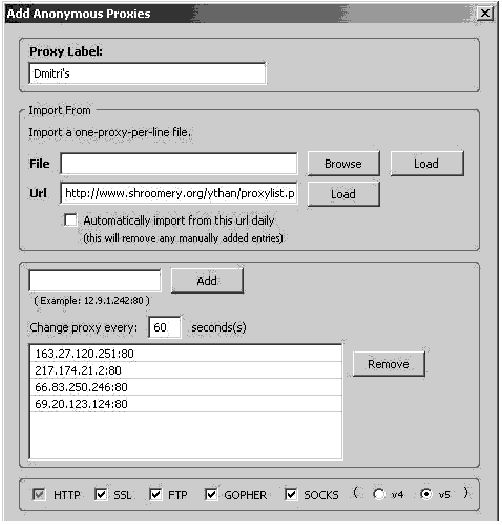
The switchproxy configuration screen Private circumventorsThese are proxy servers, set up by your friends or colleagues from the countries that do not filter the websites you wish to access. They are not well-known, and you will need either the IP address and port number, or in the case of a CGI proxy, the web page address and, possibly, login details as well. The main advantage of these circumventors is that they use trust networks – a private group of friends sharing their computer resources to help each other. Such networks provide for greater privacy as they are closed to the public and hence difficult to detect and to block.Psiphon54 is a recently developed private CGI proxy that aims to use trust relationships between people wishing to help their friends from the countries that censor the Internet. The server is easily installed on a computer running Microsoft Windows and generates login details for its clients. The details (IP address, user name and password) are passed among a closed circle of friends who then use the Psiphon computer’s Internet connection as their proxy. Psiphon adds another search bar to your browser screen. You should type all your addresses in there now. 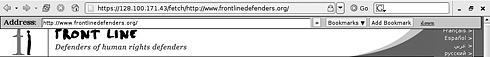
The Psiphon CGI proxy will fetch websites for you that may be blocked in your country Peacefire Circumventor55 – allows you to create your own CGI proxy server for others to use. You will need a dedicated computer and an Internet connection to install and run this server. It is recommended that your server is installed in a country that does not implement Internet censorship. The connection details to your computer/proxy server are then passed to users living in the countries that do implement censorship. Commercial circumventorsThere are a number of fee-paying circumvention software programs and services available on the Internet. They provide good security and may not be blocked in your country as they are often used by businesses.Anonymity NetworksUsing proxy servers has its disadvantages. They are often difficult to find and do not always offer ideal security for your Internet browsing. However, there exist Internet tools that will perform all functions of a proxy server, including much higher levels of privacy and anonymity for you.Imagine that you send a letter to a friend and package it in several different envelopes writing a different address on each one. The letter will circulate around these addresses in a secret order, and none of the addressees will know its origin or final destination, but only the previous address it came from and the next one it will be going to. Similar systems have been created on the Internet. A recent and stable addition to them is known as the TOR network.56 It will anonymise your presence on the Internet and your browsing requests. Surveillance agents at your ISP or a country gateway will not know the final destination of your browsing query and the website you visit will not know where your request came from. Increasingly, the TOR network is being used as a circumvention tool, easily bypassing national firewalls and website filters. 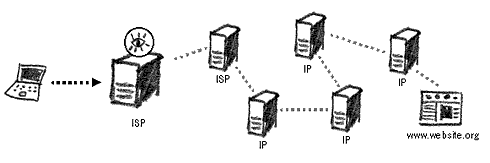
Anonymising your Internet presence on the TOR network
It relies on a number of servers (and on the volunteers to set them up) around the world and uses encryption between each of the points your message passes through. Therefore, the computers that your request goes through, will not be able to make sense of the data or decrypt it.
Freenet58 – is an anonymity network for document storage and publishing. All members of the network donate a small portion of their hard drive for storing information from other members. The files are encrypted and not accessible to the computer owner. This way you can store your documents, websites and messages on multiple computers, with secure and anonymous connections. The Freenet network has been especially popular in China and in the Middle East. A word on anonymous Internet publishingThose who maintain (or contribute to) a blog or an Internet forum need to be aware that their anonymity will not be guaranteed merely by signing with a pseudonym. Every blog entry records the IP address of the computer it was sent from, and many ISPs record all traffic that has passed through them. Therefore, if you are publishing sensitive information on a website, you must take precautions not to be found out. By using anonymous proxy servers you can disguise your IP origin from a particular website; by using an SSL proxy you can hide the article you are uploading from the ISP. Another option is to use the Tor anonymity network (if your blog site will function with it).One aspect of security that you cannot guarantee by using these servers is time stamping. If, for example, you were to publish a website about government activity in your country by using the Tor network, surveillance agents won’t see that you were sending this information to a particular blog, but they may notice that whenever you enter an Internet café a new post appears on the site. This could probably be linked to you, especially if your Internet café owner writes down your name and the time of your visit. To overcome this difficulty, it would be advisable to ask friends from a different country to post the blog for you. You could use a secure webmail service (or encryption) to send the article to them and ask them to wait for a while before publishing it on your blog. For an extensive guide to online publishing, see ‘Guide for bloggers and cyber-dissidents’ from the Reporters sans frontières web page.59 SummaryThe tools and techniques, described in this chapter, are useful to those living under the regimes that apply strong censorship and filtering to the Internet. With their help, you can get around some of the blocks to accessing websites and regain some privacy when publishing material online. Bear in mind that the countries practising Internet censorship and filtering are constantly on the lookout for new proxy servers and privacy tools with the intention of blocking access to them as well. In response, users from all over the world are setting up new proxies every day – a true cat and mouse game.
49
50
51
52
53
55
57
59 |
