Botnet attack analysis of Deflect protected website blacklivesmatter.com
Seamus Tuohy and eQualit.ie
View the report with 3D rendering (5mb)
This report covers attacks between April 29th and October 15th, 2016. Over this seven-month period, we recorded more than a hundred separate denial-of-service incidents against the official Black Lives Matter website. Our analysis shows a variety of technical methods used in attempts to bring down this website and the characterization of these attacks point to a “mob” mentality of malicious actors jumping on board in response to callouts made on social media and covert channels. Our reporting highlights the usage of no-questions-asked-hosting and booter services used by malicious actors to carry out these attacks. We describe the ever growing trend of Internet vandals who, searching for a little bit of infamy, launch denial-of-service attacks against the Black Lives Matter (BLM) website. Our analysis documented attacks that could be accomplished for as little as $1 and, with access to public documentation and malicious software within easy reach, only required basic technical skill. Some of the larger attacks against BLM generated millions of connections without relying on huge infrastructure. Instead, traffic was “reflected” from legitimate WordPress and Joomla sites. We compare public attribution for some of the attacks with the data coming through our networks, and present the involvement of purported members of the Ghost Squad Hackers crew in these events.
Contents:
Introduction
“Black Lives Matter, a May First/People Link member that is supported by the Design Action Collective, is a central organization in the response movement against police abuse, brutality and misconduct.” The BLM website has been protected by Deflect since April 15th, 2016, following a spate of DDoS and hacking attacks.
In early July we published a prima facie bulletin expecting to write a comprehensive report of the attacks soon after. Since then the BLM website faced an increasing number of sizable attacks that we decided to include in our analysis and delayed publication. This report will explore these attacks, correlating open source research and publicly stated attribution with what we saw in the data.
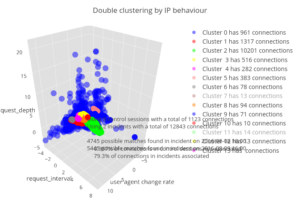
The Deflect Labs infrastructure allows us to capture, process and profile each attack, analyzing unique incidents and intersecting findings with a database of profiled botnets. We define the parameters for anomalous behavior on the network and then group (“cluster”) malicious IPs into botnets using unsupervised machine learning algorithms.
Attacks & attribution
As a DDoS mitigation solution for blacklivesmatter.com, Deflect has access to all legitimate and malicious requests made to this website. However in almost all cases, attacks come via infected machines or as reflection attacks from unsuspecting websites. A semi-experienced attacker knows how to obfuscate and disguise their traces on the Internet. It is therefore incredibly difficult to attribute an action to a particular person or IP address with confidence. We rely on our analytic tooling, peers in the mitigation industry and social media research to test our hypotheses. Assumptions arising out of OSINT are then verified against the data on our systems and vice versa.
Technical analysis and social media research indicated that actions against the BLM website were launched by multiple attackers frequently acting in concert. Some methods, like Joomla & WordPress reflection attacks, appear to have been coordinated, whilst in other cases it was clear that many actors jumped on the bandwagon of a more powerful attack to claim some of the credit. These small, loosely organized mobs appear minutes to hours after the start of the original attack and lob a hodge-podge of various attack methods, often to no effect. These actions are often accompanied by a flurry of queries from various website downtime monitoring solutions, as attackers try to collect trophies for their participation in the mob. Furthermore, we noticed a sophisticated actor who was able to generate malicious traffic on a level beyond anyone else that we documented targeting BLM. Using bulletproof hosting to coordinate their attacks, they did not go to great lengths to obfuscate their identity, creating instead a complicated web of social media accounts, possibly fake public attribution claims, and general intrigue about their motivations and purpose.
The ‘Ghost Squad’
The first, and only, publicly attributed attacks began in late April, as _s1ege, a professed member of the Ghost Squad Hackers crew, began tweeting screenshots showing site defacement and reports from website up-time checkers that the BLM site was no longer reachable. The action was part of #OPAllLivesMatter, likely in response to the #AllLivesMatter slogan (and then hashtag) created in 2015. On May 2nd, 2016, a YouTube video uploaded by @anonymous_exposes_racism contained a warning from a group identifying themselves as Anonymous to leaders of the Black Lives Matter movement, asking them to also denounce anti-white racism.
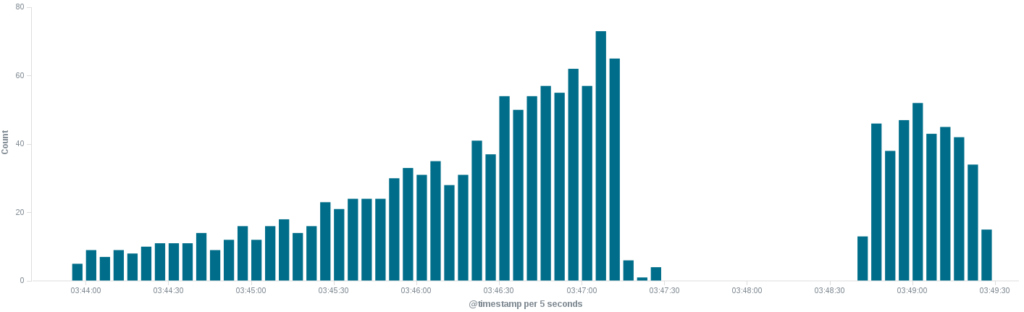
This first set of attacks against BLM, beginning on April 29th, lasted a mere 30 minutes. They came from six IP addresses and generated a little under 15,000 connections. A single method of attack and very few resources were brought into play, making this small action only temporarily effective at best. That evening five different IP addresses conducted another attack against the BLM website that topped off at over 158,000 connections over a period of an hour.
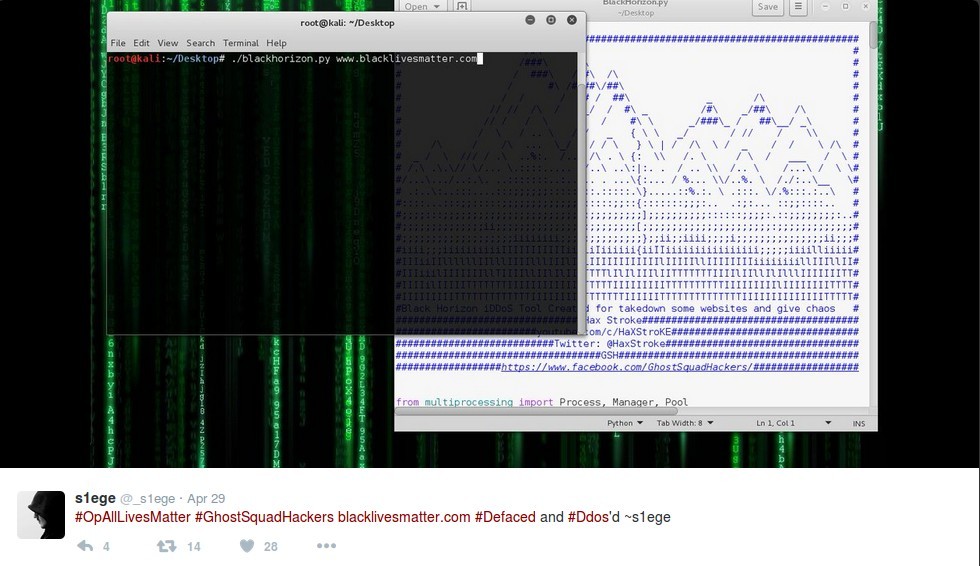
During this attack @_s1ege posted Twitter comments taking credit. Alongside photos that showed the Black Lives Matter website had been temporarily taken down by this attack, _s1ege posted a photo of the software he was using, “BlackHorizon”.

