Botnet attack analysis covering reporting period February 1 – 29 2016
Deflect protected website – kotsubynske.com.ua
This report covers attacks against the Kotsubynske independent media news site in Ukraine, in particular during the first two weeks of February 2016. It details the various methods used to bring down the website via distributed denial of service attacks. The attacks were not successful.
General Info
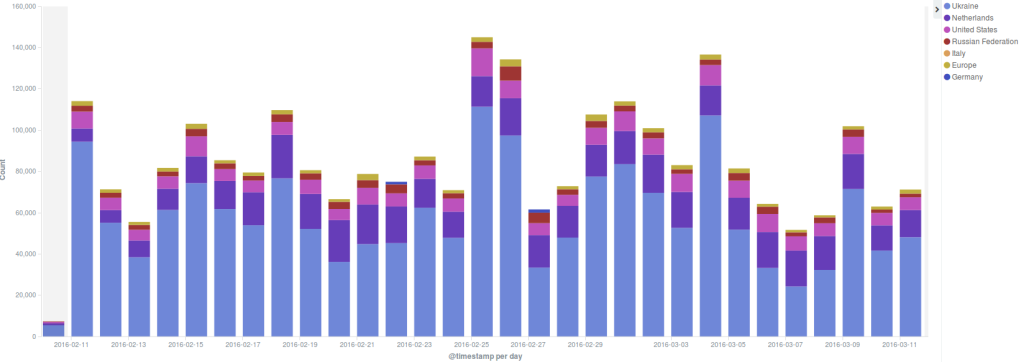
Kotsubynske is a media website online since 2010 created by local journalists and civil society in response to the appropriation and sale of public land (Bylichaniski forest) by local authorities. The website publishes local news, political analysis and exposes corruption scandals in the region. The site registered for Deflect protection during an ongoing series of DDoS attacks late in 2015. The website is entirely in Ukrainian. The website receives on average 80-120 thousands daily hits, primarily from Ukraine, the Netherlands and the United States.
Attack Profile
Beginning on the 1st of February, Deflect notices a rise in hits against this website originating primarily from Vietnamese IPs. This may be a probing attack and it does not succeed. On the 6th of February, over 1,300,000 hits are recorded against this website in a single day. Our botnet defence system bans several botnets, the largest of which comprises just over 500 unique participants (bots).
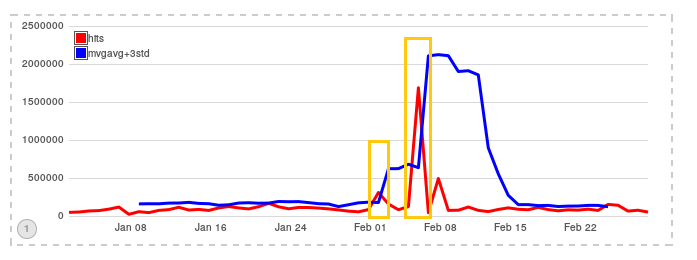
Using the ‘Timelion’ tool to detect time series based anomalies on the network, such as those caused by DDoS attacks, we notice a significant deviation from the average pattern of visitors to the Kotsubynske website (on the diagram below, hits count on the website are in red, while the blue represents a 7-day moving average plus 3 times standard deviation, yellow rectangles mark the anomalies). The fact that the deviation from the normal is produced over a week (Feb 1 to Feb 8) points to the attack continuing over several incidents. This report attempts to figure out whether these separate attacks are related and display attack characteristics and makes assumptions about its purpose and origin.
February 06, 2016 Attack profile
This incident lasted 1h 11min and was the most intensive attack during this period, in terms of hits per minute.
