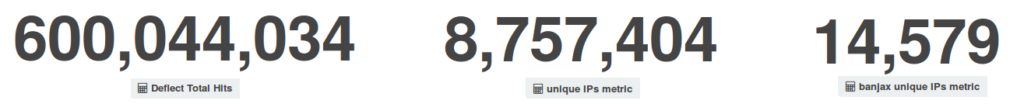
May 2016 was an interesting month for Deflect. We began the month with two intense attacks that required our team’s intervention right in the middle of May Day. After this, the month unrolled with a series of smaller attacks against the same websites, which were by then automatically mitigated by the Deflect network without requiring further effort. Traffic figures were comparable to those recorded in April.
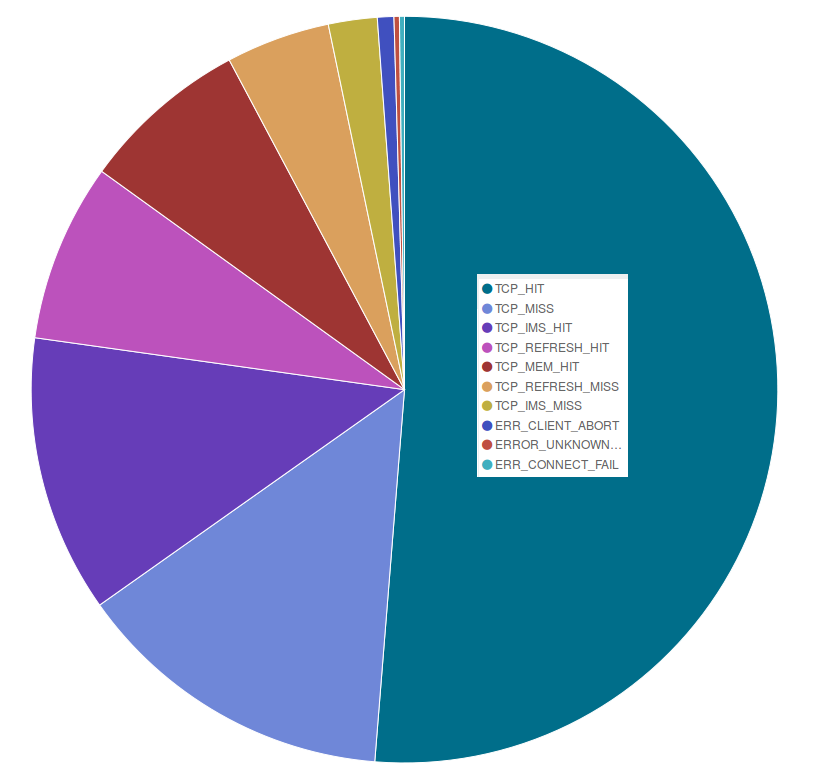
As shown in the pie chart below, also in May, as in April, around 70% of the pages we served were cached in our servers, while we had to get a copy from our users’ websites for approximately 20% of the requests we received.
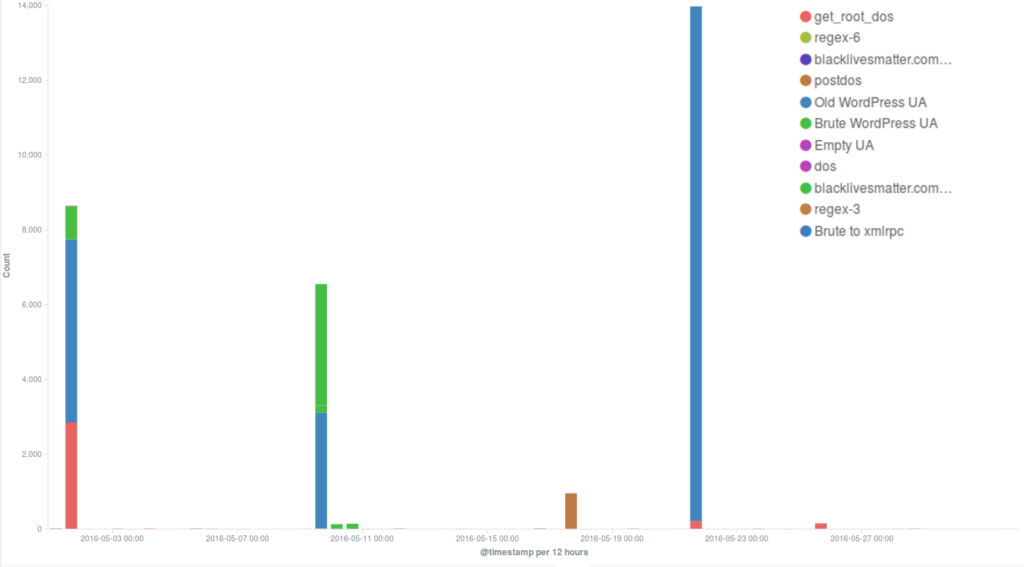
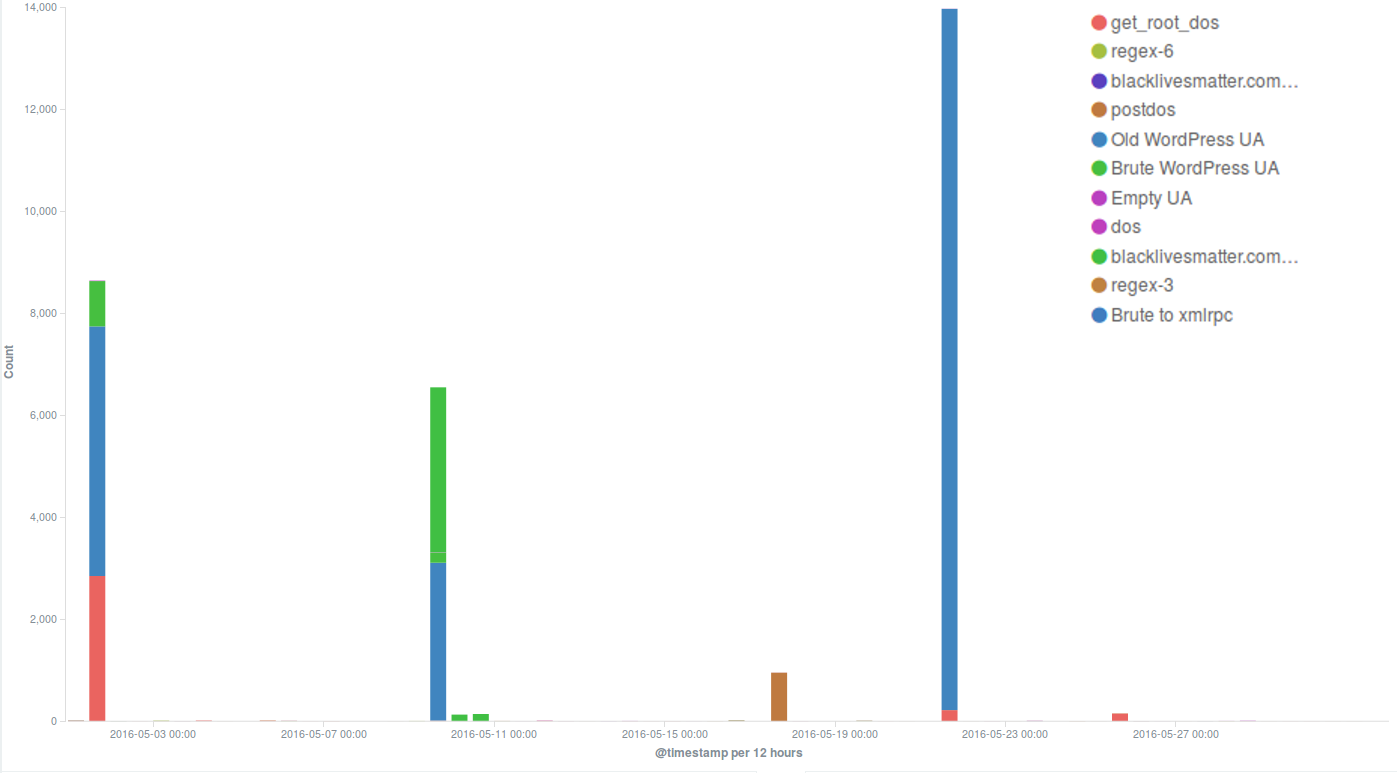
May attacks on the Deflect network
On May Day Deflect mitigated two strong attacks that required our staff’s intervention.