During this attack @_s1ege posted Twitter comments taking credit. Alongside photos that showed the Black Lives Matter website had been temporarily taken down by this attack, _s1ege posted a photo of the software he was using, “BlackHorizon”.
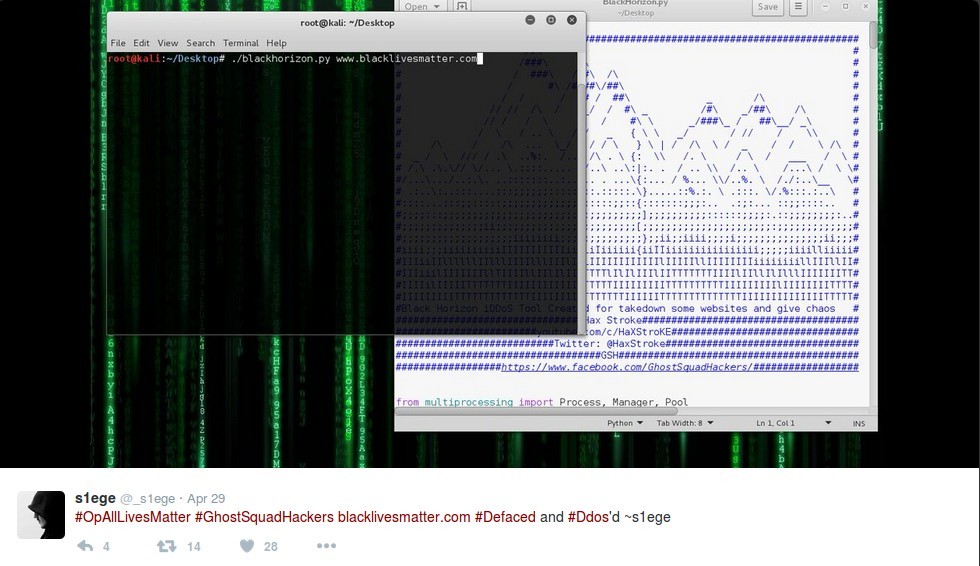 BlackHorizon is a clone of a piece of HTTP DoS software called GoldenEye, which was written by Jan Seidl in 2014. It was itself an expansion on the 2012 HULK project by Barry Shteiman. Unlike Seidl’s thoughtful adaptation and expansion of HULK, the BlackHorizon codebase mainly changes the ASCII art and the author’s name. When examined, it was clear that the functional components of the code were almost entirely unaltered from GoldenEye.
BlackHorizon is a clone of a piece of HTTP DoS software called GoldenEye, which was written by Jan Seidl in 2014. It was itself an expansion on the 2012 HULK project by Barry Shteiman. Unlike Seidl’s thoughtful adaptation and expansion of HULK, the BlackHorizon codebase mainly changes the ASCII art and the author’s name. When examined, it was clear that the functional components of the code were almost entirely unaltered from GoldenEye.
Several media publications rushed to interview _s1ege, with the @ghostsquadhack Twitter and GhostSquadHackers Facebook account referencing these publications. Around 30 minutes after the second attack Waqas Amir published an article on HackRead describing both incidents alongside his conversation with a GSH member. Later that evening one member of the GSH came back reusing an earlier bot and creating an attack that generated well under 700 connections, before giving up after less than 20 minutes.
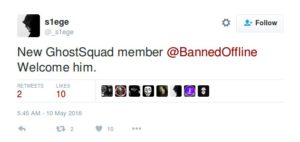
Shortly after the tweets and HackRead publication, we witnessed an increase in attack frequency and variety. Only a portion of these had a similar behavioral profile on the network to those attributed by _s1ege to GSH. The attackers were using well-known software and may have called out to others on the Internet to follow suit. On May 10th, @_s1ege announces @bannedoffline as a new member in the Ghost Squad crew and two days later stops tweeting from this account altogether.
Maskirovka
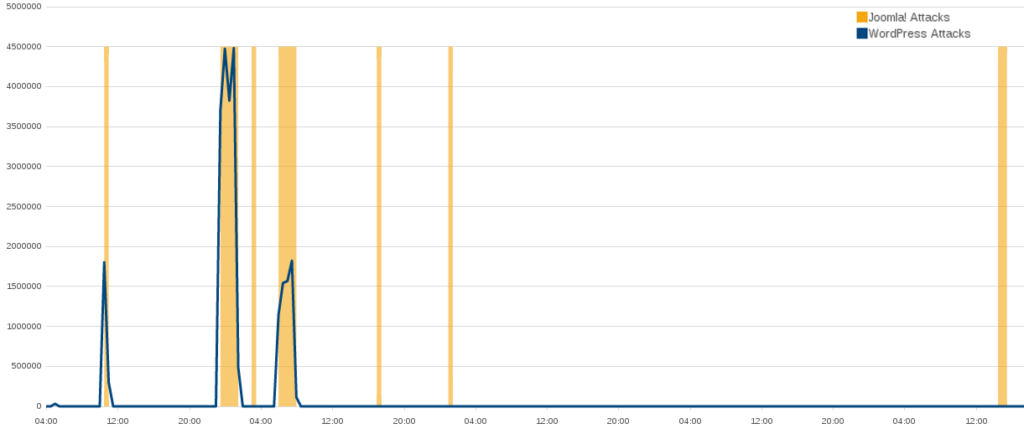
BLM began to face larger scale attacks on May 9th. The first one lasted a little over 90 minutes and consisted of 1,022,981 connections from legitimate WordPress websites. This was not the first WordPress pingback attack against the BLM website, but it was an indication that we were beginning to face adversaries prepared to deploy much greater resources than before.The level of severity and aggression continued to mount and on July 9th we witnessed a WordPress pingback attack that generated over 34 million connections to BLM in a single day. The attackers did not seem to be interested in obfuscating their provenance, allowing us to track these activities over the next few months. The attacks were coordinated from machines hosted at a “bulletproof” provider – so called because they offer servers for rent on a no-questions-asked basis. The incidents associated with these attacks were the largest faced by BLM during the reporting period.
On July 25th we received a subscription for Deflect protection from a “John Smith” asking us to enlist http://ghostsquadhackers.org. We traced this request and further conversation with this user to @bannedoffline on Twitter and Facebook, as well as the owner of the following domains: ghostantiddos.com; ghostsquadsecurity.com; bannedoffline.xyz; www.btcsetmefree.org, among others.
Our analysis of actions run from the “bulletproof” hosting provider identified several IP addresses that were used for command and control. These addresses were correlated by a peer mitigation provider who had dared @bannedoffline on a hackers forum to DDoS them and recorded the resulting activity. Two IP addresses, one belonging to the DMZhosting provider mentioned further on in this report and a Digital Ocean machine, were identified in our individual records – and correlated to eight separate incidents in our study.
