Deflect stats
-
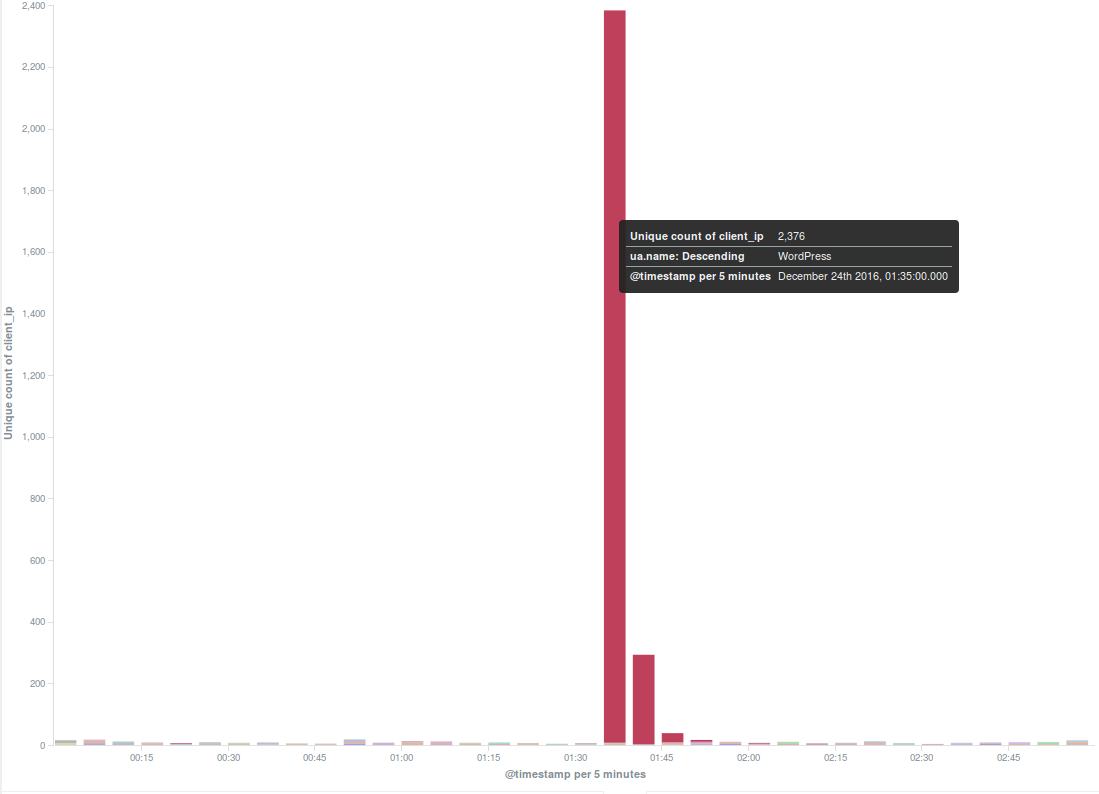
Deflect Stats December 2016
In December 2016 the Deflect network recorded a slight increase in the number of total hits as compared to the…
-
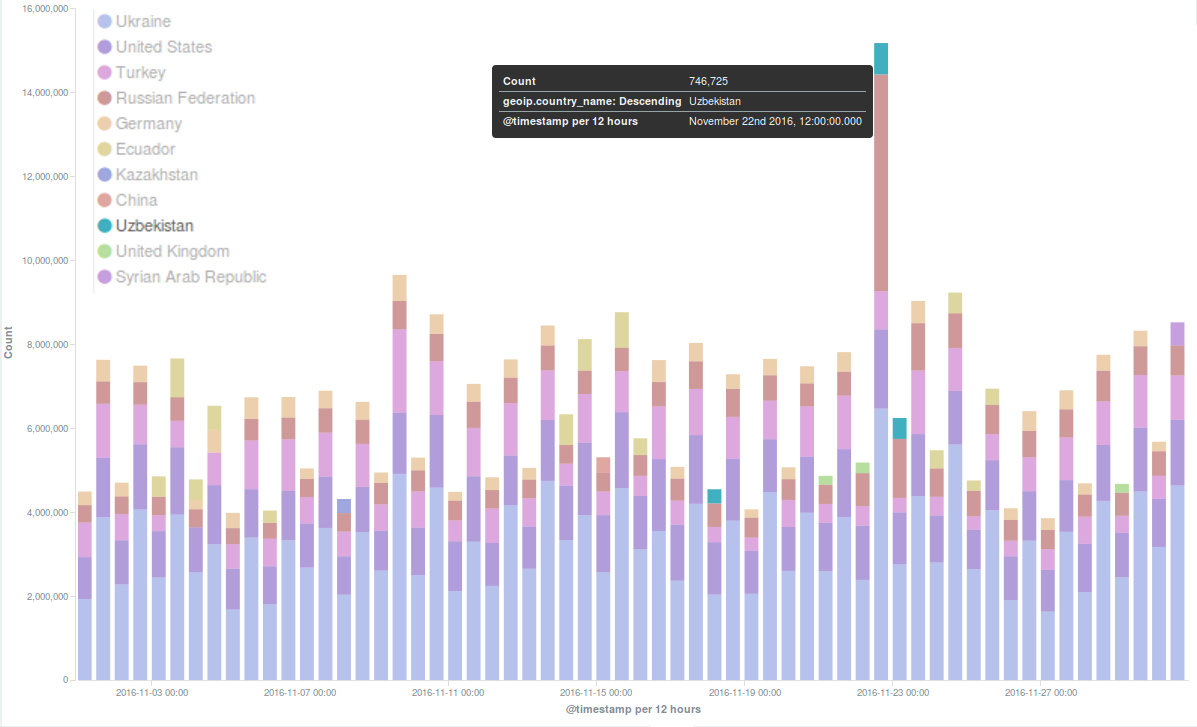
Deflect Stats November 2016
In November the Deflect network served pages to many legitimate