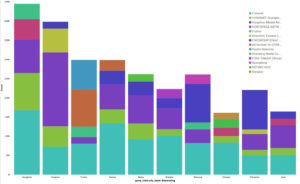
In September, Deflect metrics grew as new websites joined the service and a popular Syrian website rejoined Deflect to ensure an uninterrupted news stream on the regional conflict. In other news, the Internet witnessed the largest ever DDoS attacks, surpassing 600gbps and then 1 terabyte of traffic per second. These events followed the leaks of an online DDoS service, called vDOS. We ingested and visualized the leaked database, presenting some findings below for your perusal 🙂
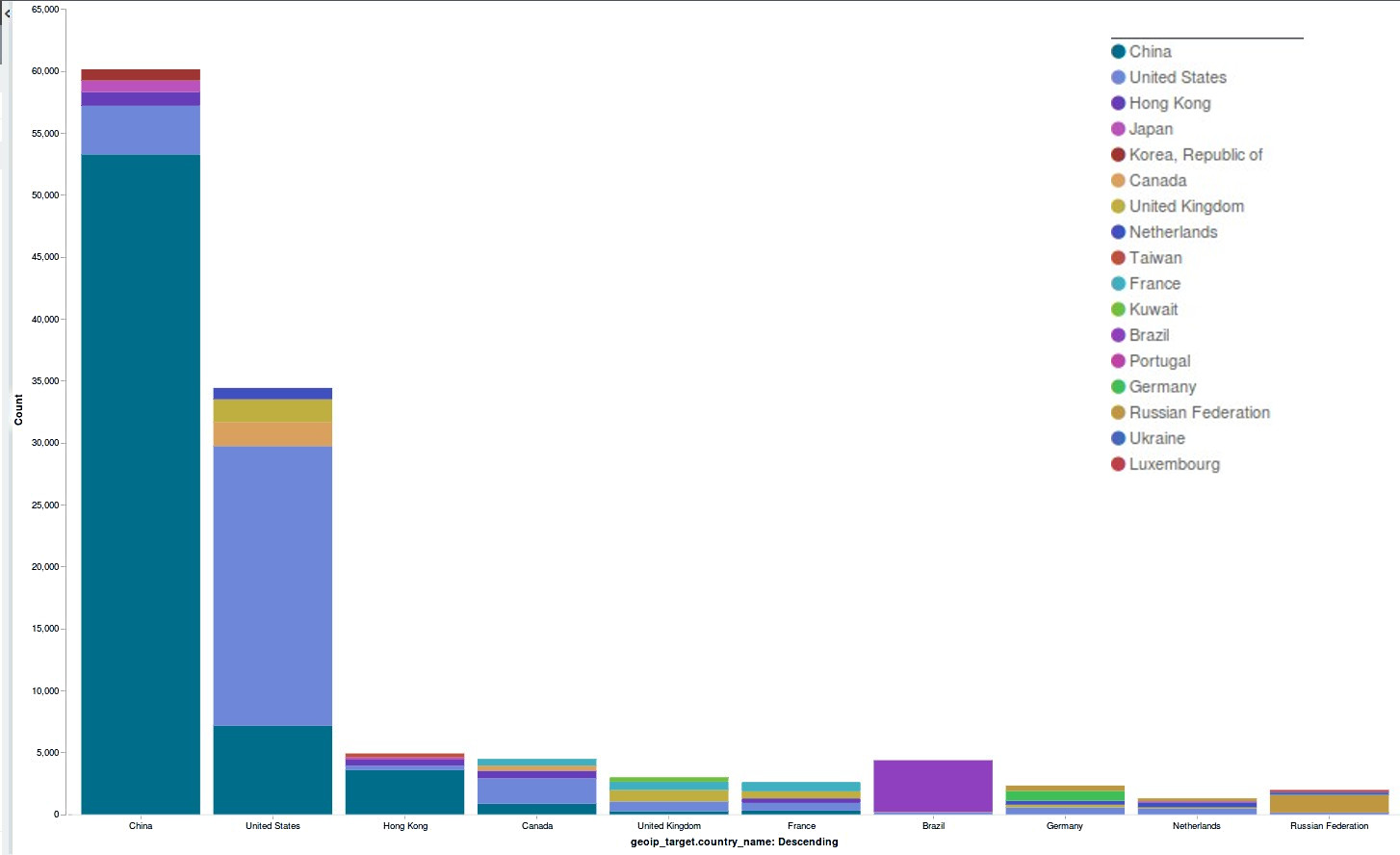
 Overall, the Deflect network served 623.2 million pages to 9.3 million unique visitors and our banning mechanism banned 27,238 bots. Let’s break up these statistics to put the figures in context and give them meaning:
Overall, the Deflect network served 623.2 million pages to 9.3 million unique visitors and our banning mechanism banned 27,238 bots. Let’s break up these statistics to put the figures in context and give them meaning:
[one_third]
[/one_third][one_third]
[/one_third][one_third_last]
[/one_third_last]
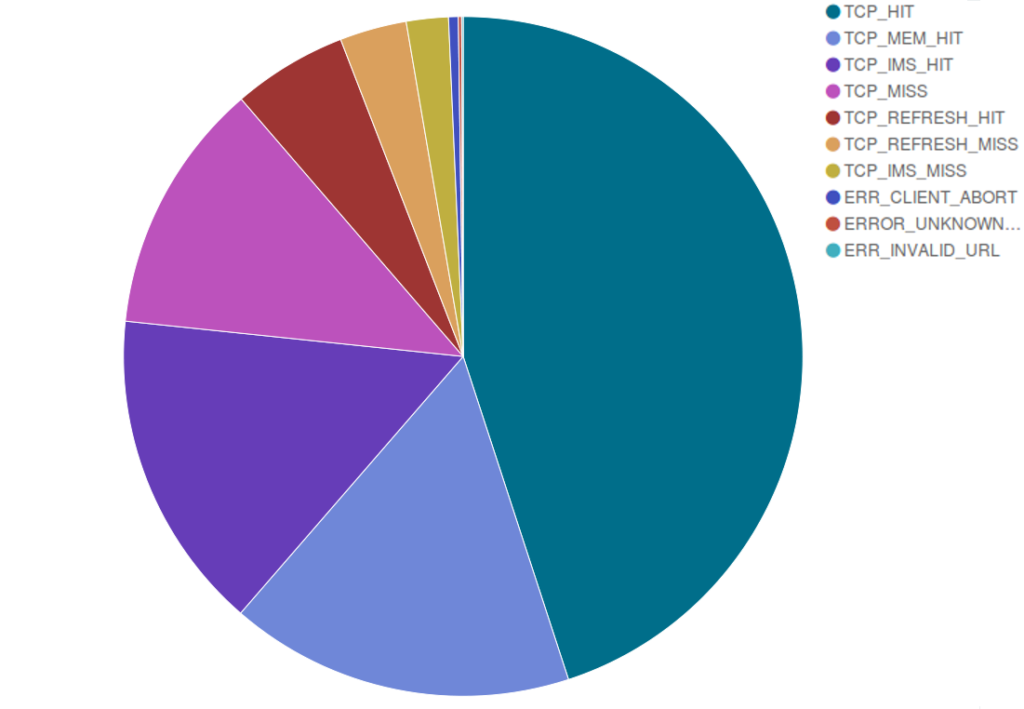