- 191.96.249.80 Dmzhost Limited https://dmzhost.co
- 178.62.152.134 DigitalOcean https://www.digitalocean.com
It is hard to say with any certainty why there were no more public attributions for attacks on BLM after the first week of May, considering that the severity and sophistication increased several-fold. @bannedoffline deleted all of their social media postings in late September, just before we recorded the biggest attack against the BLM website. bannedoffline was also linked to a 665gbps attack (the largest attack of its time, before the Mirai botnets) against the Krebs on Security website. The Ghost Squad did not attribute or deny @bannedoffline’s continued participation in their crew. Attacks attributable to bannedoffline and _s1ege, who could very well be the same person, made up less than 20% of recorded DDoS activity against BLM.
Technical Analysis Of Attacks
Incidents using a similar attack method were distinguished through an iterative process of identifying possible behavioral characteristics that distinguish one type of attack from others. First we identified combinations of behaviors and features that distinguished possible attacks from normal traffic. These profiles were then matched to existing types of attacks by looking for signatures from other reports and known codebases of these attacks to create an attack method profile. At this point secondary characteristics of the attack were examined to see if they distinguished individual attacks. This ranged from the hosting provider used for botherders, to the collection of innocent websites used as reflectors, and the methods used to check the status of the website, among others. If one or more of these characteristics overlapped for a specific set of attacks, those attacks were flagged for further investigation. Once we clustered these attacks, we looked across the entire set of attacks and attempted to reject any characteristic that could clearly differentiate that subset of attacks from similar attacks.
The most common category of attacks against the BLM website has been “application level” (layer 7) HTTP flood attacks. These bots mimic human behavior by connecting to a website and requesting a large amount of content until the server crashes for lack of resources. In this report we will only be looking at this type of attacks.
The capability of individual attackers has ranged greatly. As the BLM website faced more resourced and effective attackers, the mob became a persistent background noise.
| Attack type (including variants and clones) | April | May | June | July | Aug | Sept | Oct |
| WordPress pingback | 5 | 6 | 4 | 4 | 5 | ||
| Joomla pingback | 1 | 6 | 6 | 4 | 3 | 3 | |
| Slow Loris | 2 | 5 | 3 | 1 | |||
| Fully Randomized NoCache Flood | 6 | 14 | 11 | 5 | 7 | 2 | 4 |
| Cache Bypass flood | 1 | 1 | 2 | 2 | |||
| Python script flood | 2 | 2 |
You can view the entire attack portfolio on Google Docs
Slowloris
| Aliases/Tools | Slowloris, Pyloris, Torloris |
| Attack Type | Layer 7 Denial of Service |
| Exploits | Connection exhaustion |
| Obfuscation | None |
| Attack Class | Single-source |
| Attack Rate | Low |
The first attack identified against the Black Lives Matters website occurred on April 18th, just a few days after it had switched over to Deflect. A single address made between 5 and 30 connections per second to the main BLM web page. This lasted for 28 seconds. In total it made only 168 connections. Usually, this type of behavior would not raise any flags. But in this case, the user agent of this client matched the user agent used in the original proof of concept code for “Slowloris – the low bandwidth, yet greedy and poisonous HTTP client!”
 Slowloris is a DoS tool that was originally released in 2009. It is unique among the other Layer 7 attacks we will be discussing in this report because it does not focus on flooding the network with traffic. Instead, it attempts to use up all the connections to a web server leaving none left for legitimate users. This low number of connections allows Slowloris to attack a website without drawing the same attention that a flood of traffic would. There have been 12 identified attacks using the original Slowloris codebase since the BLM website has been protected by Deflect. All but one of these attacks were under 1000 connections. The largest Slowloris attack occurred on July 10th from 0:50 to 3:20 and from 6:00 to 7:20, making over 40,542 connections and clearly misusing this tool or not understanding its original purpose.
Slowloris is a DoS tool that was originally released in 2009. It is unique among the other Layer 7 attacks we will be discussing in this report because it does not focus on flooding the network with traffic. Instead, it attempts to use up all the connections to a web server leaving none left for legitimate users. This low number of connections allows Slowloris to attack a website without drawing the same attention that a flood of traffic would. There have been 12 identified attacks using the original Slowloris codebase since the BLM website has been protected by Deflect. All but one of these attacks were under 1000 connections. The largest Slowloris attack occurred on July 10th from 0:50 to 3:20 and from 6:00 to 7:20, making over 40,542 connections and clearly misusing this tool or not understanding its original purpose.
In the initial code release Slowloris used a single user agent. Today, many of the custom versions of Slowloris have changed the user agent [pyloris.py] or added source client obfuscation by randomly picking from a list of user agents [slowloris.py]. It is not surprising to see someone using an unmodified version of such an arcane tool even when the server used on the BLM website is protected against that attack. Many of the actors conducting DoS attacks are not building upon existing tools. While Slowloris was elegant at the time, the DoS space is dominated by attackers using simplistic measures. This is because one does not need a highly complex tool to take down most sites on the Internet.
Slowloris attacks on the BLM website have a tendency to overlap with or occur around the time of two low-skill “basic HTTP flood” attacks: [Blank] and [Python], as well as (Blank+WordPress) WordPress attacks.
HTTP Floods
HTTP floods are easy to implement and hard to identify attacks. Generally, they attempt to exhaust a system’s application resources or the network bandwidth. They do this by either creating a large amount of connections to the website or by continuously downloading a large amount of files. Because they only require an attacker to create many legitimate connections to a server, HTTP floods are quite easy to implement. Since these connections are legitimate, it can be very difficult for a defender to differentiate these connections from those of real users.
Simple HTTP Flood
| Aliases/Tools | None |
| Attack Type | Layer 7 Denial of Service |
| Exploits | None |
| Obfuscation | None |
| Attack Class | Single-source |
| Attack Rate | Low |
A simple example of this type of attack can be seen on April 30th. For just under ten minutes one lone address conducted a low sophistication HTTP GET request attack against the Black Lives Matter website. Over a five-minute period this attacker made 1503 connections from a single address using an Internet Explorer user agent. The BLM website only received a few of these connections as the attacker was banned within a second.