Incident statistics
Here are listed part of the incident statistics that we get from the deflect-labs system. They show the intensity of the attack, the type of the attack (GET/POST/Wordpress/other), targeted URLs, as well a number of GEOIP and IP information related to the attacker(s):
- client_request host:”www.kotsubynske.com.ua”
- Hits between 24000 and 72000 per minute
- Total hits for the attack period: 1643581
- Attack Start: 2016-02-06 13:34:00
- Attack Stop: 2016-02-06 14:45:00
- Type of attack: GET attack (bots requested page from website)
- Targeted URL: www.kotsubynske.com.ua
- Primary botnet request: “http://www.kotsubynske.com.ua/-”
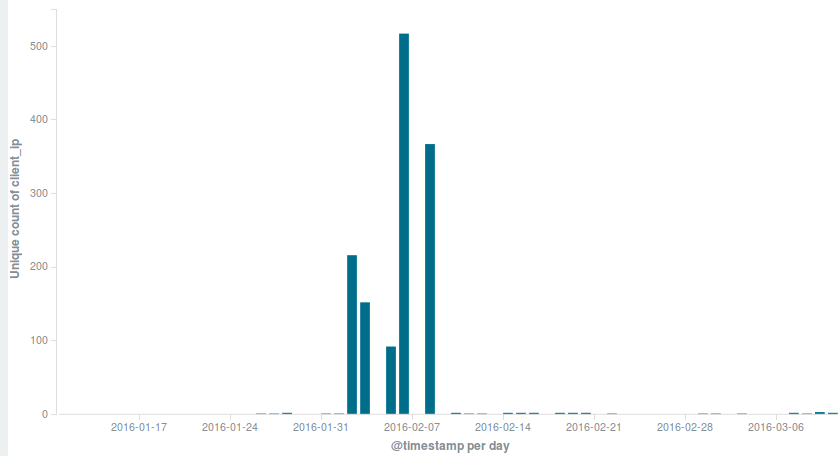
The majority of hits on this website came from Vietnam, Ukraine, India, Rep of Korea, Brazil, Pakistan. Herewith are the stats for the top five countries starting with the most counts and descending:
| geoip.country_name | Count |
| Vietnam | 817,602 |
| Ukraine | 216,216 |
| India | 121,405 |
| Romania | 70,697 |
| Pakistan | 61,201 |
Cross-incident analysis
We’ve researched three months of incidents on the Kotsubynske website, namely from January to March 2016. We have detected five incidents between February 01 – 08 and present a detailed analysis of botnet characteristics and the similarities between each incident. The point is to figure out if the incidents are related. This may help us define whether the actors behind this attack were common between all incidents. For example, we see relatively few IPs appearing in more than one incident, while each incident shares a similar botnet size and attack pattern.
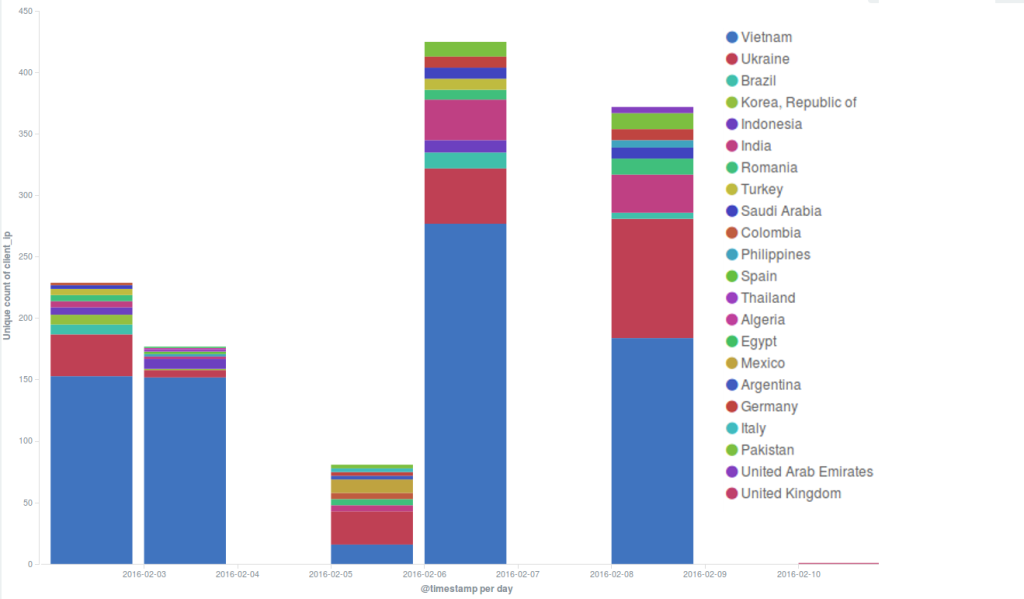
Table 1. Identical IPs across all the incidents
We identify, in sequence of incidents, botnets IPs which re-appeared from a previous attack.