In September we also observed an improvement in our cache response: as you can see in the pie chart below, around 82% of the pages we served were cached in our servers, while we had to get a copy from your websites for approximately 17% of the requests we received.
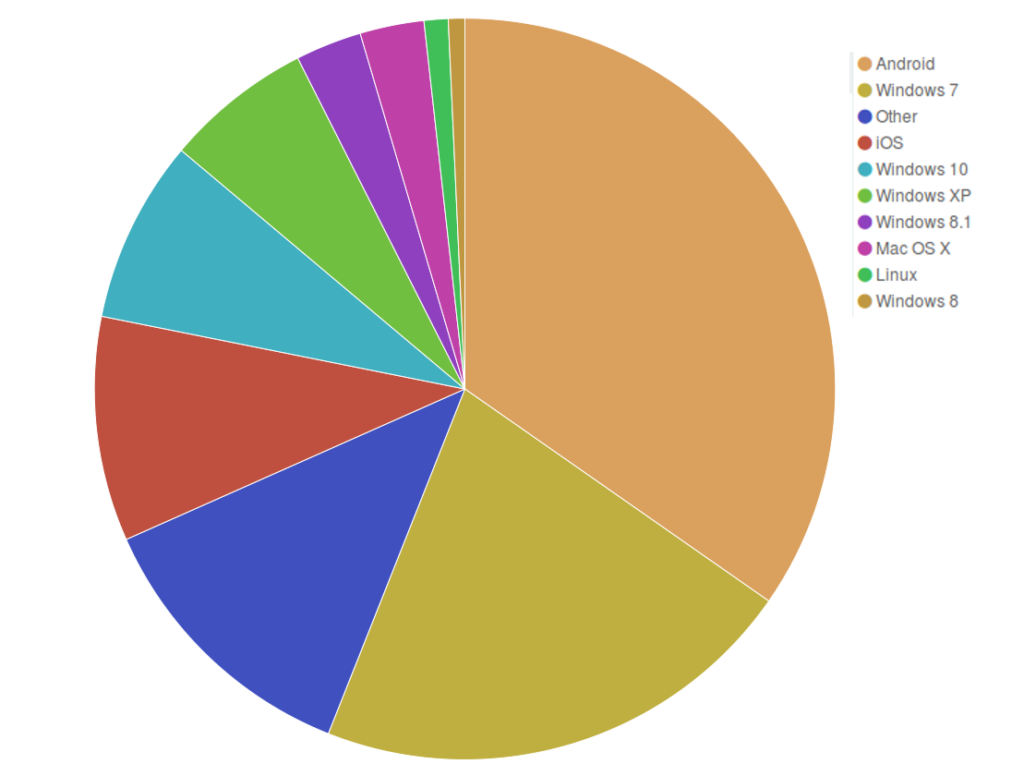
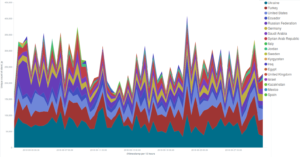
Our stats on the operating systems used by visitors of deflected websites suggest that the usage of Android is spreading, from around 25% in the last few months to nearly 35%, while the quantity of Windows users has shrunk from around 50% to 39.34%. We are glad to see that the slice of pie corresponding to the obsolete Windows XP is getting smaller and smaller (6.42% last month) — we hope it will soon disappear altogether from our graphs!
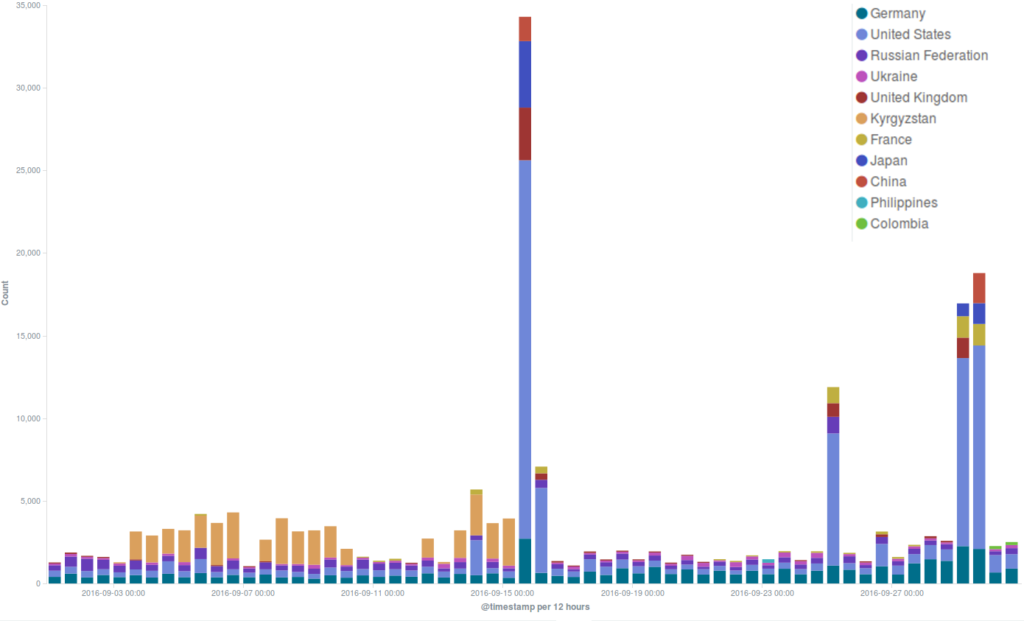
September attacks
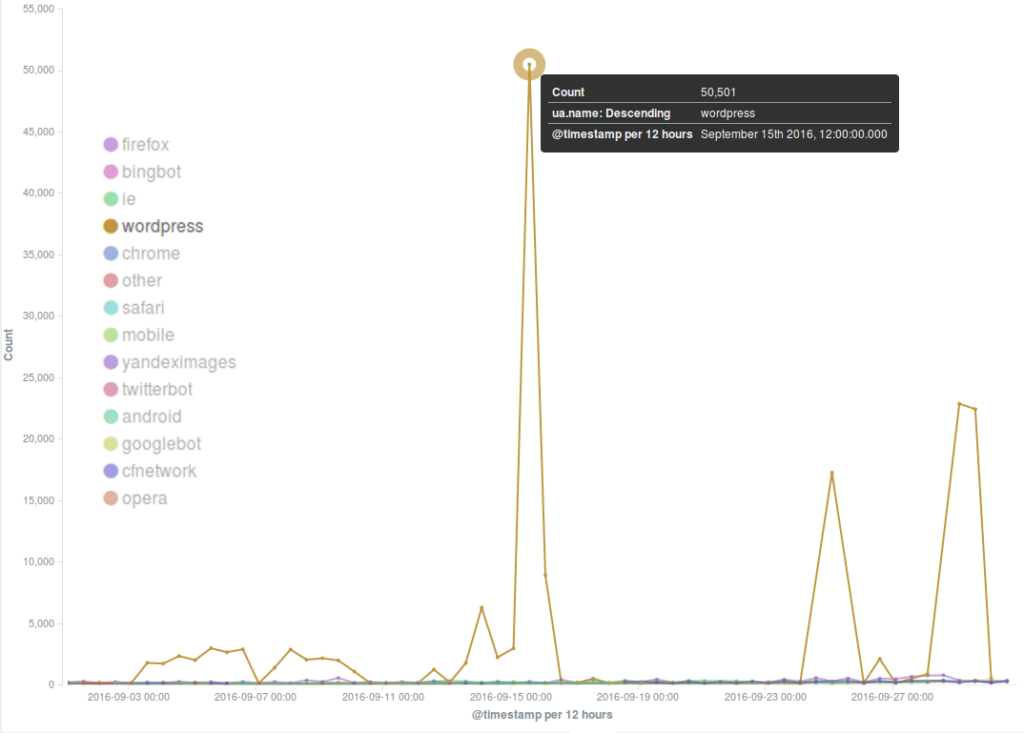
Last month Deflect mitigated automatically several DDoS attempts targeting especially three websites.
[one_third]
[/one_third][one_third]
[/one_third][one_third_last]
[/one_third_last]
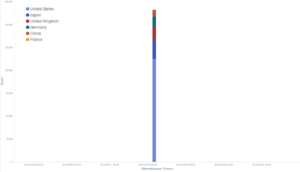
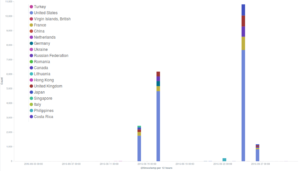
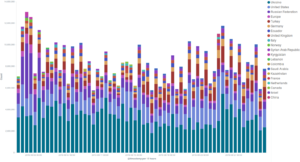
