|
Digital Security and Privacy for Human Rights Defenders |
2.5 Internet Surveillance and Monitoring
Abstract
Surveillance and intelligence gathering have moved on – from monitoring phone calls and opening people’s mail – to the Internet. Because of the Internet’s open structure, today’s surveillance can be carried out by governments, businesses, hackers and criminals. It is relatively simple to establish mechanisms that will record and monitor all of your Internet activity. All websites log information about their visitors (IP address and time of visit) as do the majority of email providers. Such surveillance has even become mandatory in many countries. In 2006, the EU passed the legislation requiring the ISPs to store the traffic data of all their subscribers for a maximum period of 2 years,36 although some member states are not adhering to these rules and are storing the information for much longer periods. Let’s have a look at how to monitor and censor your Internet activity on a local, national and global level. Monitoring Internet browsing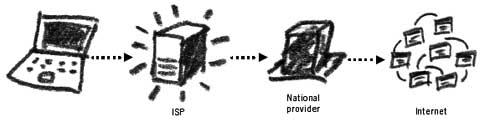
The ISP can monitor your Internet connection
When you wish to eavesdrop on someone else’s phone call, you need to get physical access to the telephone line or a contact at the phone exchange who would provide access to the line used by the conversing parties. Similarly, on the Internet it is possible to either intercept the line that connects you to the Internet or persuade the ISP to do the same. By doing this, all Internet activity originating from your computer can be recorded or even controlled by the surveillance mechanism.
All countries have access to an Internet gateway. This is like a door that can open or close to control the Internet access to and from the given country. All the Internet traffic will therefore pass through the national gateway, and one can assume that to have control over the country’s gateway means being able to access to all country-related Internet traffic38. China has installed a system to monitor and filter all Internet traffic on its national gateway, known as the ‘great firewall’, and it restricts the Internet access for the entire population of China. Recently, the Chinese built an additional structure into this surveillance system. Known as Golden Shield, it can bring the filtering mechanisms into smaller regional networks, thereby distributing the workload from the national gateway to the local routers. 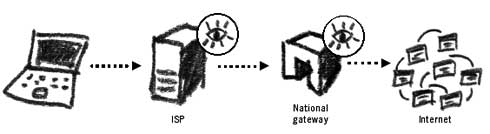
Internet monitoring at the ISP and the national gateway The above-mentioned tools for monitoring and censoring Internet traffic were not deemed sufficient in all the countries. The US, UK, Canada, Australia and New Zealand began to develop a global surveillance system that would encapsulate all major traffic points on the Internet. The events of September 11 in the United States led to huge investments to improve the system known as ECHELON which operates under the supervision of the National Security Agency (NSA). It is not known for how long ECHELON keeps the traffic data. It may seem that on a global level it is difficult to efficiently analyse and categorise all Internet and telephone communication, but the NSA claims a 90% success in doing that.39 CookiesRecords of our Internet activity are further stored on the websites we visit and on our personal computers. Many websites require installation of a cookie on our computer. A cookie is a small amount of data that stores specific user information about us. For instance, it could record our country of residence, so that we are presented with a relevant country page when visiting a particular website. This is often practised by airline websites. Other information could include the links we have followed to arrive at this or that website, or even personal data about us from our own computers. After browsing the internet for a month, you may have hundreds of different cookies on your computer. Accessing them can reveal information about your interests and affiliations. A cookie on your computer can act as a proof of your visiting a particular website. The largest Internet advertising service, DoubleClick, has agreements with thousands of websites and maintains cookies on over 100 million users, each linking to hundreds of details of the user’s browsing habits.40It is possible to delete cookies from your computer. This can be done from your Internet browser or by finding and deleting them manually. It is also possible to tell your browser not to accept cookies at all. This may result in many websites refusing to open on your computer, but will provide you with maximum protection from cookie infiltration. Monitoring EmailEmail communication uses the same principles as general Internet browsing, except that each message of ours has a destination: another person who also connects to the Internet through his or her country’s local provider.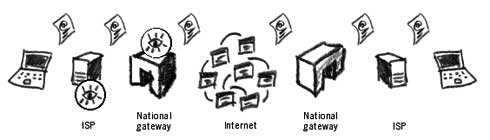
Monitoring email at the ISP and national gateway Following this scheme, our email message can be intercepted at all major routing points on its way. If you live in a country with strong legal protection of privacy, its legislation won’t apply when your email reaches the ISP of the recipient in a country with different privacy laws. Bear in mind that whilst your email is on its way from country A to country B, it could pass the routers of several other countries on its way. Many ISPs and email providers keep a copy of all emails on their servers. Sometimes this is to our benefit, as we may want to access an email that was sent to us 3 years ago. However, it also allows an outside party to request/demand access to our email accounts. Yahoo! handed over to the Chinese government its user information on four Chinese dissidents resulting in their arrest and conviction.41 SpoofingIt is relatively easy to ‘spoof’ an email address. Spoofing means that you fake the name and email address of the sender that can appear as a random address or the one of someone you know. For example, someone can use your email address and name to send a controversial article to a newspaper. The newspaper does not bother to verify whether it was actually you who had sent the article and simply publishes it. The outcome could be embarrassment, damaged reputation and even litigation. Email can also be intercepted and its contents altered while it is en route to its destination. It is almost impossible to tell a real email from a spoofed one, as all its identifying features can be faked. Digital signatures are the only way to make sure the message is not tampered with or faked42. 