| ID | Incident start | Incident end | Duration | botnet IPs | Recurring botnet IPs | Attack type | Attack pattern (URL request) |
| 1 | 2016-02-02 12:0700 | 2016-02-02 12:21:00 | 14 min | 224 | – | GET | 163224 hits: /- |
| 2 | 2016-03-02 08:27:00 | 2016-03-02 08:31:00 | 4 min | 120 | 22 | GET | 35991 hits: /- |
| 3 | 2016-05-02 21:10:00 | 2016-05-02 22:00:00 | 50 min | 99 | 0 | GET | 49197 hits : /- 23 hits: /wp-admin/admin-ajax.php |
| 4 | 2016-06-02 13:34:00 | 2016-06-02 14:45:00 | 1h 11 min | 484 | 0 | GET | 1557318 hits: /- |
| 5 | 2016-08-02 12:20:00 | 2016-08-02 16:40:00 | 4 h 20 min | 361 | 0 | GET | 392658 hits: /- |
Table 2. Pairs of incidents with significant numbers of identical IPs banned by Deflect
Here we correlate each incident against all other incidents to see whether any common botnet IPs reappear and present the incident pairs where there is a match
| incident id | banned IPs | incident id | banned IPs | recurring IPs | % of recurring botnet IPs in the smaller incident |
| 1 | 224 | 2 | 120 | 22 | 18.3% |
| 3 | 99 | 4 | 484 | 15 | 15.2% |
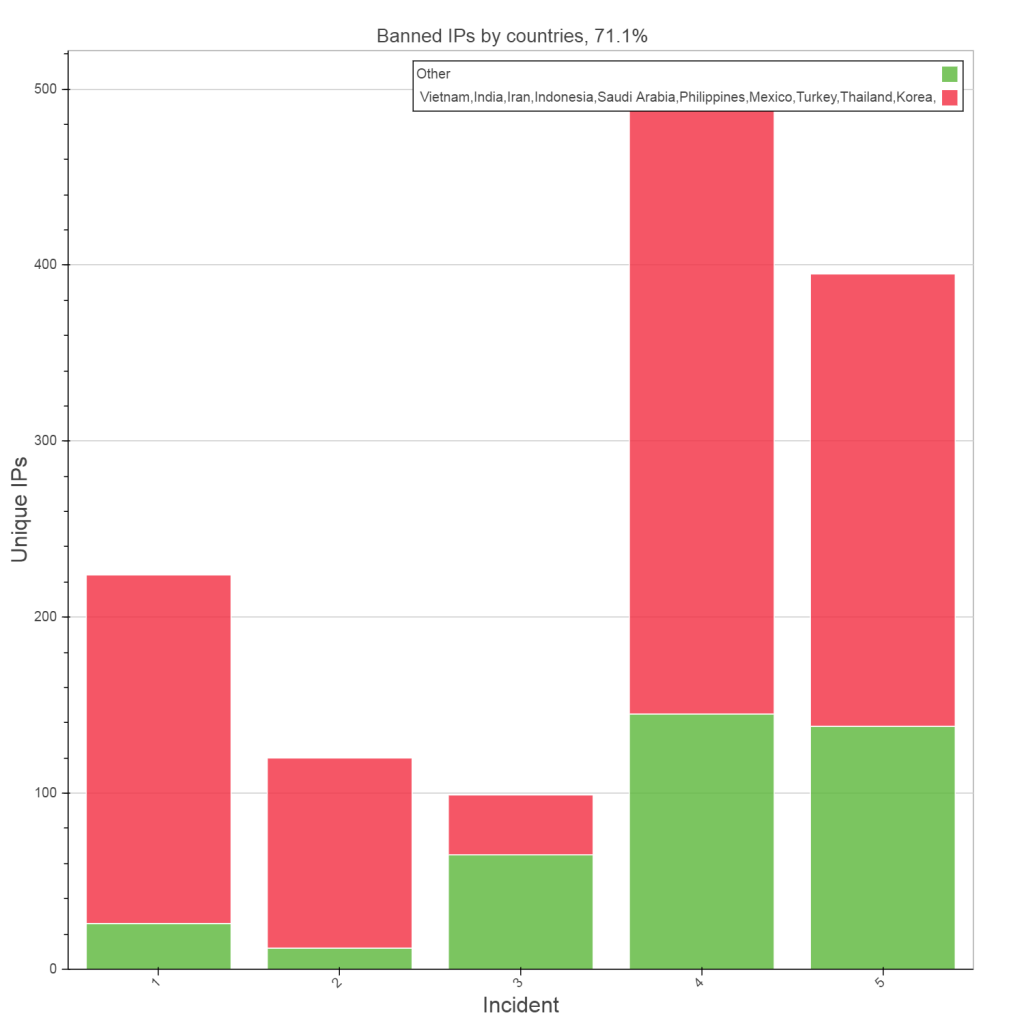
Analysis of the five attacks shows thats very few botnet IPs were reused in subsequent attacks. The presence of any recurring IPs however suggests that they either belong to a subnet of the same botnet or are victims whose computers have been infected by more than one botnet malware. Furthermore, each botnet’s geoIP characteristics and behaviour is almost identical. For example, whilst traffic during this period followed the normal trend, both in terms of number of visitors and their geographic distribution, banned IPs were primarily from Vietnam, India, Pakistan and other countries that do not normally access kotsubynske.com.ua
This is a reliable indicator of malicious traffic and a transnational botnet.
