|
Digital Security and Privacy for Human Rights Defenders |
2.2 Password Protection
Abstract
Having good passwords is an essential part of using computers. They act as a security barrier providing authentication to the required service, be it an email account, network login or online banking. A password is like a key to a door. You may have several different keys for your home, your office, your car and your safe. None of the locks are the same, and you have a collection of different keys to open them. This makes breaking in more difficult. Even if the thief manages to find one corresponding key, they will not be able to open all other doors. Our door locks are getting more sophisticated and expensive. They are made of many different components with the sole purpose of preventing break-ins. The same should apply to your passwords. They are a door lock to your information banks. The advent of computers has seen passwords protecting the information that is often of a greater value than whatever is stored in your cupboard or safe. Therefore, in a technical sense, your passwords should be as strong as the most expensive safe to protect the information they guard. In the world of digital security, a good password is the most essential and important element of any system. History has shown that breaking passwords is the most common method for hackers and intruders to attack your information systems. Cracking PasswordsHow do passwords get compromised? There are several methods of doing this. One is to observe someone typing their password from a distance. Another - to install a spyware program that would record all the keystrokes typed into the computer and transmit them to the attacker. Both of these can be prevented by vigilant behaviour. Make sure you notice your surroundings and always run frequently updated anti-spyware and anti-virus software.ProfilingProfiling involves making an educated guess by collecting personal information and facts about the person who owns the password. In many cases, our passwords reflect something which is easy for us to remember - year of birth, name of a family member or a friend, town of birth, favourite football team, etc. The profilers take notice of these and other similar facts. If they have access to your office, they may also spot the books on your bookshelf. The naming system for your passwords is excusable (at least, until you finish reading this chapter!) since the ability to remember many different passwords that have no association with you and are difficult to memorise is limited. However, guessing a password by possessing personal information about the user is still the most common method of compromising a system that continues to be extremely successful for motivated hackers.Many password systems on the Internet give you the option of recovering your password, provided you answer a previously set ‘secret question’. For some unexplained reason, these secret questions (which you set when creating an account) invariably have something to do with the name of your pet, your first school or your mother’s maiden name. This makes the profiler’s job extremely easy. They will not even have to work out what your password is, but will simply answer the secret question and receive your password in an email. If you are ever asked to set up a recovery mechanism in the form of answering a simple question about your personal life, do not use it. If it is a requirement for completing the registration process, just write something unintelligible. Don’t rely on the secret question recovery process to remember a password you have forgotten. 
Personal passwords are easily guessed Social EngineeringMany people have been tricked into revealing their passwords through cleverly created scenarios and questions. It can happen in a phone call (supposedly) from your ISP saying that they are upgrading their servers and in order to make sure you do not lose any email in the process, they require your password. Someone could pose as a colleague from another branch of your NGO and request the password to access the shared email account, as the person who knows it is currently ill and they need to send something urgently. This is known as social engineering. There have been numerous cases of employees revealing potentially damaging information simply because they were tricked into it. It remains an effective method for hackers to try to gain access to a system.No one should never reveal any computer related information (especially passwords and access codes) on the phone or to someone whose identity they cannot verify19. Brute ForceBrute force is the practice of guessing a password by using all sorts of possible combinations. This could involve taking an electronic version of a dictionary and trying every word in it. It may seem a lengthy task for a human, but for a computer it takes only seconds. If your password is a properly spelt word from a dictionary, it can be compromised within minutes by a brute force attack.Perhaps you have used the opening lines from one of a 1000 most famous songs or poems as your password? The digital world is ever expanding and growing as the the whole of world literature and thought is being transferred onto it. There exist electronic compilations of the works of literature, and these can also be used to break your password. You should think twice before using a natural language password – a intelligible or a famous phrase, a combination of words or a complete sentence. Some password systems are protected against brute force attacks. Take a bank machine or a mobile phone as an example. Even though your password is usually a simple combination of four digits, the system will shut down (take your card, lock your phone) after three incorrect guesses. Creating PasswordsMnemonicsThere exist various methods for creating passwords which are difficult to break and easy for us to remember. A popular one is mnemonics (a method or system for improving the memory, such as a rhyme or acronym20). Lets take a common phrase: To be or not to be? That is the question (Hamlet, Shakespeare) We can convert this to 2Bon2B?TitQ In this example, we have substituted words with similar-sounding numbers and acronyms, with nouns and verbs capitalised and prefixes appearing in small-case letters. Or, for instance: I had a dream, where all men were born equal (Martin Luther King) 1haDwaMwB= This appears to be a relatively random password and not so difficult for you to remember as you know the trick of how it was made up. Other tips include substituting numbers for similar-looking letters, abbreviating words that resemble numbers and using emoticons. I, i, l, t = 1 o,O = 0 s, S = 5,2 four, for, fore = 4 two, to, too = 2 Are you happy today? = rU:-)2d? These are but basic examples, and you can always create your own method of coding numbers and words. It is advisable that you do so. Note: Please do not use the examples shown above as your password!
Using software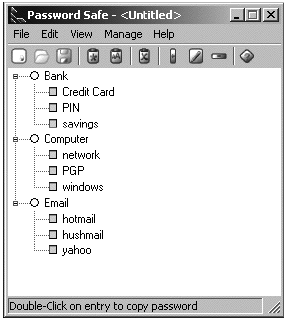
A screenshot from the PasswordSafe program You can group your passwords into categories and copy them from the program to the screen by using the clipboard. The passwords are stored encrypted in the program and have to be unlocked by you. Hence, the only password you will need to remember is the one to access the program itself. It will take you a little while to begin creating and storing all passwords in such a program, but the benefits of security hugely outweigh the little of inconvenience of doing so. Your password is often the first and most important guarantee of the security of your information. It is like a door to the house where you live. Using a bad password or no password at all, is like leaving the door open all night. Maybe, no one will walk in, or, maybe, someone will and steal all your belongings. Pay great attention to how you create your passwords and where you keep them. 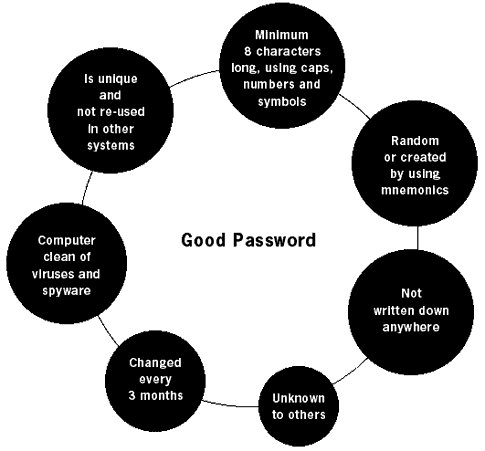
18
19
20
21 |
