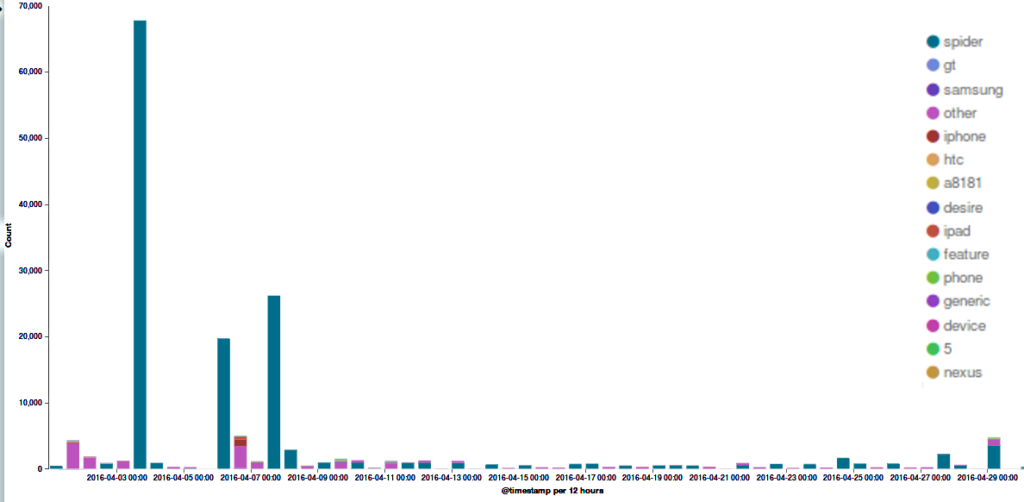
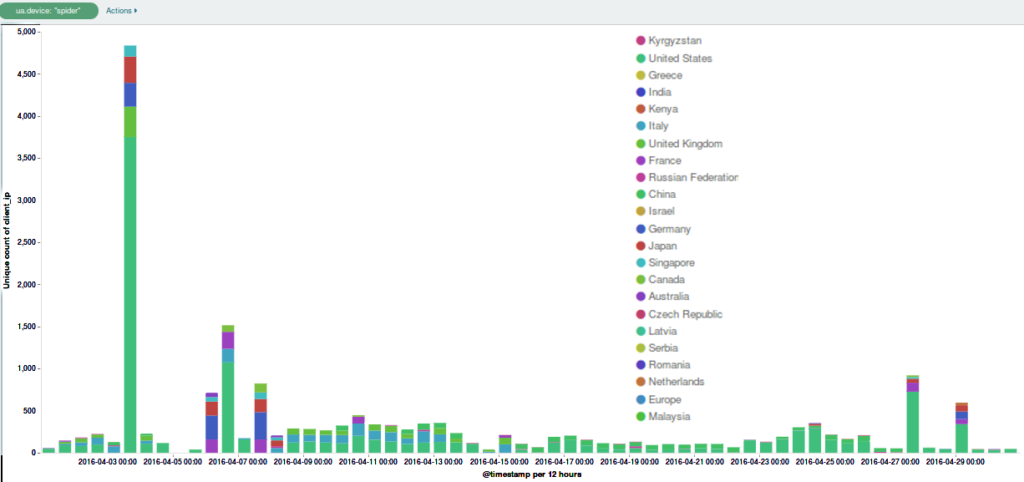
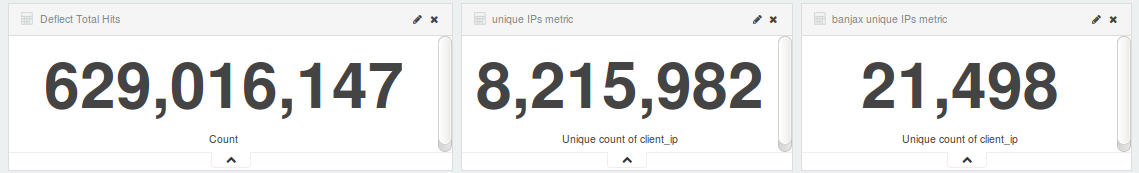
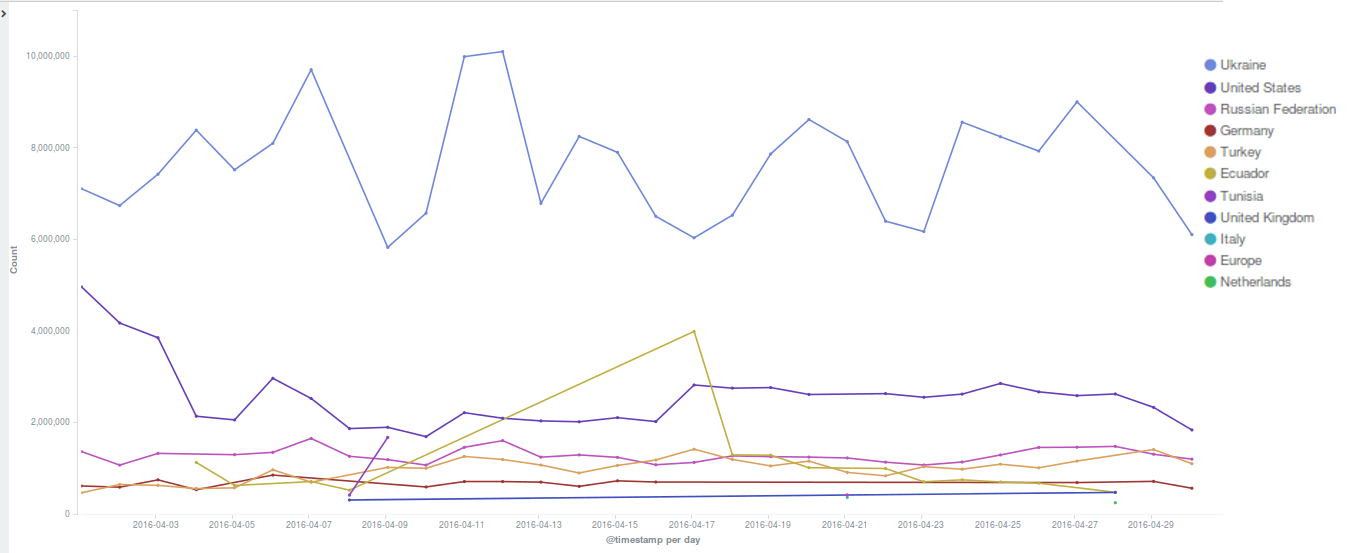
April 2016 was noticeable for the amount of attacks launched against Deflect protected websites. Most of them