- 71.1% of banned IPs come from Vietnam, India, Iran, Pakistan, Indonesia,Saudi Arabia, Philippines, Mexico, Turkey, South Korea.
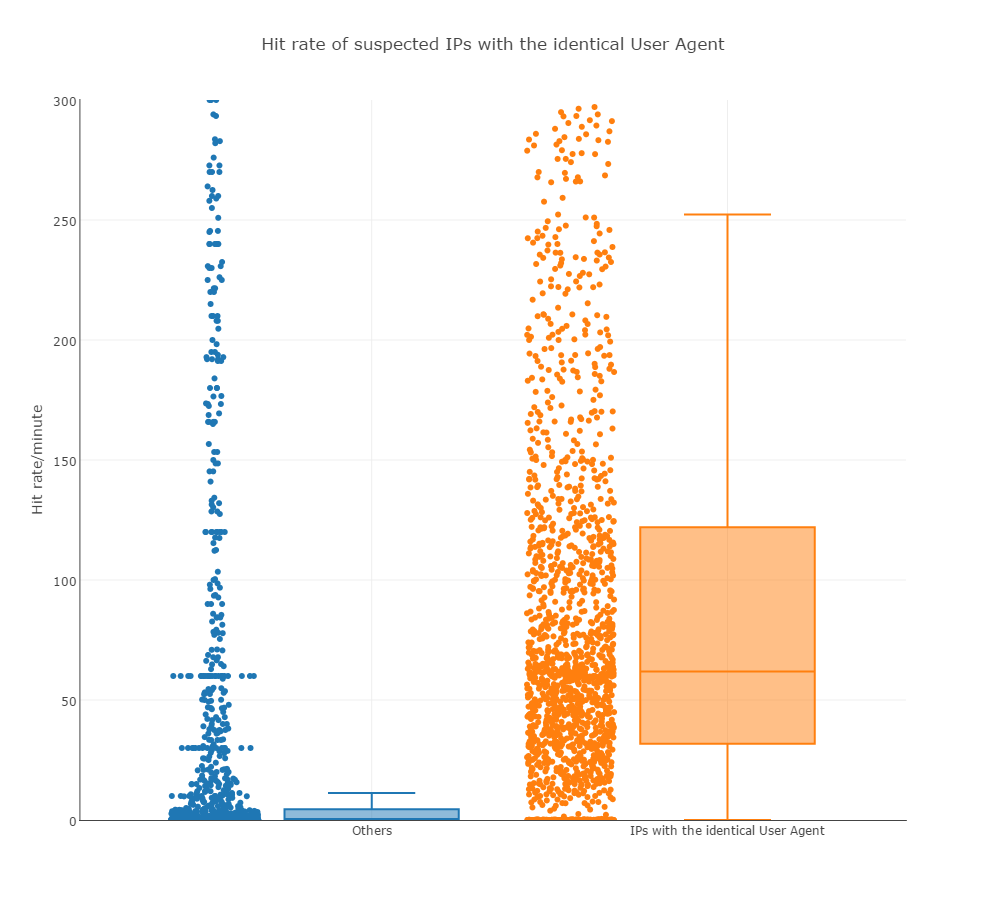
- 99.9% of banned IPs have identical user agent string: “Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0)”.