visitors interested in breaking news reported by deflected websites, and…
-
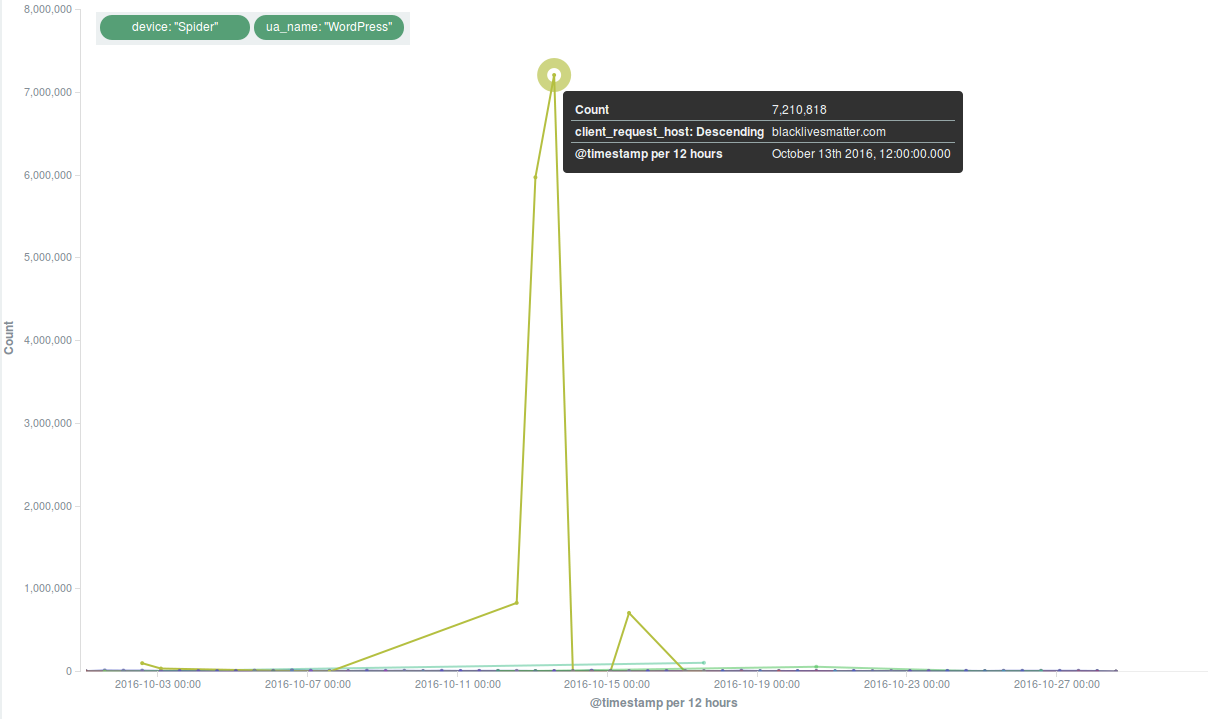
Deflect Stats October 2016
In October Deflect’s metrics kept following the trend we had seen in September, with comparable figures in terms of unique…
-
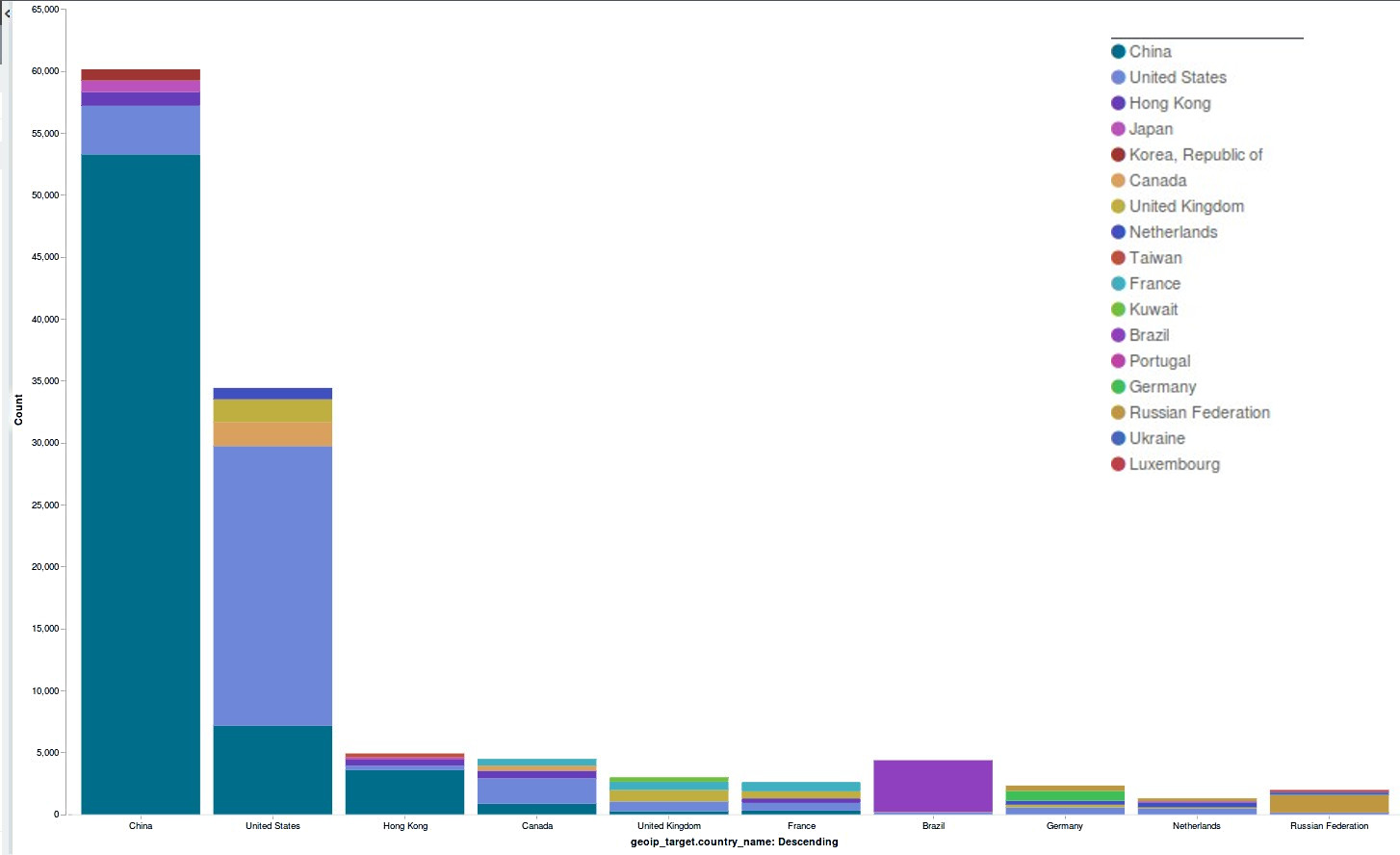
Deflect Stats September 2016