Your message or identity can be spoofed by an adversary on the Internet Internet & Email FilteringApart from monitoring our Internet activity and emails, government and intelligence bodies have the ability to scan the contents of our messages and to prevent us from accessing certain websites. At this point, surveillance becomes censorship in breach of Articles 12 & 19 of the Universal Declaration of Human Rights43.All information on the Internet, unless otherwise specified, travels in an open manner. When you send an email, the data in it goes to its destination unsecured. To compare this transmission to a telephone conversation, if you were you to pick up the phone at the ISP, you would hear the message content read out to you by all ISPs users currently sending emails and/or browsing webpages! Therefore all your email as well as exchanges from Internet forums or blogs can be easily intercepted and read. Internet filtering scans the contents of every web page, blog of forum that you visit. We have seen already how easy it is to collect all our email and Internet traffic, and one can only imagine the amount of information freely submitted to the surveillance agencies simply by not making our communications secure. Certain countries are particularly sensitive to the information communicated by human rights organisations. Modern technology means that it is no longer necessary to sit in a dark room reading all email messages in or out of the country in search of undesirable or damaging information. This task is now performed by computers and is known as filtering. Email FilteringA program to scan the content of all email messages is installed at the ISP or a national gateway. It is instructed to look for the keywords ‘human rights’ or ‘freedom of expression’. In reality, it could be programmed to search for thousands of specific words and phrases. Whenever an email containing the listed keyword is found, it is either blocked and not allowed to pass further on, or recorded for further investigation of the sender’s and recipient’s identity. Filtering can occur at any point of the message’s routing on the Internet.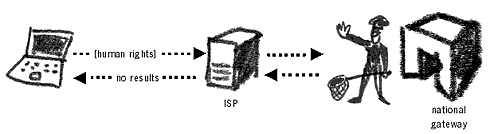
Certain words in your email could trigger the filtering mechanisms The ECHELON system uses the above filtering technology. Here’s a list of some words that would trigger a response should they be found in your email by ECHELON. Rewson, SAFE, Waihopai, INFOSEC, ASPIC, MI6, Information Security, SAI, Information Warfare, IW, IS, Privacy, Information Terrorism, Terrorism Defensive Information, Defense Information Warfare, Offensive Information, Offensive Information Warfare, The Artful Dodger, NAIA, SAPM, ASU, ASTS, National Information Infrastructure, InfoSec, SAO, Reno, Compsec, JICS, Computer Terrorism, Firewalls, Secure Internet Connections, RSP, ISS, JDF, Ermes, Passwords, NAAP, DefCon V, RSO, Hackers, Encryption, ASWS, CUN, CISU, CUSI, M.A.R.E., MARE, UFO, IFO, Pacini, Angela, Espionage, USDOJ, NSA, CIA, S/Key, SSL, FBI, Secert Service44 Internet FilteringThe same methodology is applied to Internet browsing. When you enter a search query into Google, it is passed through the ISP and a country gateway, before you get a reply. A filtering system could intercept your search for ‘human rights’ and return a null or wrong result. Below are images of a search result from 2004 on ‘falundafa’ (a banned spiritual movement in China) performed on Google.com from China.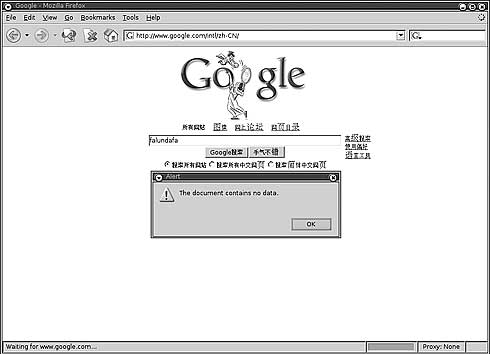