were using the WordPress Pingback reflective attack method. Ukrainian readers topped our statistics this month, with readers from the United States, Ecuador and Russia also generating several million daily hits.
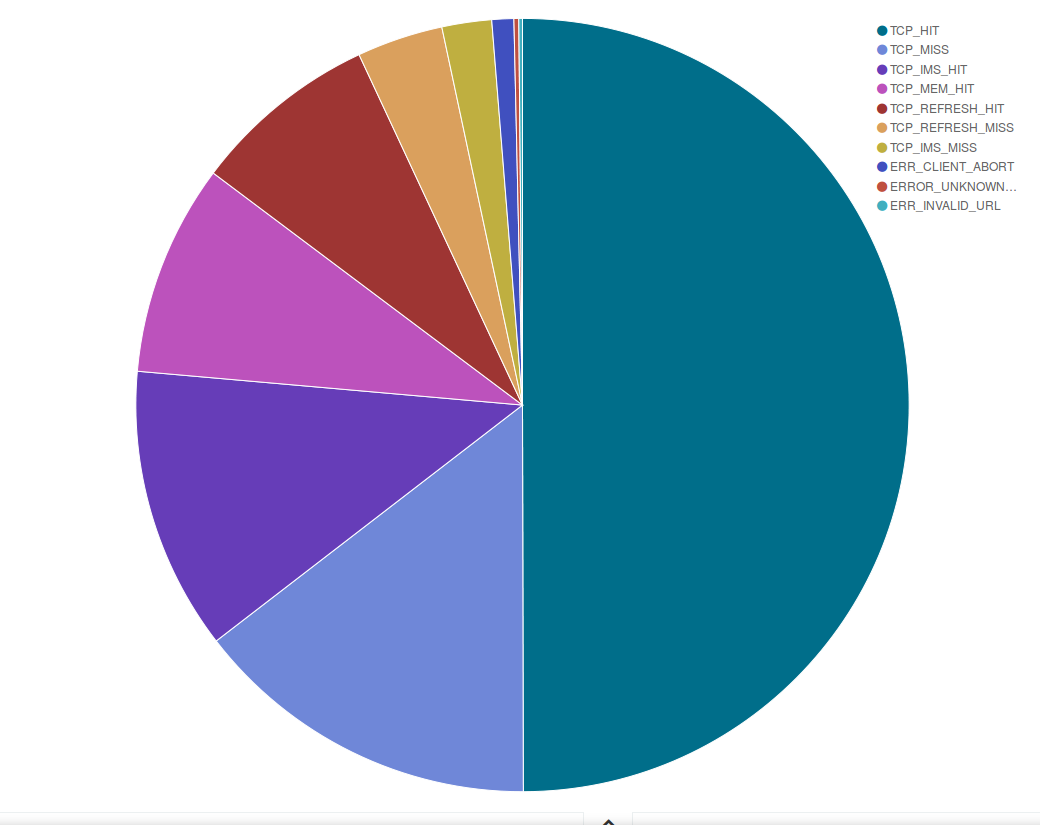
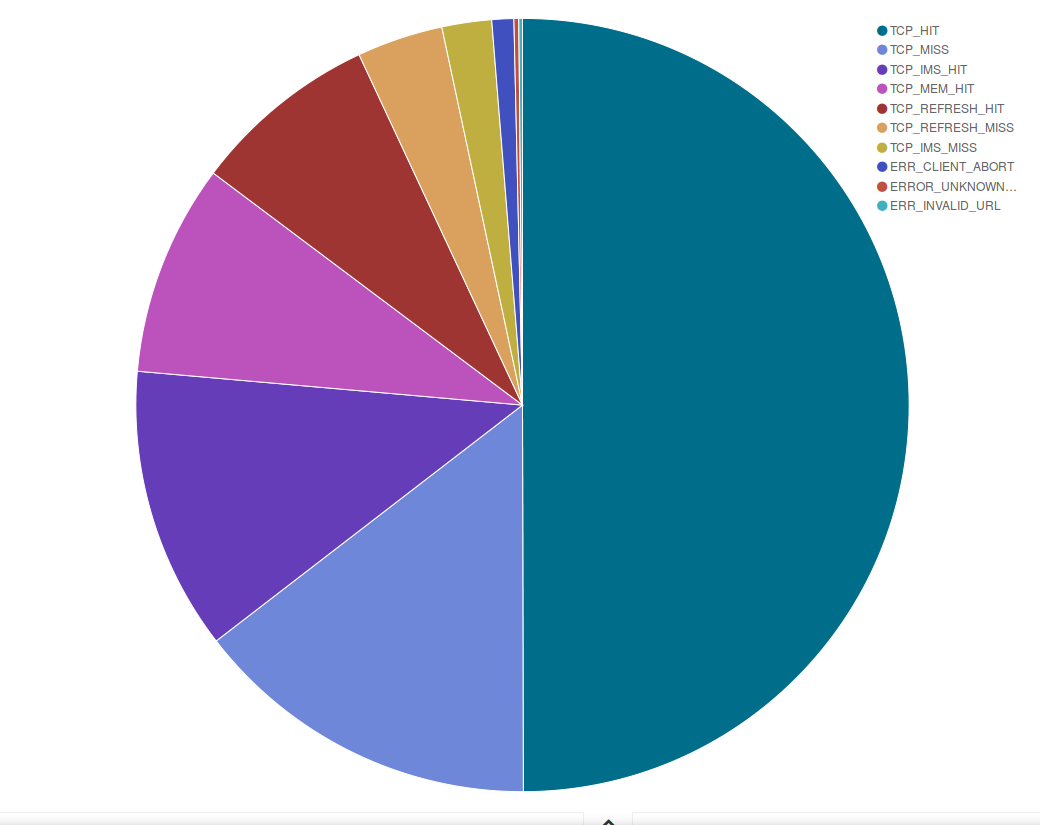
An interesting set of data regards our cache response: as shown in the pie chart below, in April around 70% of the pages we served were cached in our servers, while we had to get a copy from your websites for approximately 20% of the requests we received.
