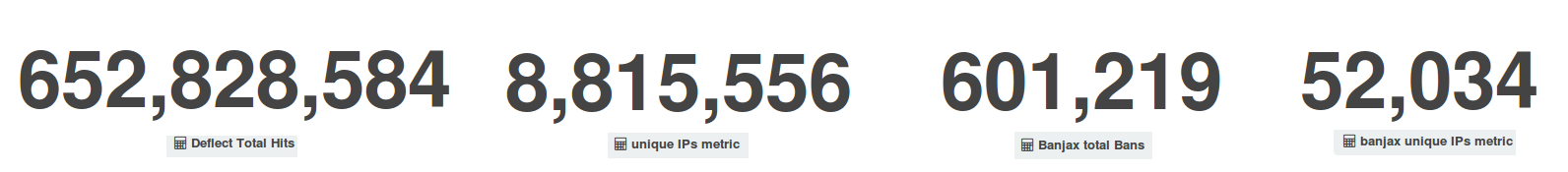
From what we can conclude from our statistics, during the month of July bot controllers must have come back from their holidays, since the traffic on the Deflect network has started to increase again and we have witnessed one of the most intense bursts of DDoS attacks we had observed so far. This series of incidents slightly increased our metrics in terms of total hits (652.8 millions vs. 514.1 millions in June) and unique visitors (8.8 millions vs. 7.8 millions in June), but in terms of banned IPs the increase was significant, with 601,219 total banning events, against 33,637 bans in June, and with 52,034 unique IPs banned, against 2,915 unique IPs banned during the previous month.
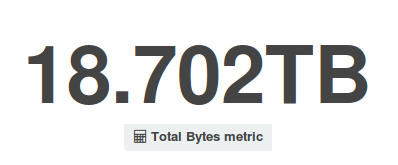
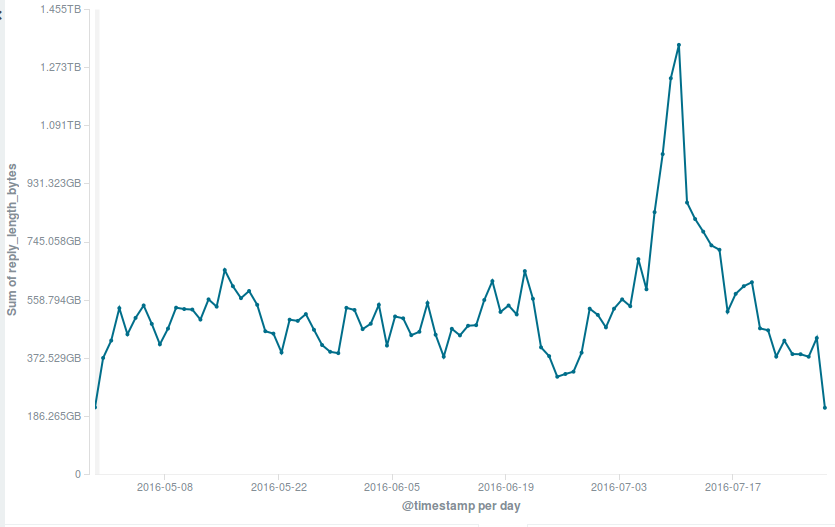
 A notable increase was recorded also in our bandwidth usage, which peaked to 18.7TB from an average monthly usage of about 13.6TB reached in the previous quarter.
A notable increase was recorded also in our bandwidth usage, which peaked to 18.7TB from an average monthly usage of about 13.6TB reached in the previous quarter.
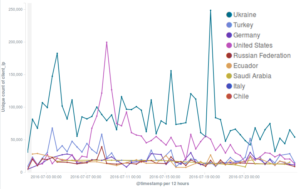
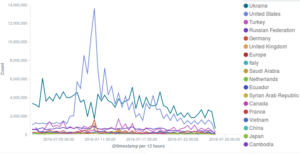
Setting aside malicious events, trends in our statistics are mostly unchanged, with a majority of connections originating from Ukraine, the United States and Turkey.
[one_third]
[/one_third][one_third]
[/one_third][one_third_last]
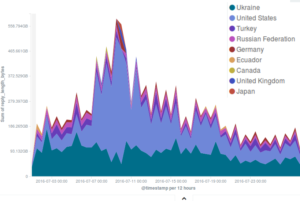
[/one_third_last]
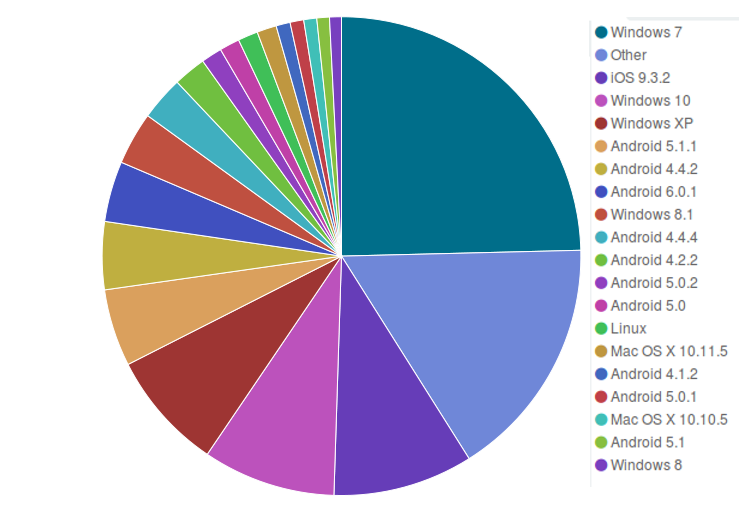
Looking at visitors’ user agents, we can see that Windows is still the most used operating system, covering at least 46.1% of all connections, followed by Android with 24.63% and by iOS with 9.28%. The amount of connections from Windows XP has luckily reduced from 10.18% last month to 8.13% in July, but still the same recommendations we gave in the post on June statistics apply to anyone who’s still running Windows XP on their computers: update your system to a newer version of Windows or, better, switch to Linux!