In September, Deflect metrics grew as new websites joined the service and a popular Syrian website rejoined Deflect to ensure…
-
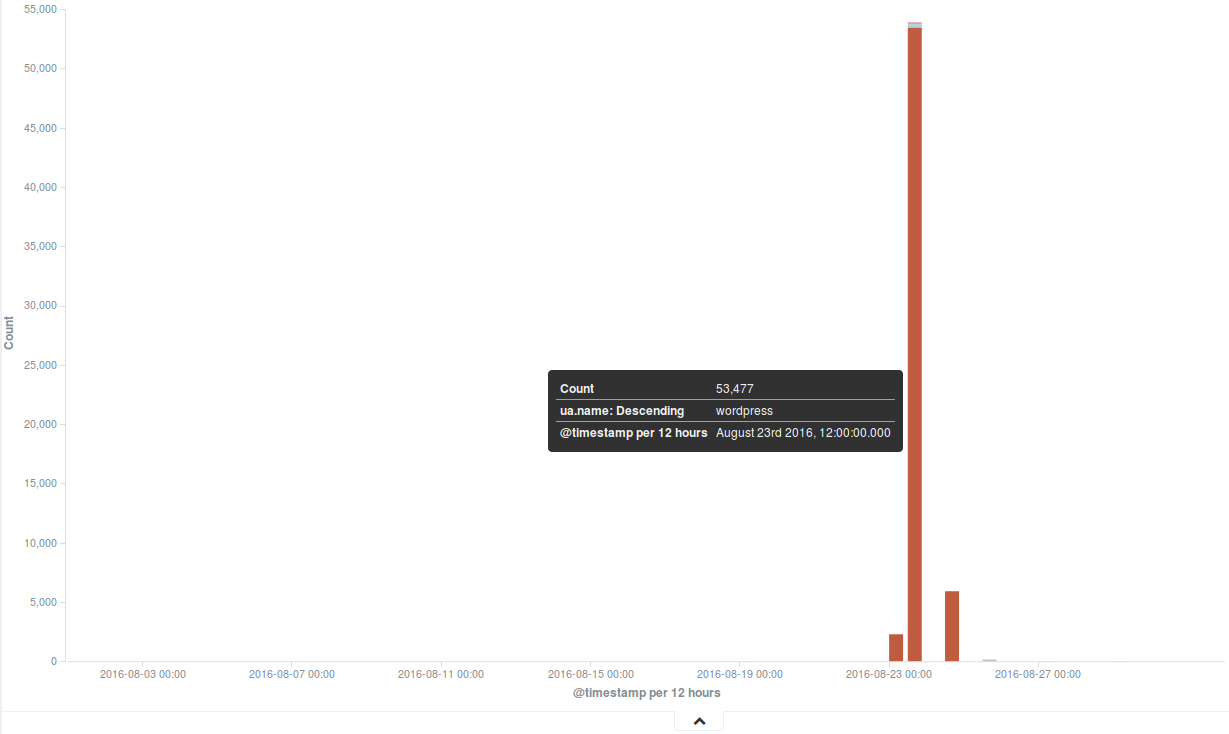
Deflect Stats August 2016
“No news is good news” in the DDoS mitigation game, and this is what we were hoping for in August…
-
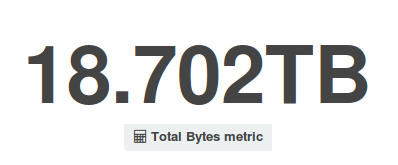