Basic Python
| Aliases/Tools | None |
| Attack Type | Layer 7 Denial of Service |
| Exploits | None |
| Obfuscation | None |
| Attack Class | Single-source |
| Attack Rate | Low |
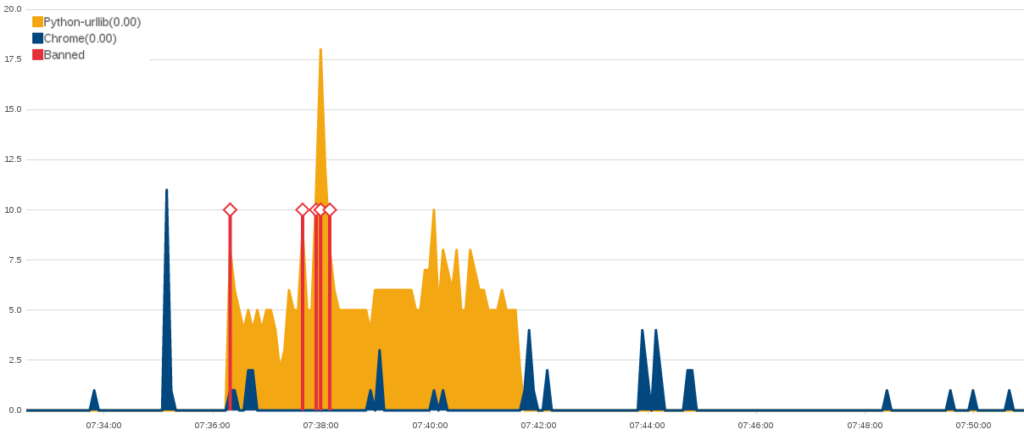
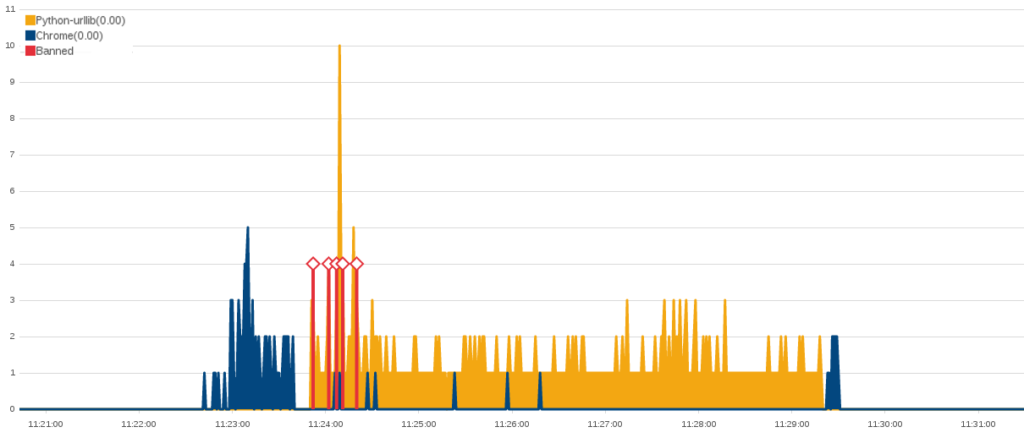
Just a few hours after the previous HTTP Flood concluded, two different attacks started and subsided. They missed each other by just two minutes. The first was a “Fully Randomized NoCache Flood” and connected 2,000 times in its two minutes of attack. The second was a test run of an even simpler HTTP Flood attack than the previous example. The code behind this attack was written without any attempt to make it look like a legitimate user. Over the six minute attack, this script made around 400 connections. There were also 23 connection from a Chrome browser at the same IP address during this period, as the attacker frantically refreshed the web page to check on their impact. As in the previous attack, it took under a second for this IP address to be banned.
While a DoS attack does not need much sophistication to be effective, we mention it here because its unique signature shows that this attack was written by an inexperienced programmer. To explain how basic this attack is, the Deflect Labs researchers have recreated a working version of it below.
import urllib
while True:
urllib.urlopen("http://www.blacklivesmatter.com")
This attacker came back again after a few hours using a different address. As in many single-source attacks, they were likely using a proxy to disguise the original IP of their attacks as they conducted these test runs. Before running the python script, they ran the same “Fully Randomized NoCache Flood” attack for about a minute and then quickly switched back to their python script. The python script made another 429 connections during the approximately six minute long attack. It was, like before, stopped within seconds.
This testing behavior continued over the next few days. With another small attack on the morning of May 1st that made up to 700 connections in just under 10 minutes and one with just over 1000 connections in just under 20 minutes. By the end of that week this attacker had concluded their experiment in attempting to build their own script. Its simple nature made it automatically blocked almost as soon as it connected. At its peak, it could only create a hundred or so connections per minute, which is far too little for a machine conducting a DoS attack.
HTTP Flood DDoS
| Aliases/Tools | None |
| Attack Type | Layer 7 Denial of Service |
| Exploits | None |
| Obfuscation | None |
| Attack Class | Multi-Source |
| Attack Rate | High |
The HTTP floods we have described so far in this section have only come from a single source. In this section we will explore how a botnet can leverage thousands of machines to conduct a distributed HTTP Flood and how we can identify these floods among regular traffic.
HTTP floods that involve many sources (DDoS attacks) are difficult to identify because they can look very similar to regular traffic. But because the BLM website, like every other, has traffic patterns that show the general behavior of their usual readership, there are some clear examples of DDoS HTTP Floods that we can explore.
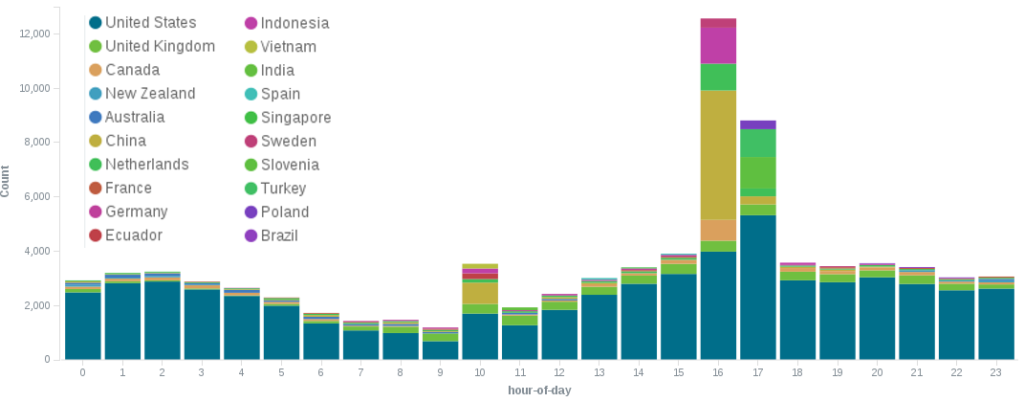
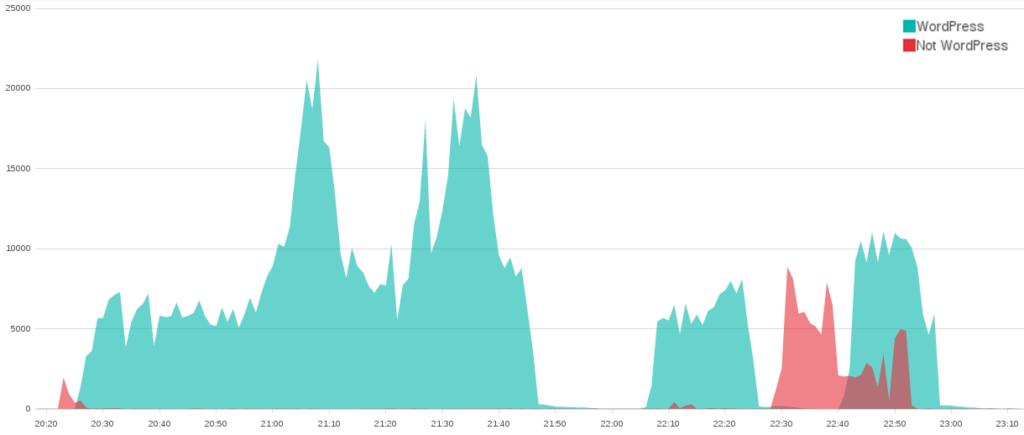
Unsurprisingly, people in the US visit the BLM website far more often than other groups. This also impacts traffic patterns to the site. Traffic to the BLM website follows a daily cyclical pattern. There is a peak in its traffic between 12:00 and 14:00 EST. (The numbers in our screenshots reflect UTC+0 timestamps.) After that, the traffic slows until around 07:00 EST, when it spikes for the evening and then slows for the night.