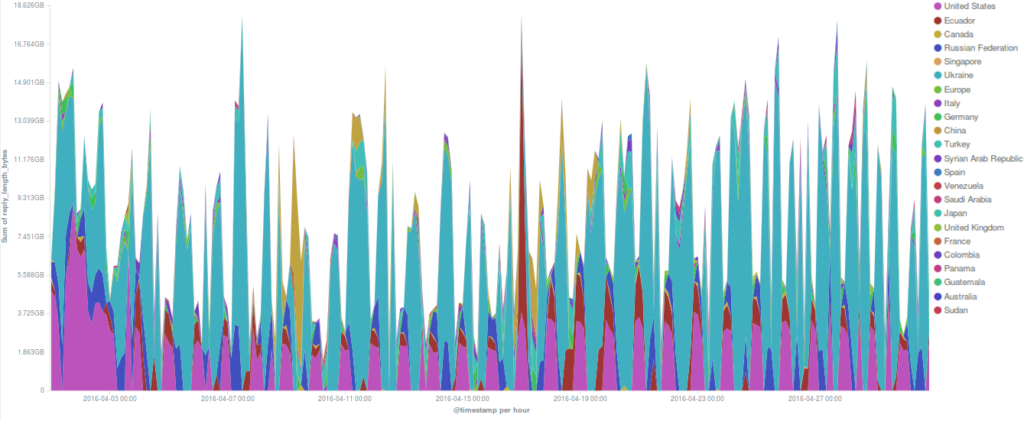
Attacks on the Deflect network in April 2016
Around a dozen separate incidents were recorded on the network in April. It’s important to note that the statistics represented here are from requests that triggered our banning mechanisms. In reality there may have been many more malicious requests. As per last month’s stats, the majority of bots were originating from the United States.
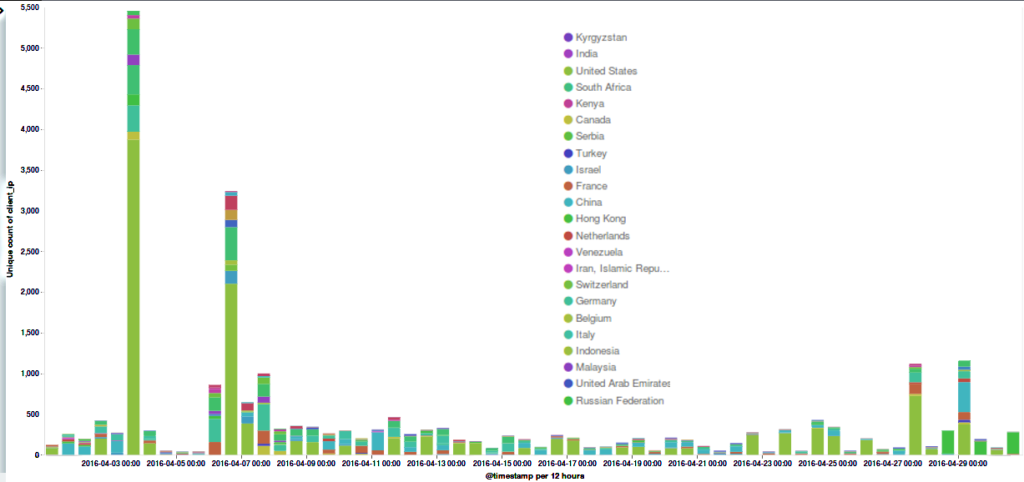
The majority of botnets captured by Deflect were using the WordPress Pingback attack mechanism, masquerading themselves with a “spider” user agent device. The “Ua_Device” parameter is a finding by our system, which recognises the user-agent strings used by many different devices, and categorises traffic accordingly. In this case the vast majority of IP addresses hitting the site were categorised as “spiders”. A spider, or web crawler, is software used by search engines to index the web. In order to index pages, however, a spider would usually visit each page of a website only once. In this case each IP address claiming to be a “spider” was requesting pages a very large number of times. User-agent strings are just text and this can be changed by clients to anything they like – including copying a user-agent string commonly used by some other software. We conclude that this was malicious traffic from a botnet masquerading as web-crawler traffic.