Deflect Stats July 2016
From what we can conclude from our statistics, during the month of July bot controllers must have come back from…
-
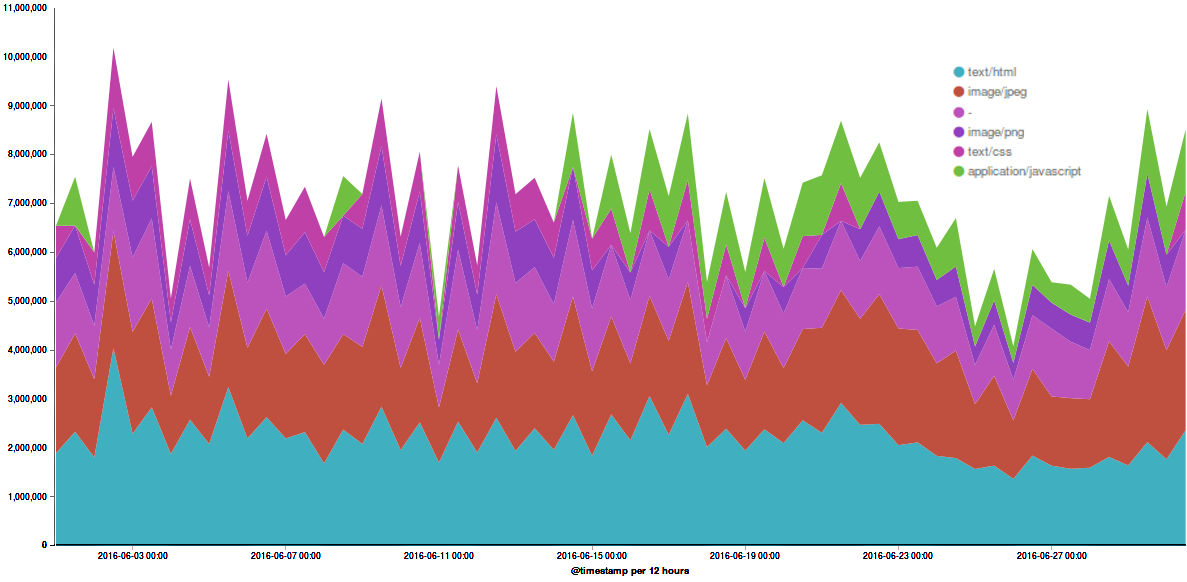
Deflect Stats June 2016
If any conclusion can be drawn in comparing this month’s statistics with the rest of the year, it’s probably that hot…