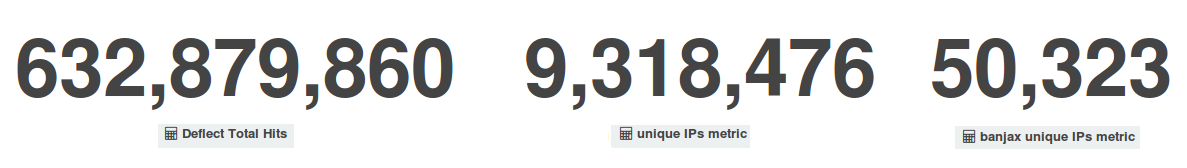
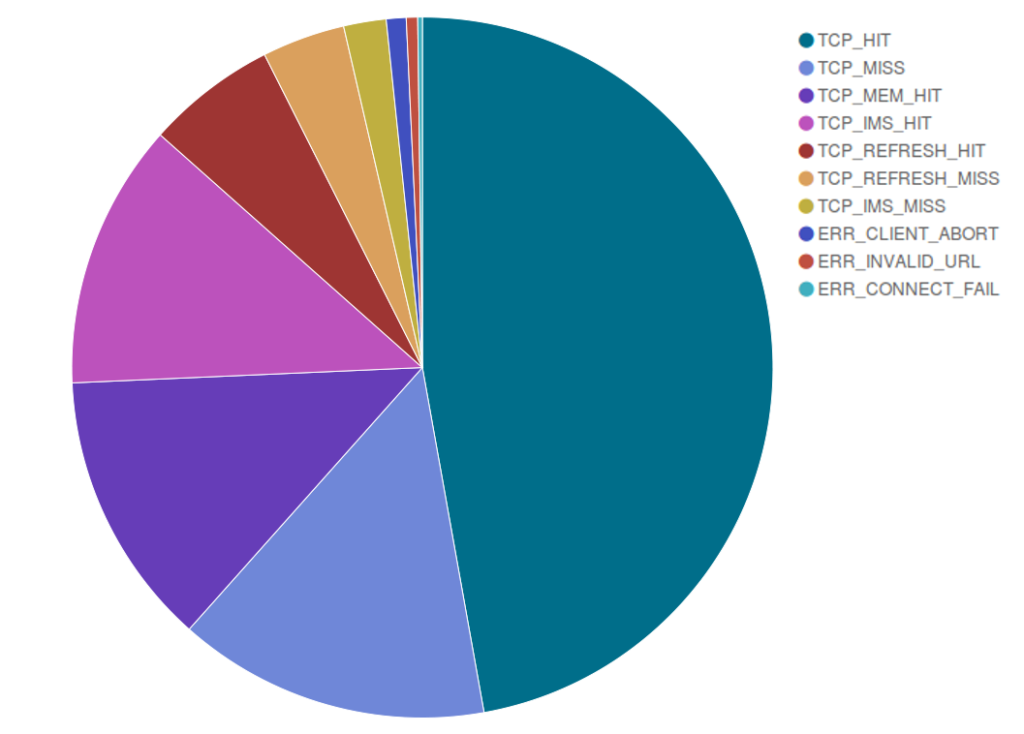
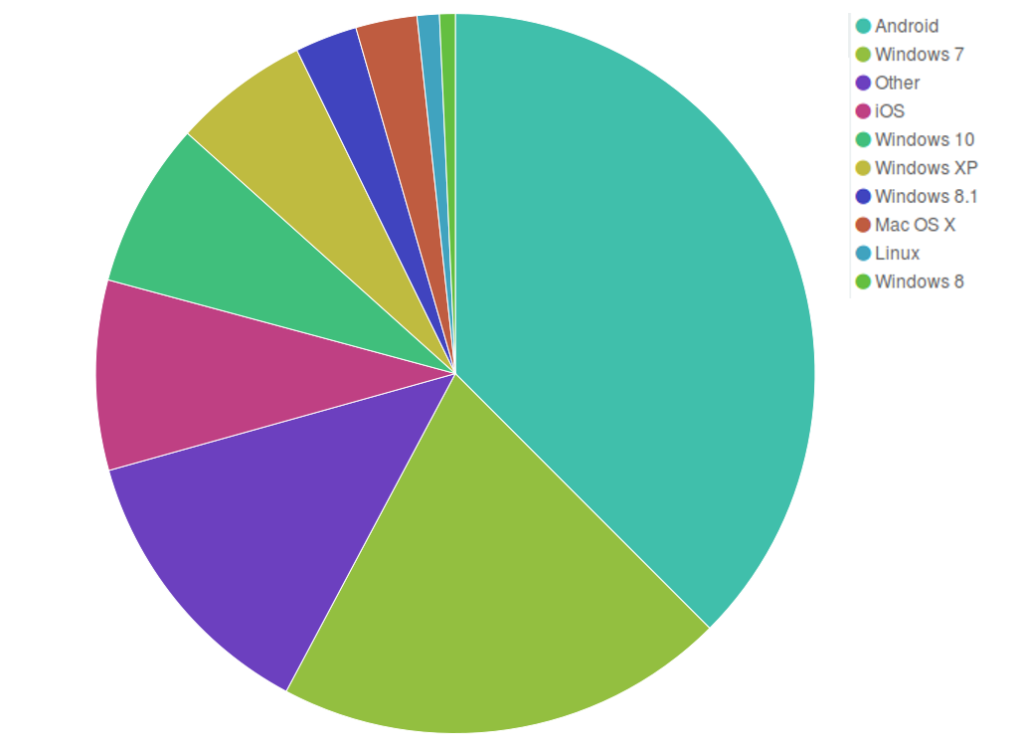
In October Deflect’s metrics kept following the trend we had seen in September, with comparable figures in terms of unique visitors (9.3 million) and a slight increase in total hits (632.8 million requests reaching our edge servers), but with almost twice as many bots identified and banned by Deflect’s banning system – 50,323 bots against 27,238 in September. This means that deflected websites attracted a lot of legitimate visitors, but that we also had to mitigate stronger DDoS attacks.
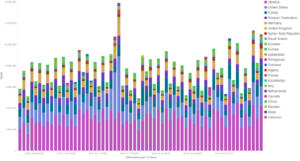
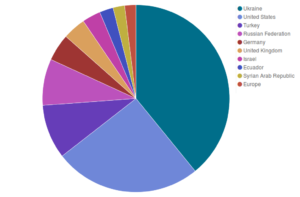
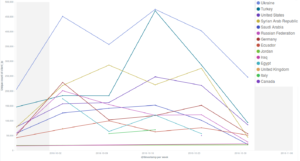
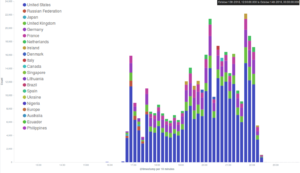
Looking at some more detailed graphs dividing Deflect’s metrics by country of origin of our visitors, we can see that while Ukraine and the United States keep topping the scores as in previous months, the peak of visits originating from Russia in August and September has been subsiding in favour of Turkey.
[one_third]
[/one_third][one_third]
[/one_third][one_third_last]
[/one_third_last]
[one_half]
[/one_half][one_half_last]
[/one_half_last]
October attacks
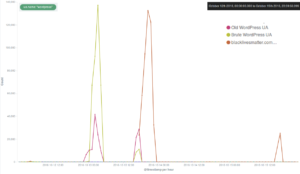
Deflect mitigated some major attacks around mid-October. Two websites were targeted in particular, and the method was most probably a common WordPress pingback reflective attack.