A split visualization of the major incidents targeting three deflected websites divided by country of origin of the bots shows that in each case the main country of origin was the United States. Another common feature we have observed in most of these DDoS attempts is the method used to launch the attack – the common WordPress Pingback reflective attack method we have often reported about lately.
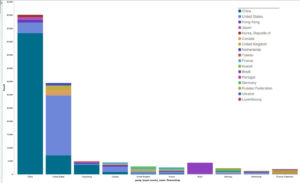
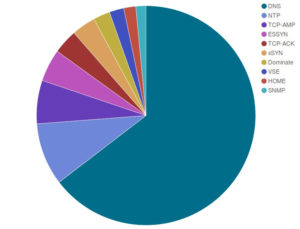
Another attack gave us a lot of food for thought in September. Although it wasn’t targeting the Deflect network, it marked a turning point in the history of DDoS attacks and online censorship. The attack targeted independent journalist Brian Krebs’ website KrebsOnSecurity, an important source of digital security news that had recently reported on the hack of a DDoS-for-hire business known as vDOS. One of our clients appeared in the vDOS target list. Otherwise we saw that the most common method of attack requested was DNS (likely reflection) and the majority of clients were from China, attacking websites that were also from China.
[one_third]
What made this attack particularly concerning was its unseen intensity: 620 gigabits per second of data were constantly thrown at the website for hours, until Akamai, a network provider that was supplying KrebsOnSecurity DDoS mitigation services for free, decided that it was unsustainable for them and their clients to keep protecting Krebs’ website from that onslaught.
Read more about the attack on KrebsOnSecurity in this article, which also explains how its huge botnet was made of Internet of Things devices: common routers, printers, CCTV cameras and the like. The code used to create that botnet has now been released, and similar attacks will probably become more and more frequent. As Brian Krebs himself has noted in this readworthy post, we are witnessing an alarming trend towards an all-pervasive internet censorship. In the future DDoS attacks are foreseen to become more and more violent. Any website could be targeted, especially if they cover news from an independent point of view or support a hard-fought cause. DDoS mitigation is much more effective if a website gets protected in advance. If you defend Human Rights, run a civil society organisation or produce independent media, consider registering your website on Deflect now 🙂