- The average hit rate of IPs with the exact identical user agent string is significantly higher: 61.9 hits/minute vs 4.5 hits/minute for all other traffic.
The user agent (UA) string seems to be identical in all five incidents, when comparing banned and legitimate traffic. In the diagram below, Orange represents the identical user agent string, whilst blue represents IPs with other user agent strings. The coloured boxes contain 50% of IPs in the middle of each set and the lines inside the boxes indicates the medians. The markers above and below the boxes indicate the position of the last IP inside 1.5 height of the box (or inside 1.5 inter quartile range).
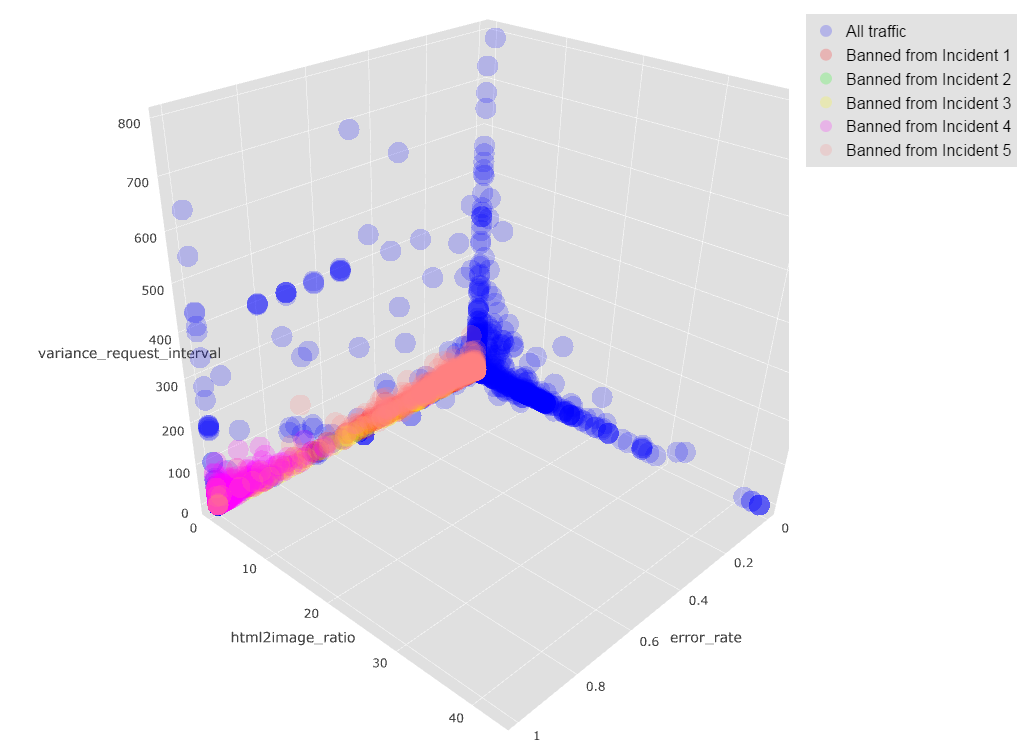
Even though there are not many identical botnet IPs across all of the 5 incidents, the behaviour of botnet IPs from different incidents is very similar. The figure below illustrates some characteristics of the botnet (different colours) in comparing with regular traffic (blue colour).
Scatter plot of sessions in 3-dimensional space:
- Request interval variance
- Error rate
- HTML to image ratio
Report Conclusion
On the 2nd of February, the Kotsubynske website published an article from a meeting of the regional administrative council where it stated that members of the political party ‘New Faces’ were interfering with and trying to sabotage the council’s work on stopping deforestation. The party is headed by the mayor of the nearby town Irpin. Attacks against the website begin thereafter.
Considering the scale of attacks often witnessed on the Deflect network, this was neither strong nor sophisticated. Our assumption is that the botnet controller was simply cycling through the various bots (IPs) available to them so as to avoid our detection and banning mechanisms. The identical user agent and attack pattern used throughout the five attacks is an indication to us that a single entity was orchestrating them.
This is the first report of the Deflect Labs initiative. Our aim is to strip away the impunity currently enjoyed by botnet operators the world over and to aid advocacy efforts of our clients. In the near future we will begin profiling and correlating present-day attacks with our three year back log and with the efforts of similarly minded DDoS mitigation efforts.