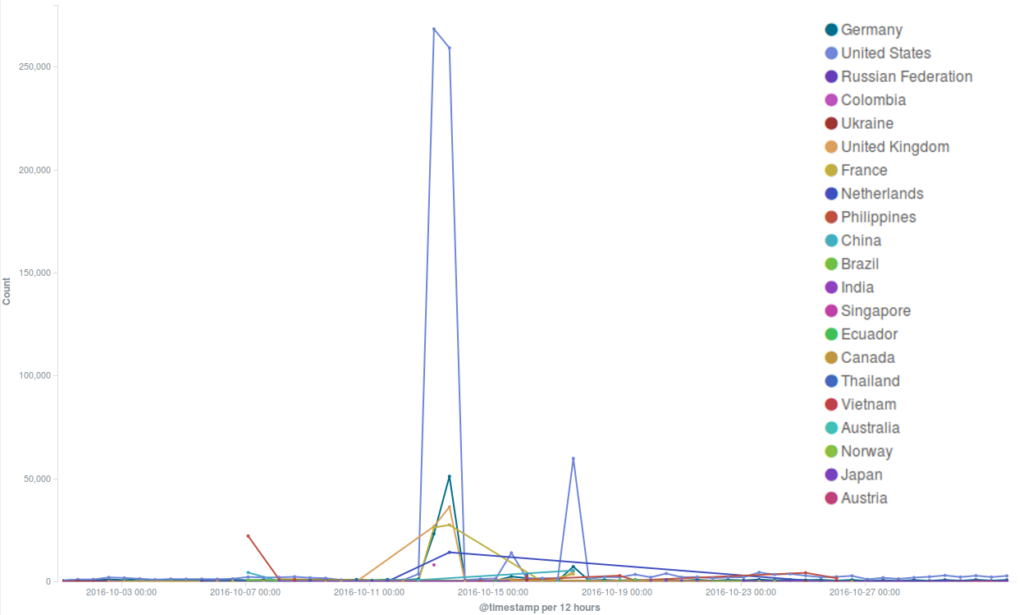
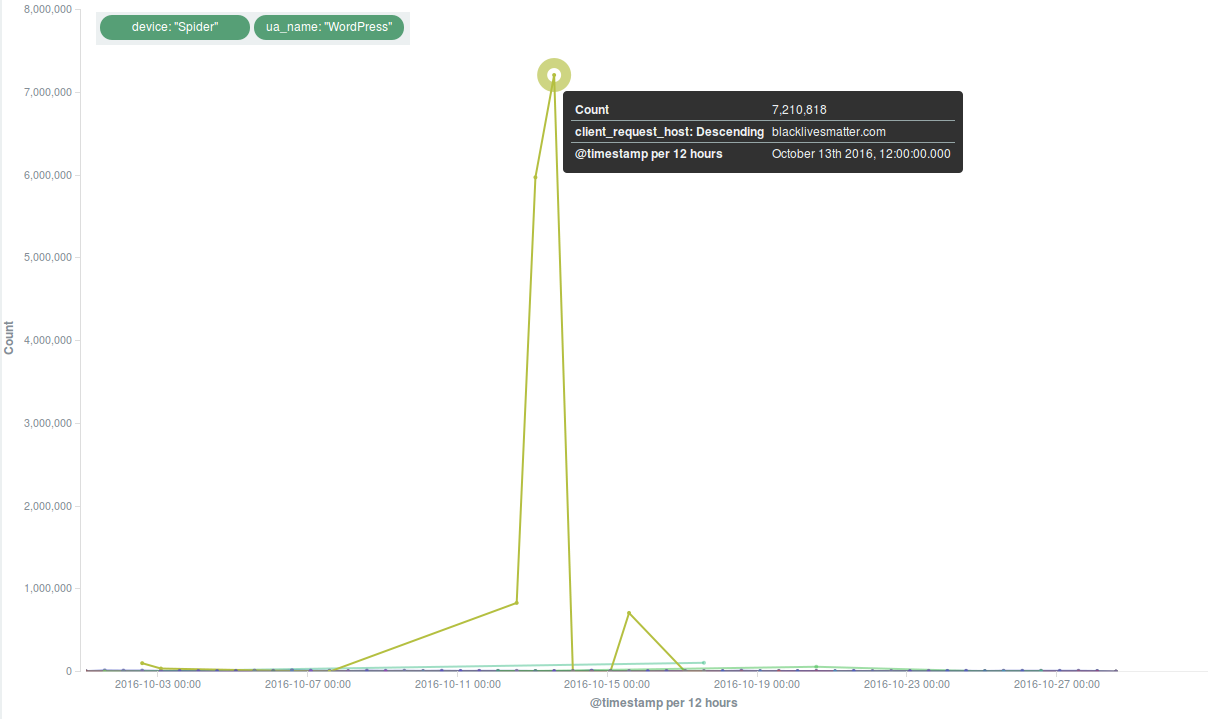
The most intense DDoS attempt this month targeted the official Black Lives Matter website, which has been under attack for months, as we will describe in the new Deflect Labs report that will soon be published.