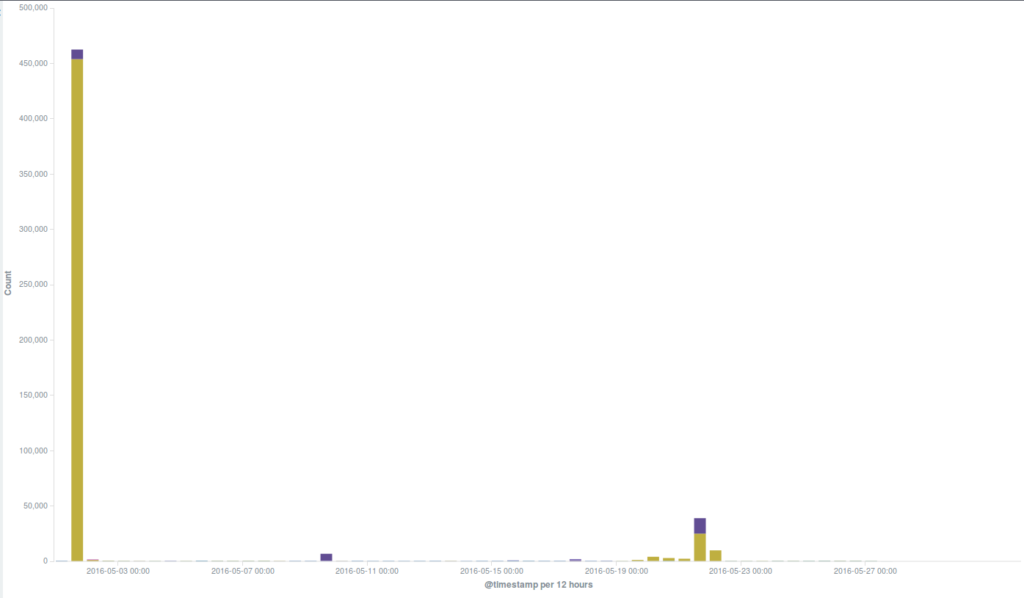
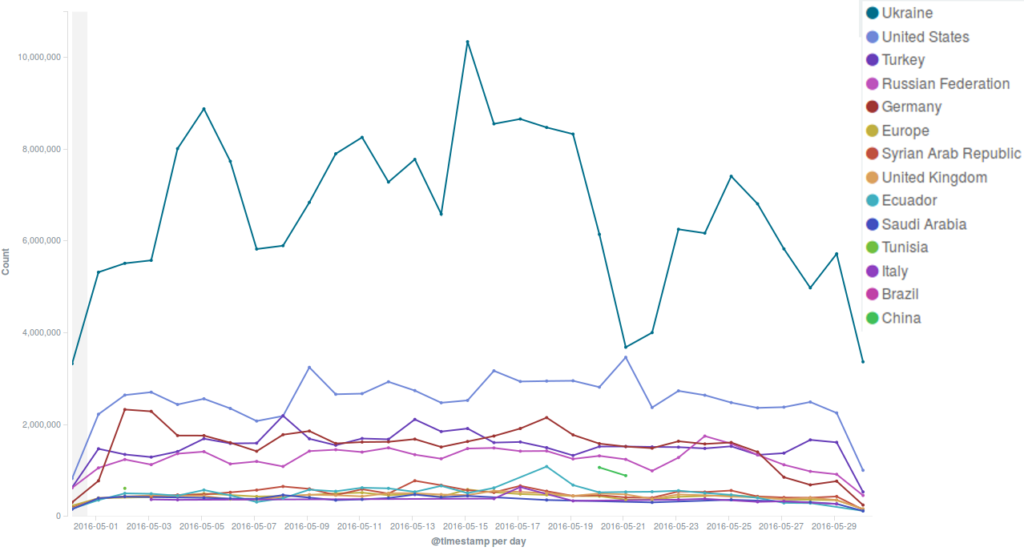
Several incidents observed during the month were using the WordPress Pingback reflective attack method, which is very common and we often encounter in our day-to-day work. This is the method used in one of the strong attacks we mitigated on the 1st May, when thousands of bots attacked the targeted website for the most part of the day, up to midnight. Although we have seen much larger botnets attacking our protected websites, this one hit with short peaks of high intensity, forcing us to intervene manually in order to trigger an earlier blockage of these requests and make sure they couldn’t reach the origin server, as well as to reduce the load on our servers. Since the WordPress Pingback attack uses any WordPress website available anywhere on the web to create a botnet, it was impossible for us to identify a main country of origin for this attack.
By deploying the Banjax Challenger, we eliminated all the bots requesting these pages.
