Blog
-

Outcomes from the Canadian Digital Resilience forum
On May 21st, eQualitie and partners hosted the inaugural forum on Canadian Digital Resilience, convening government, industry and academia in…
-

Digital Resilience Forum
Digital Resilience Forum Canadian Leadership in Internet Freedom and Cybersecurity Date: May 21stTime: 12:30 – 17:00 Location: Global Centre for…
-

Ukraine Deserves to Win. Nobel Peace Prize Laureates To Send a Powerful Message to the US Government
From July 25 to 28, 2023, a delegation of the 2022 Nobel Peace Prize laureates from Ukraine, Belarus, and Russia…
-
Launching the Ukrainian digital security helpline – Nadiyno
On 8th of November 2022, eQualitie and Internews Ukraine are launching nadiyno.org – the first national digital security helpline in…
-
eQualitie launches CENO, world’s first decentralized p2p mobile browser
CENO Browser lets anyone access and share information in areas with censored communications Montreal, May 10, 2022 – eQualitie, developer…
-

IGF 2024 in Montreal
Join eQualitie in encouraging the government of Canada to invite the IGF Secretariat to Montreal in 2024.
-
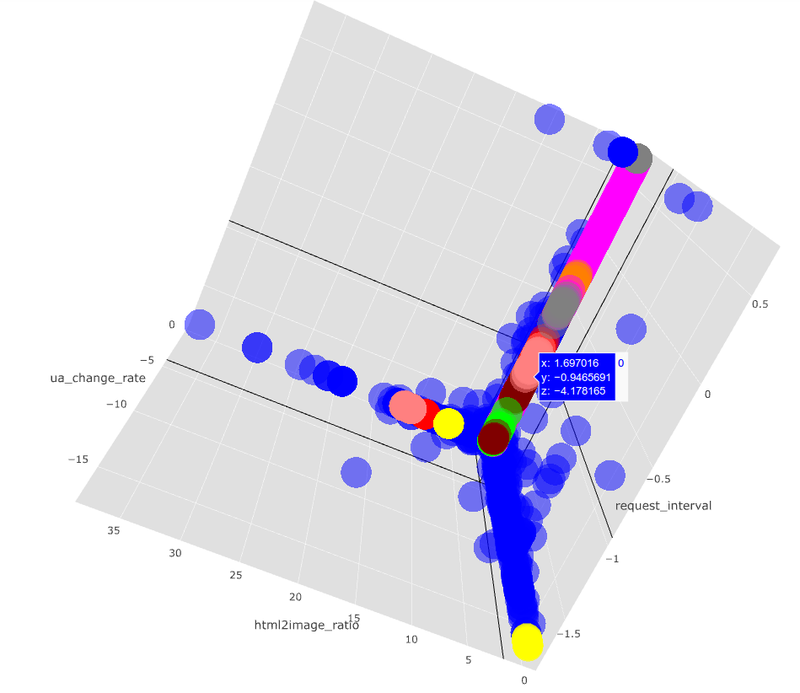
Distributed Deflect – project review
This is the fifth year of Deflect operations and an opportune time to draw some conclusions from the past and…