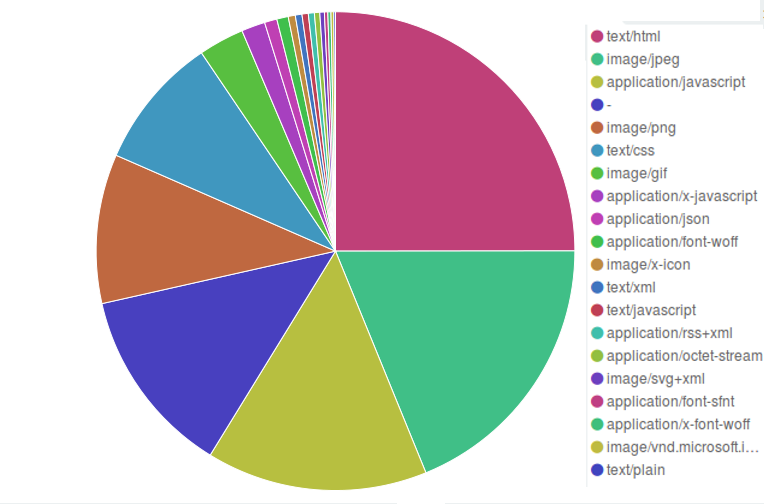
From the statistics on requested resources, we can also visualize what kinds of contents are being requested, with over half of the connections requesting text and images from websites.
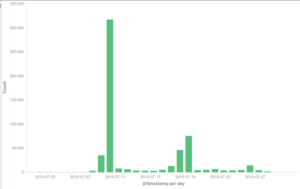
July attacks on the Deflect network
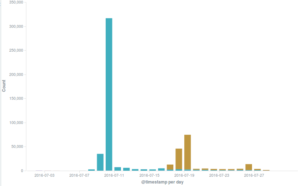
Among the DDoS attacks Deflect helped mitigate, there were some of the most intense bursts we ever observed on our network, targeting the Black Lives Matter official website on the 10th July, and a series of smaller attacks against an independent media website between the 18th and 19th July.
[one_third]
[/one_third][one_third]
[/one_third][one_third_last]
[/one_third_last]
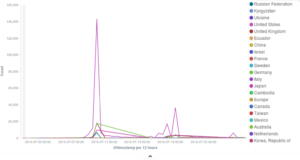
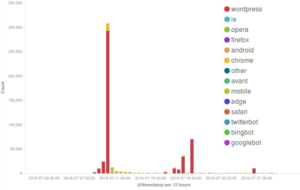
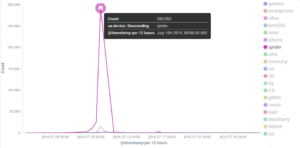
As we noted in the post on the attack on Black Lives Matter, the 10th July incidents were based on the frequent WordPress Pingback reflective attack method. This can be seen in the graph on the user agent declared by banned bots in the peak corresponding to the attack, where the “wordpress” UA makes up the majority of connections. The same user agent is also clearly visible in the peak of banning events observed on the 18th and 19th July.
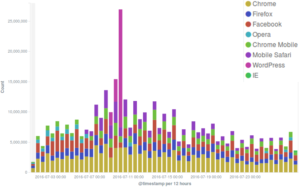
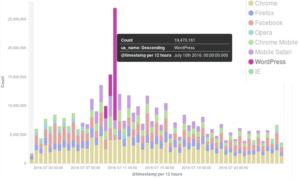
A similar pattern can be observed in the count of all connections to the Deflect network, where Google Chrome is the most used browser for regular connections to deflected websites, but a peak of “WordPress” UAs can be seen on the 10th July – those are clearly malicious requests coming from bots.
[one_third]
[/one_third][one_third]
[/one_third][one_third_last]
[/one_third_last]
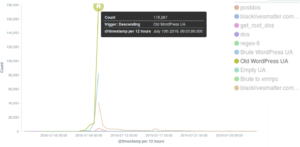
The main incident observed on the 10th July against the Black Lives Matter website triggered a dramatic increase in banning events by our banning tool Banjax, which recognized the malicious requests from their Old WordPress UA, despite the fact that bots were masquerading themselves as “spiders“.
[one_half]
[/one_half][one_half_last]
[/one_half_last]