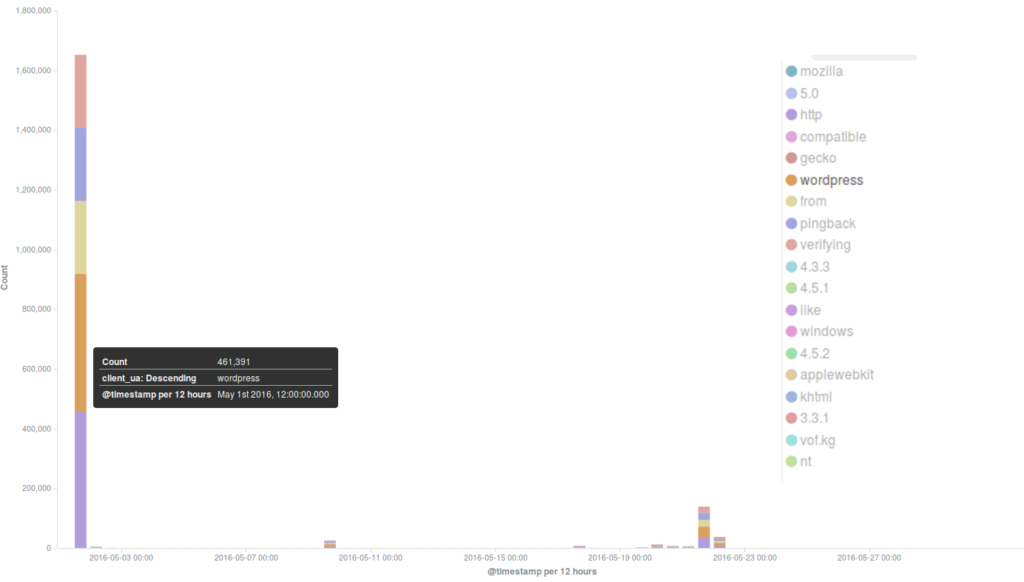
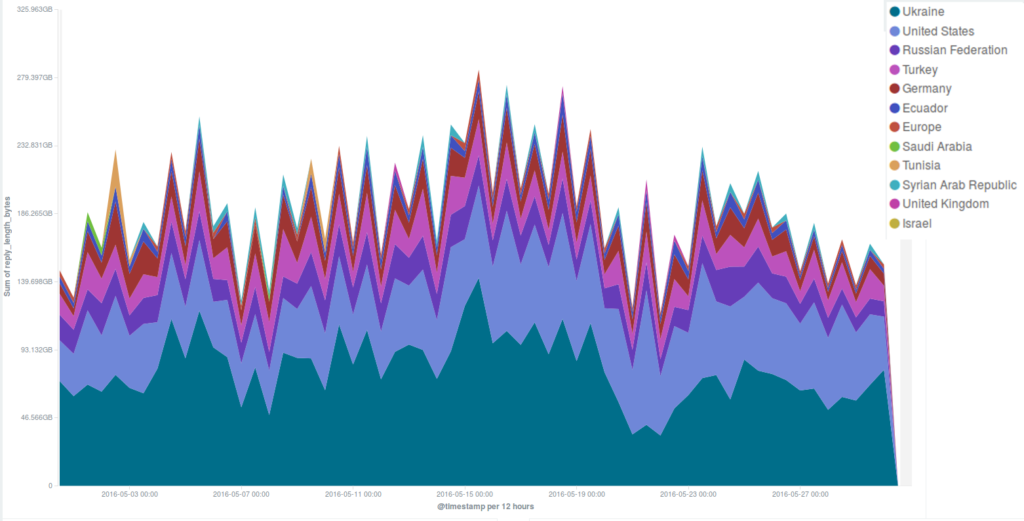
One of the websites targeted by the May Day DDoS attacks was blacklivesmatter.com, which was attacked again during the rest of the month, in particular on the 9th and 21st May. These attacks were based on different methods: while in the latter cases a common WordPress pingback attack method was used, on May 1st the attackers flooded the site with GET requests to its root path (“/”), coming from various locations across the world. Deflect automatically mitigated the second and third attacks, but the first one, which lasted 2 hours with a fairly steady level of 8000 hits per minute, managed to take the server down despite a lot of content being served by Deflect’s edge servers. We will be investigating these attacks in more detail with the aim of publishing our analysis in a Deflect Labs report.