It appears as if there is no information on this topic in Google, but the error message actually comes from the filtering software, not Google itself 45. Internet filtering can also scan the content of websites you wish to access, and block your request, should the website contain any words the filter is programmed to look out for. Internet CensorshipNumerous countries have banned access to certain websites for their citizens. These websites present information on religious extremism, terrorism, paedophilia. Some countries also block websites that criticise or expose government policy, discuss issues of human rights or provide tools that could enable one to bypass these censorship blocks. Here is the result of a request from Saudi Arabia to access a banned website. 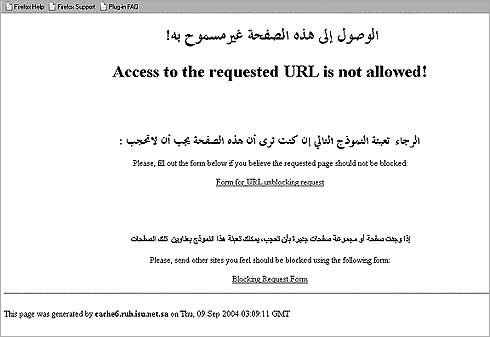
A screenshot of a blocked website from inside Saudi Arabia Governments tend to decide for themselves what content they wish to censor. The majority of governments that perform filtering use US and Israeli technology. Some of the more infamous products are SmartFilter and WebSense. These are bought (or pirated) by states who then set up the filtering based on the software’s criteria, with additional modifications. Websites can be blocked and Internet searches restricted with the help of the three following methods: Blocking by DNSThis block on the filter ensures that all requests to www.bbc.co.uk will not be allowed to pass. The block is applied to the domain name of the website. Should the website be re-registered or mirrored under a different domain name, it will become accessible again.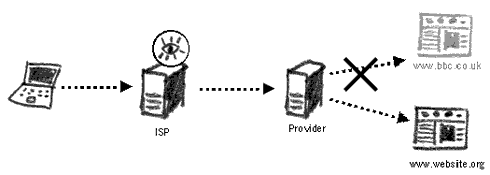
Blocking by IPThis method blocks the website’s IP number from access. This is a much more effective block as a new DNS name for the website could still point to the same IP. However, a problem arises when blocking websites by IP. Sometimes these websites sit on large web servers that host several thousands of different websites. These web servers only have one IP. Blocking a website’s IP address effectively blocks all other websites sitting on the same webserver.46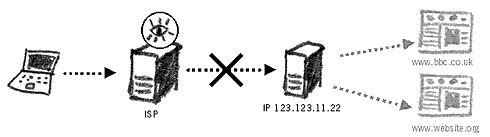
Blocking by keywordsAny email or search query that contains words banned by the filter is not allowed to pass through. The same applies to any website that contains banned words.These rules can be applied separately or together to create filtering and blocking capacity. Some countries rely on the pre-defined categories of the filtering software and add new websites to its configuration, whilst others employ huge teams of people to scan the Internet and catalogue what should appear in the filter. The Internet’s open structure is being limited and reduced to allow only approved content to appear for the nationals of many countries. For an in-depth study into country-specific filtering methods and technology, go to the OpenNet Initiative – Country Studies website.47 DNS hijackingThis is a recent Internet practice that has been used in presidential campaigns (2004 US elections) as well as by countries that filter the Internet. When you enter an address of a website you wish to visit, you are automatically re-directed to another website. Some users may not even notice the difference.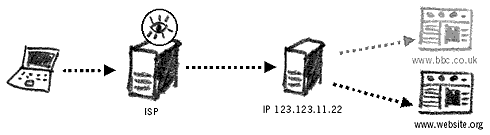
On September 8th 2002, users in China were prevented from going to Google’s web search page. Instead, they were re-directed to a number of China-based pages. The address in the URL said www.google.com48 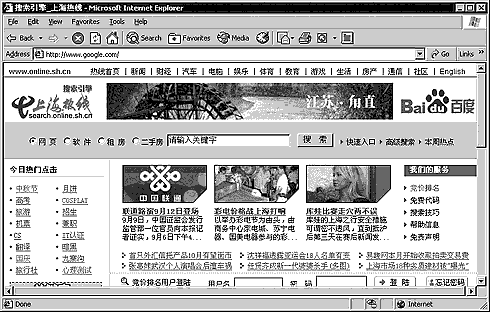
A screenshot of the Chinese Internet hijacking the www.google.com DNS
36
37
38
39
40
41
42
43
44
45
46
47
48 |