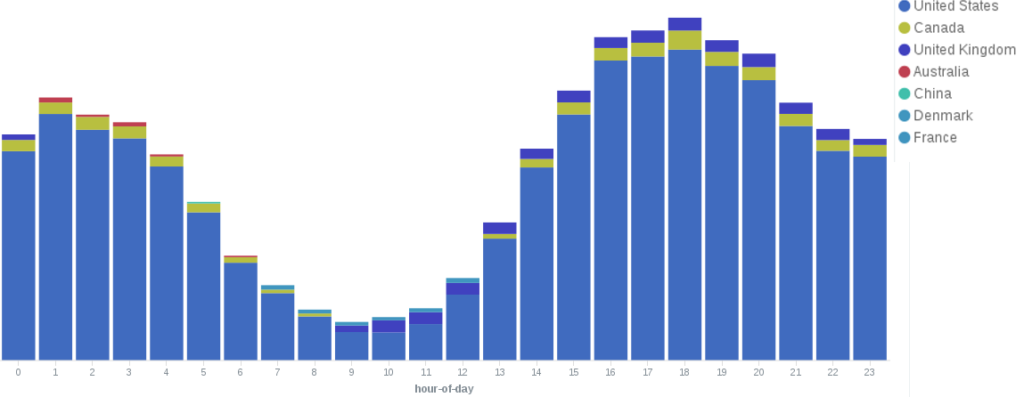 Between August 5th and August 9th the hourly pattern changed from a smooth usage pattern like the above into this.
Between August 5th and August 9th the hourly pattern changed from a smooth usage pattern like the above into this.
That week between 11:00 and 13:00 EST there was a surge of traffic from China, Indonesia, Turkey, and Slovenia. While the Deflect Labs team is not surprised that BLM receives international attention, it is a bit odd to see it occurring during the same period worldwide. When looking for HTTP Floods that have multiple sources, knowing these usage patterns can make it far easier to identify possible attacks like this one.
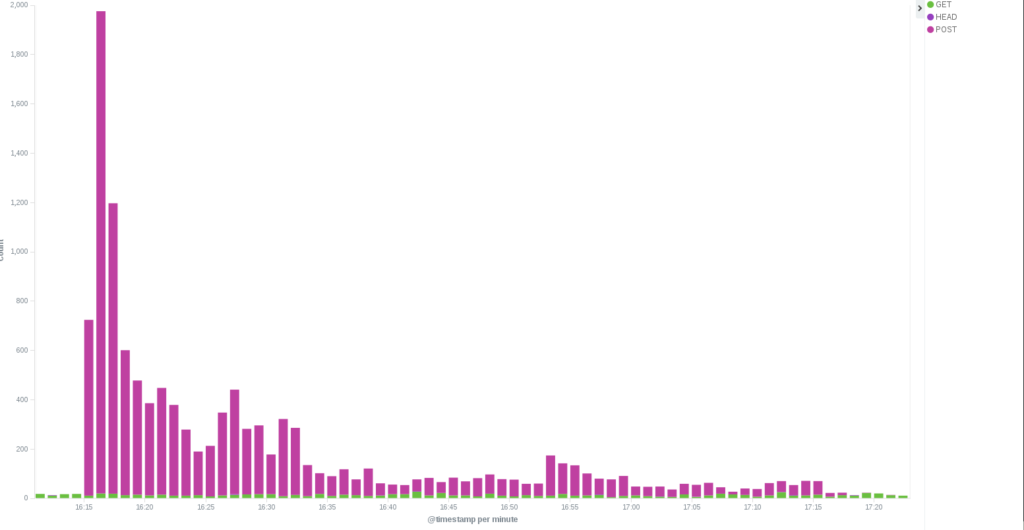
The anomaly we can see above was an HTTP POST Flood attack on August 8th. Based upon the dozens of countries per minute that are seen making higher than average connections, it seems plausible that this attack was using a botnet of infected machines.
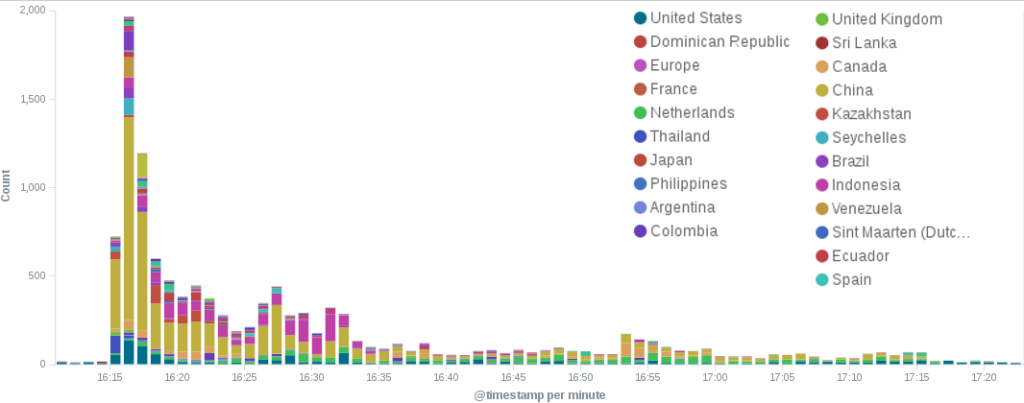 Over a period of just over an hour, 11,514 machines attempted to upload (POST) a series of large files to the BLM website. This created a flood of large content-length requests that the BLM website had to process.
Over a period of just over an hour, 11,514 machines attempted to upload (POST) a series of large files to the BLM website. This created a flood of large content-length requests that the BLM website had to process.
Fully Randomized NoCache Flood
| Aliases/Tools | Hulk, GoldenEye, BlackHorizon |
| Attack Type | Layer 7 Denial of Service |
| Exploits | KeepAlive, NoCache |
| Obfuscation | Source Client Obfuscation, Reference Forgery |
| Attack Class | Multi-Source |
| Attack Rate | High |
Websites that are protected by DDoS mitigation services – such as Deflect – use a “caching” system to store commonly requested pages and provide them to users so the protected website’s server does not have to. This “cache” of recently requested web pages allows Deflect to further limit the requests made to the protected server. Even if simple bots, like those in the last section, evade blocking, they often are just receiving responses from Deflect’s caches of recently requested URLs and not impacting the origin server at all.
DoS providers responded to the use of caching by creating a bot that tricks the cache into thinking that they are requesting a page that was never requested before. These “Cache-bypass” HTTP Floods are bots that add a randomized query at the end of their requests. These randomly generated queries cause a cache to view each request as a new request, even though the bots we are examining in this report only ever requested the main BLM URL “blacklivesmatter.com”.
GoldenEye is a Layer 7 DoS tool. It allows a single computer to open up multiple connections to a website, each of which pretends to be a different device. To do this, GoldenEye provides a different user agent string for each connection. Over the combined hour and a half of attacks, these 11 bots pretended to be hundreds of different types of users to avoid detection.
