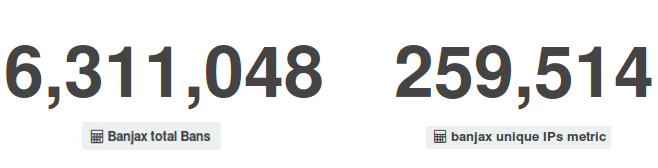In 2016, Deflect set some records and helped defend online voices against some record breaking attacks. Throughout the year, Deflect served a bit less than 2% of the population connected to the Internet in 2016, published 3 DDoS analytic reports, mitigated the strongest DDoS attack that ever targeted our network, renewed its funding and began to look for new revenue-generating opportunities, and added some excellent people to the team, including more sysops to offer 24/7 support and a business development manager to make sure that our infrastructure will keep existing also in the long term.
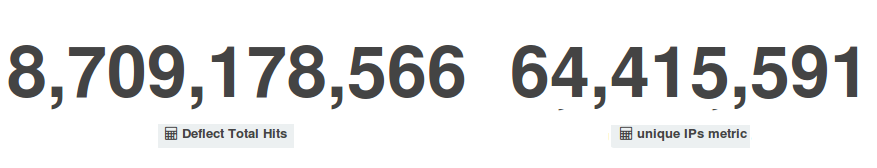
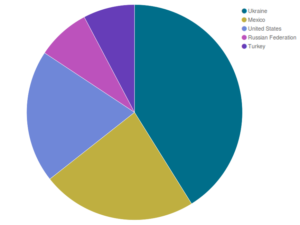
In 12 months, the Deflect network received 8.7 billion hits from 64.4 million users. At the same time, Deflect mitigation tools banned 259,514 unique bot IPs, scoring 6.3 million banning events. Visitors of Deflected websites originated primarily from Ukraine (41.13%), Mexico (23.24%), the United States (19.94%), the Russian Federation (7.98%), and Turkey (7.72%).
[one_third]
In March we published the first Deflect Labs report, covering attacks against Kotsubynske, a Ukrainian independent media outlet battling corruption at the local council. This was a first test of the software and infrastructure we had developed over six months. As we would find out later, Deflect was pivotal in making sure that one of the directors of Kotsubynske got re-elected to his town council to continue asking questions and weeding out the truth. The group’s efforts are now being replicated in a dozen different towns across Ukraine. It confirmed our initial hypothesis turning the tables on our clients’ adversaries by shining a light on their methods and provenance, and improving advocacy for the target website.
In April we released the world’s first free, secure and open source WordPress hosting framework, called eQPress and available for free to any group that meets Deflect’s eligibility criteria. In another moment of inspiration, we compiled our sysadmin knowledge into a set of Ansible recipes, allowing anyone to provision a secure communications server, in a project called Caislean.
In June Deflect Labs published its second report, covering attacks against the BDS movement and correlating the behaviour of a particular botnet to incidents involving other organizations working in the region. As could be expected, the topic of the Israel-Palestine conflict generated a lot of media coverage, which helped promote the ideas and tools proposed by the project.
In late June, the Deflect project received a much needed funding top-up, allowing us to keep doing our work and further improve our infrastructure and tool set. This time we focused on usability: starting in late summer and throughout the autumn, the Deflect Dashboard underwent a major overhaul, including automation of processes, a streamlining of communications with users, new statistics in the Deflect Dashboard, and a new TLS/SSL system that allows us to create Let’s Encrypt certificates to secure connections to Deflected websites, while our users can keep their server certificates private.
In late September the team gathered in the mountains of Quebec for a company retreat. During this week people who are normally scattered all over the planet got to meet each other in person, relax together, refine our workplan and discuss strategies. One of the results of the retreat we are particularly proud of is the final version of the Deflect Terms of Service and Privacy Notice.
In October Richard, our technical project manager, presented Deflect at the Freedom Online Coalition, outlining Deflect’s positive impact on the work of civil society.
Six months of research and analytic work finally resulted in the publication of our third and most detailed Deflect Labs report covering attacks against the Black Lives Matter movement. Published on the 13th December, the report was covered by a feature in Ars Technica and articles in other media. This coincided with the release of our botnet behavioural classification library, Bothound. We will follow up with a set of standards for responsible data sharing among mitigation providers in 2017.
The challenges in the sphere of web security are never-ending, and last year we saw DDoS attacks grow stronger and stronger, reaching an unprecedented peak of 1.2 terabits per second and taking down important web services in entire world regions. But as Deflect Labs’ 3rd report shows, DDoS attacks don’t need to be huge or to rely on advanced techniques to be successful – silencing online voices has become so easy and cheap that Brian Krebs is talking about a “democratization of censorship”. To fight this alarming trend, and safeguard freedom of speech, we need to join forces with as many actors as possible within the civil society and the community of web security and mitigation experts. Creating a wide network defending a free internet, and sharing resources to offer a better protection is our hope for this year. Get in touch if you’d like to contribute!