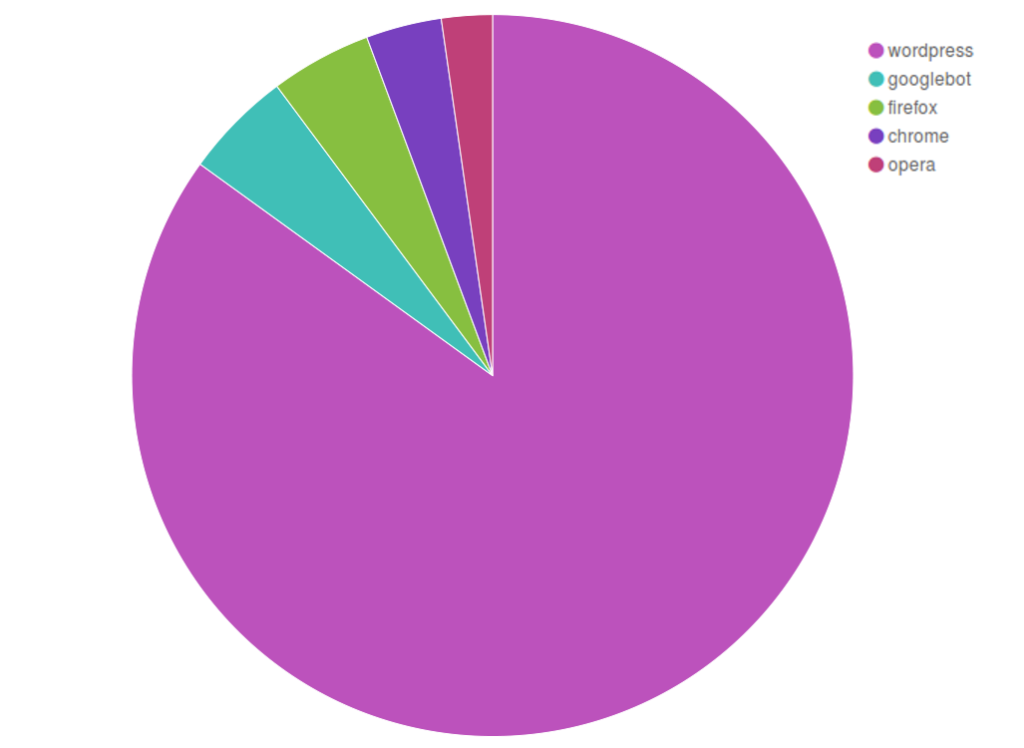
As we have often seen in DDoS attacks against Black Lives Matter, the botnet originated in great part from the United States, and was characterized by a large number of bots masquerading themselves with a “spider” user agent device and a “wordpress” user agent name.
[one_third]
[/one_third][one_third]

[/one_third][one_third_last]
[/one_third_last]
Towards the end of the month, we were struck by news of another DDoS attack elsewhere on the internet. On the 21st October a record-breaking DDoS attack against the domain name provider Dyn caused an outage that made important websites like Twitter, Reddit or Spotify unreachable for several hours on the East Coast of the United States and in Japan. As in the September attack against KrebsOnSecurity, this attack exploited Internet of Things devices through malware called Mirai that had just been released to the public. As Bruce Schneier concludes in his post on this episode and the lessons we can learn from it, DDoS attacks are likely to become stronger and stronger. If you defend human rights, fight for social justice or produce independent media, consider protecting your website under Deflect!