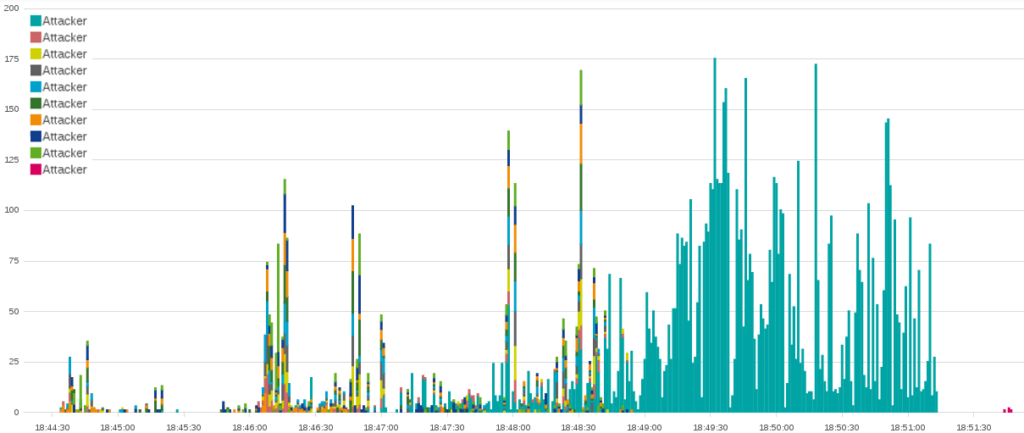
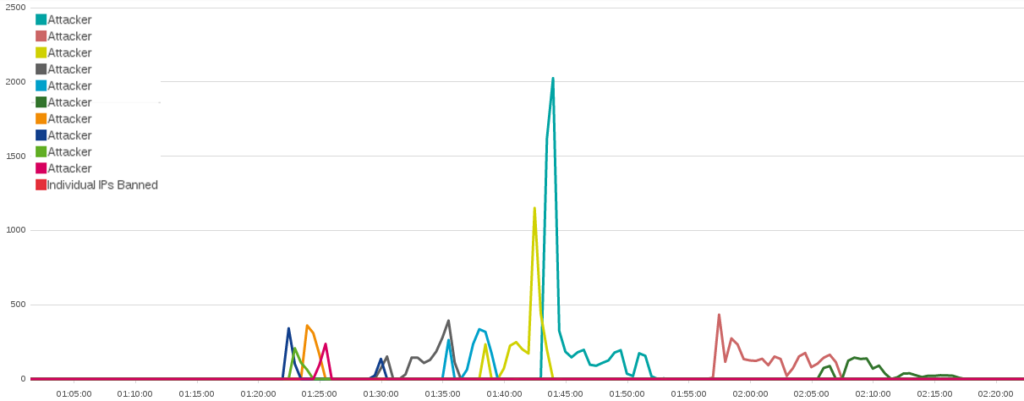
Later in the evening of April 30th another attack consisting of just under 11,000 connections was attempted. This attack used an improved “Fully Randomized NoCache Flood.” While the attack starts with 9 bots using something similar to the code used by GSH, a single address joins a minute into the attack and quickly dwarfs the other attackers in both number of connections and variety of user agents that it employs.
If it were not for the variety of intensity and method used by the individual addresses, attacks like this would look like they involved a single actor. But as is common for attacks against the BLM website, this attack starts slowly with one or two initial actors, who are then joined by a small mob of “bandwagon bullies.” As was seen in the early GSH attacks, they share the tools used in their attacks with the other attackers. Whoever this late attacker is, they are clearly not just another member of the team. This attacker has considerably different network resources and likely software that allows them to have far more impact than all the participating GSH team members.
Reflection DDoS
Joomla! Reflection DDoS
| Aliases/Tools | DAVOSET, UFONet |
| Attack Type | Layer 7 Denial of Service |
| Exploits | None |
| Obfuscation | None |
| Attack Class | Reflected |
| Attack Rate | High |
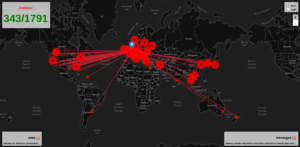 In 2013 a series of vulnerabilities were discovered in a Google Maps plugin for the Joomla! CMS. One of them made it possible for anyone to request a Joomla! site to make an HTTP request to remote websites. By June 2013 this vulnerability had already been weaponized and included in an existing DDoS framework called DAVOSET (DDoS attacks via other sites execution tool). In 2014 this same vulnerability was included in the UFOnet DDoS framework.
In 2013 a series of vulnerabilities were discovered in a Google Maps plugin for the Joomla! CMS. One of them made it possible for anyone to request a Joomla! site to make an HTTP request to remote websites. By June 2013 this vulnerability had already been weaponized and included in an existing DDoS framework called DAVOSET (DDoS attacks via other sites execution tool). In 2014 this same vulnerability was included in the UFOnet DDoS framework.
Each of these DDoS frameworks have easy-to-use web-based point-and-click interfaces and a built-in list of vulnerable Joomla! websites. This makes them ideal for a low-resourced or unsophisticated attacker looking to amplify another attack. Of the 23 WordPress attacks made against the BLM website, only 7 of them were not paired with a Joomla! attack.
Initially, it was difficult to identify Joomla! attacks because most of the connections do not provide a user agent string. Empty user agents are somewhat common on the Internet. Many non-malicious, but quickly made, bots do not provide a user agent. As such, when we initially saw these spikes of traffic, we assumed that they were from another sloppily made DoS bot.
After we saw this bot accompanying attacks from a variety of different attackers, we investigated further and noticed a fingerprint hidden in the traffic that led us to the Joomla! attack. Although most of the user agents used by Joomla! sites to make these requests are blank, a small subset of these machines include the version of PHP language that was used to run the request. While blank user agents are somewhat common, many of the attacks that included them were combined with user agents that contained PHP versions. Given the relative rarity of PHP, we realized that the odd increase in empty user agents alongside other attacks was because they were being combined with Joomla! attacks.
Introduction to WordPress XMLRPC Floods
| Aliases/Tools | WordPress Pingback |
| Attack Type | Layer 7 Denial of Service |
| Exploits | NoCache |
| Obfuscation | Spoofing |
| Attack Class | Reflected |
| Attack Rate | High |
By default, WordPress has a “pingback” feature that was built to allow WordPress sites to alert other blogs when they linked to their content. On a high level, this works similarly to a mention in Twitter. When a WordPress site publishes a post that links to another website, it sends out a “pingback” to that site with a link to the post containing the original link. If the receiving site is also based on WordPress, it responds to the original site to confirm that it received the pingback.
Pingbacks have been a part of WordPress sites since Version 1.5, which came out in 2005. It wasn’t until 2012 that Christian Mehlmauer released a working implementation of code that took advantage of this feature to ask WordPress sites to verify “pingbacks” from spoofed URLs. Two years later, in March 2014, Akamai released a post that described a “pingback” attack consisting in over 162,000 WordPress sites. In September 2015 they announced that WordPress pingback attacks made up 13% of all Layer 7 attacks they faced.
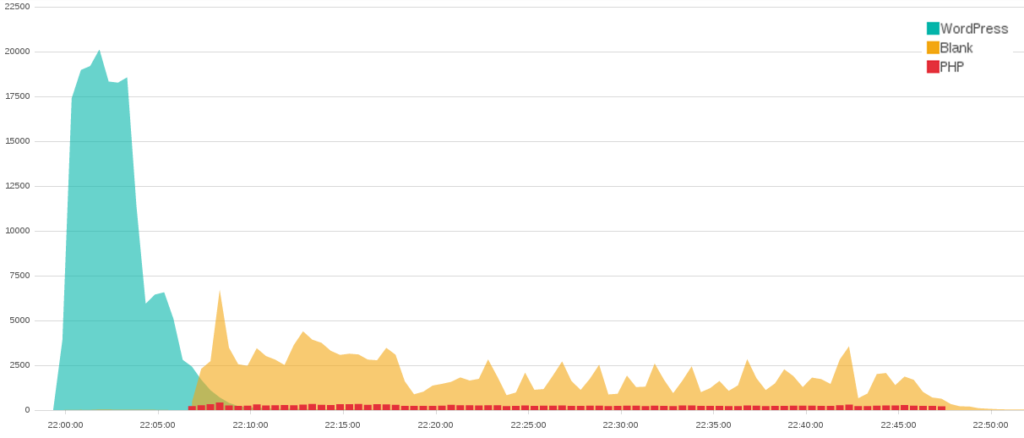
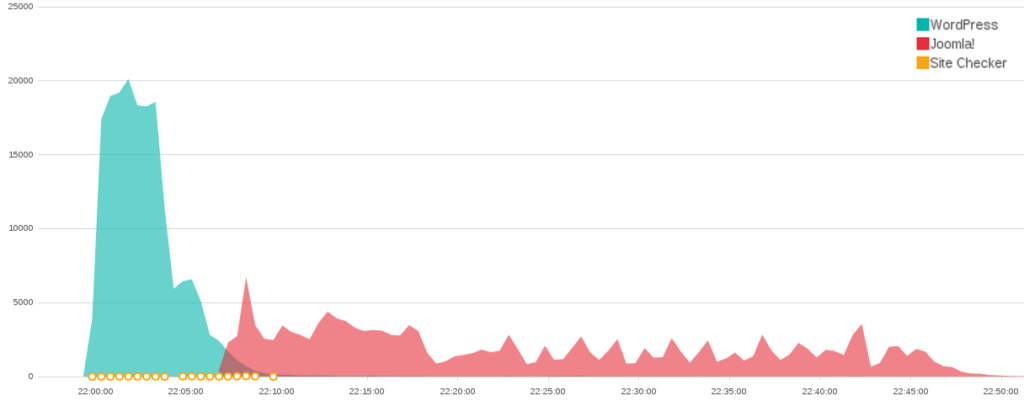
At 22:00 on May 1st a WordPress pingback attack began targeting the Black Lives Matter website. In just 13 minutes it made 181,301 connections. As this WordPress attack subsided, a Joomla! attack took its place. The moment the WordPress attack started, the second attacker began to use free online services dozens of times a minute to check if the Black Lives Matter website had gone down. As the second attack began, the attacker increased the frequency at which they monitored the state of the website. Four minutes into the attack, when it had obviously succeeded, the attacker stopped checking the site. Altogether, this attack consisted of around 350,000 connections in a period of less than an hour.
As was mentioned in the original bulletin, the most intense attacks against the Black Lives Matter website have been WordPress pingback attacks. The first large-scale attack against the BLM website was a WordPress attack on May 9th. This attack made over 1,130,000 connections in just under three hours. It was a mix of over 1,000,000 connections from a WordPress pingback attack alongside 100,000 connections from a “Fully Randomized NoCache Flood.”
The following WordPress sections will provide some illustrative examples to show how we explored the relationships between these bots. But we will not examine every attack. Nor will we try to attribute attacks to their source.
WordPress pingback & Botherder Addresses
While WordPress attacks work similarly to Joomla! attacks they are far easier to identify. These attacks clearly list their WordPress version as their user agent. Because these attacks started to become more widespread, a new feature was released in version 3.9 of WordPress. This version updated pingbacks to include the IP address that made the original pingback request.
WordPress/4.6; http://host.site.tld; verifying pingback from 127.0.0.1
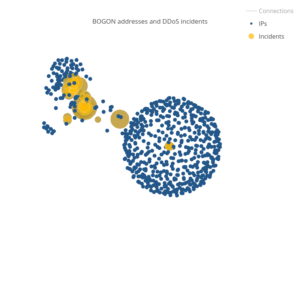
We call these IP addresses “botherder” addresses. Some of these addresses correspond to globally addressable IP addresses that one can reach over the Internet. Others are addresses that should never appear on the public Internet. These bogon addresses are private/reserved addresses and netblocks that have not been assigned to a regional Internet registry. The bogon address seen in the example above is called localhost. It’s the IP address used by a computer to refer to itself.
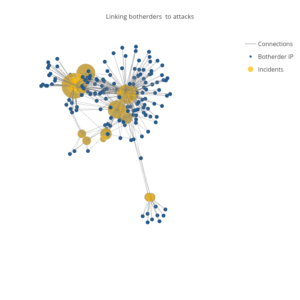
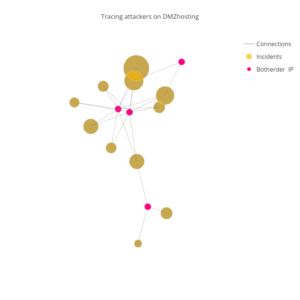
While adding the address of the botherder was implemented to de-anonymize the true source of an attack, most attackers are very adept at concealing their true IP address through the use of spoofed packets, proxies, virtual private servers (VPSs), and the use of compromised machines to conduct the original requests. When we started looking into the botherder addresses, we assumed that we would only find spoofed addresses. To our surprise, the botherder addresses exposed far more than we expected them to. By clustering the botherder IPs exposed in an attack, we were able to develop behavioral profiles that helped us link different attacks together to understand which attacks were likely conducted by the same attacker.
The first thing we looked at were the botherder IPs used in WordPress attacks against the BLM website. Our exploration of bogon addresses showed clear relationships between the attacks that could be exposed by looking at the botherder addresses.
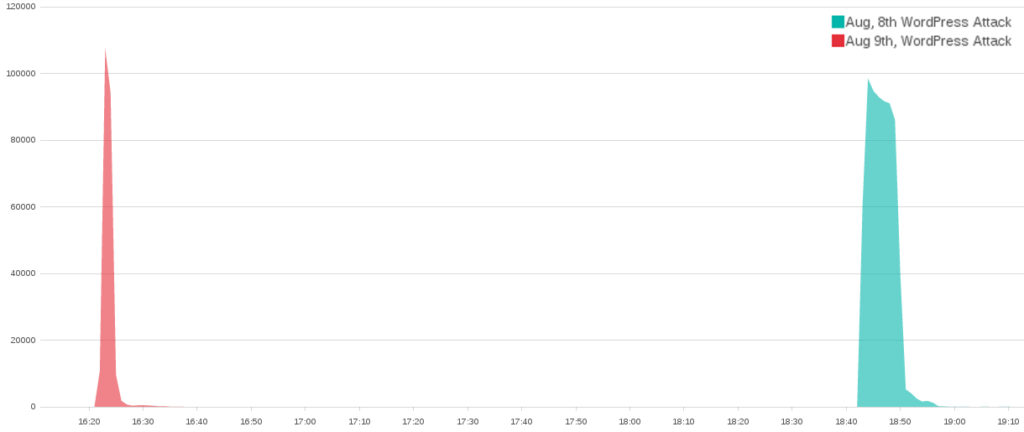
The large blue ball of shared IP addresses on the left side of the bogon graph above surrounds two small incidents that occurred on August 8th and 9th. This massive ball of shared IP addresses consists of over 500 addresses from the private IP address spaces. Specifically, they include 382 addresses from the 172.16.0.0/12 address range and 177 addresses from the 10.0.0.0/8 address range. Private address ranges are not entirely uncommon for WordPress pingback attacks. They can appear when the botherder is on the same hosting provider as the WordPress sites they are exploiting and can also be created when a botherder is spoofing random addresses. What is unusual is how clearly the overlapping bogon IP addresses link these two attacks.
There were also globally addressable botherder IP addresses that linked each of the individual attacks against BLM together. It is likely that areas of sparse overlapping IPs exist because many botherders were clearly spoofing IP addresses. But the areas with many connections showed relationships that were worth exploring.
One commonality between all the attacks was that while every attack has hundreds of spoofed botherder addresses that appear only once or twice, there are also a small number of botherder addresses that account for a majority of the bots herded for the attack. In the August 8th and 9th attacks, which can be seen at the bottom of the globally addressable IP graph, three IP addresses accounted for 95% (13,963 / 14,585) of the WordPress connections that identified a botherder.
Because Deflect’s primary purpose is DDoS mitigation, Deflect Labs’ investigations often happen days or weeks after the fact. This means that we often have to rely on our logs and open source intelligence. In this case one of the first things we looked at was who owned the three primary botherder IP addresses. These IP addresses belong to Digital Ocean, a VPS provider based in New York. Digital Ocean does not provide multiple IP addresses per machine, and so we know that this attack was herded by three separate Digital Ocean “droplets.” Hourly pricing for Digital Ocean droplets runs between $0.007 USD/hour and $0.119 USD/hour. With each of these attacks lasting under half an hour, the cost to run this attack was well below a single dollar.
“Bulletproof” Hosting
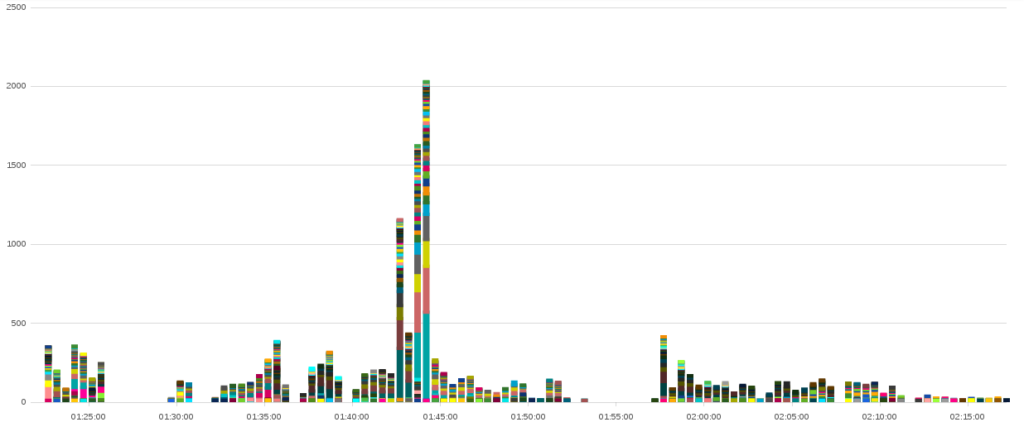
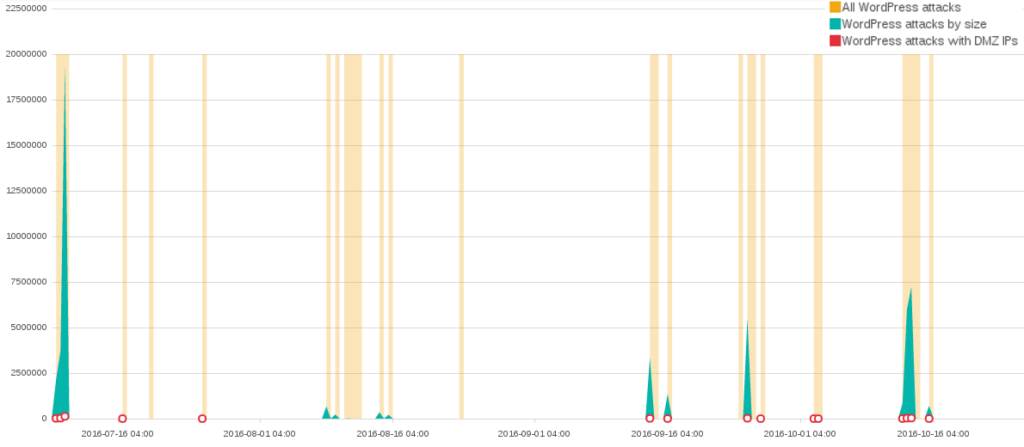
By far the largest cluster of associated WordPress attacks occurred between July and October. This set of attacks includes the five largest attacks over that four-month period.
Among the 206 globally addressable IPs used by those attacks, 5 botherder IP addresses make up 65% (41,030 / 62,488) of the botherder IPs identified in the attack. Each of these botherders were hosted on an “offshore” hosting provider called DMZHOST. The two most connected botherder IPs in our attacks are mentioned countless times on a variety of IP address reputation websites, forums, and even blog posts as the source of a variety of similar attacks.
“Bulletproof hosting” providers like DMZHOST provide VPSs that advertise themselves as outside of the reach of Western law enforcement. DMZHOST offers its clients “offshore” VPSs in a “Secured Netherland datacenter privacy bunker” and “does not store any information / Log about user activity.” At the same time, DMZHOST’s terms of service are just as concise. “DMZHOST does not allow anything (related) to the following content: – DDos – Childporn – Bank Exploit – Terrorism – NO NTP – NO Email SPAM”.
Conclusion
Silencing online voices is becoming ever easier and cheaper on the Internet. The biggest attacks presented in this report did not require expensive infrastructure, they were simply reflected from other websites to magnify their strength. We are beginning to see authorities pursue and shut down “bulletproof” hosting and booter services that enable a lot of these attacks, yet more needs to be done. In the coming age of IoT botnets, when we begin to witness attacks that can generate over a terabyte of traffic per second, the mitigation community should not guard their intelligence on malicious activity but share it, responsibly and efficiently. Deflect Labs is a small project laying the groundwork for open source community-driven intelligence on botnet classification and exposure. We encourage you to get in touch if you would like to contribute.
Deflect is a website security project working with independent media, human rights organizations and activists. It offers DDoS mitigation, secure hosting and attack analytics, free of charge to qualifying organizations. All of our tools are open source and we operate according to strict terms of service and principles promoting the privacy of our clients. Deflect is a project of eQualit.ie, a Canadian not-for-profit organization working to promote and defend human rights in the digital age.