Key Findings
- We identified traffic from thousands of IPs trying to brute-force WordPress websites protected by Deflect using the same user-agent (
Mozilla/5.0 (Windows NT 6.1; rv:52.0) Gecko/20100101 Firefox/52.0) since September 2017 - We confirmed that it was not only targeting Deflect protected websites, but targeting also a large number of websites over Internet
- We analyze in this blog post the origin IPs of this botnet, mostly coming from IP addresses located in China.
Introduction
In August 2018, we identified several attempts of brute-forcing WordPress websites protected by Deflect. These attacks were all using the same user-agent, Firefox version 52 on Windows 7 (Mozilla/5.0 (Windows NT 6.1; rv:52.0) Gecko/20100101 Firefox/52.0). By retracing similar attacks with this user-agent, we discovered a large number of IP addresses involved in these attacks on over more than hundred of Deflect protected websites since September 2017.
Presentation of an Attack
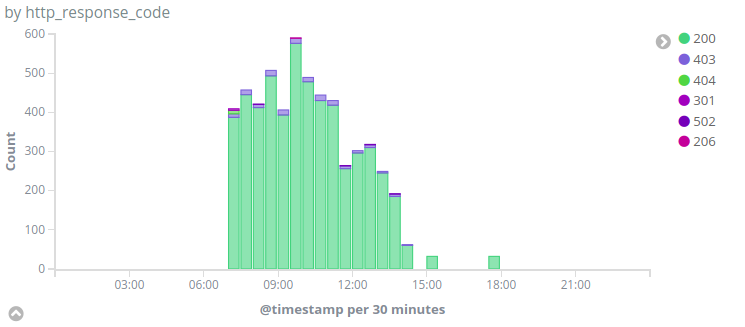
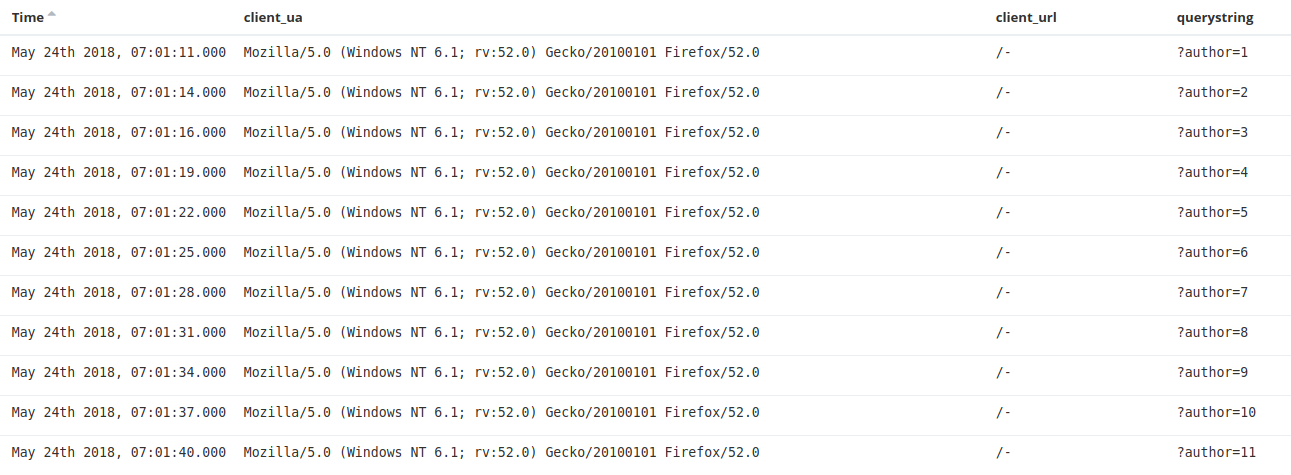
An example of an attack from this botnet can be found in the traffic we observed on a Deflect protected website on the 24th of May with the user agent `Mozilla/5.0 (Windows NT 6.1; rv:52.0) Gecko/20100101 Firefox/52.0` :
At first one IP, 125.65.109.XXX (AS38283 – CHINANET) enumerated the list of authors of the WordPress website :
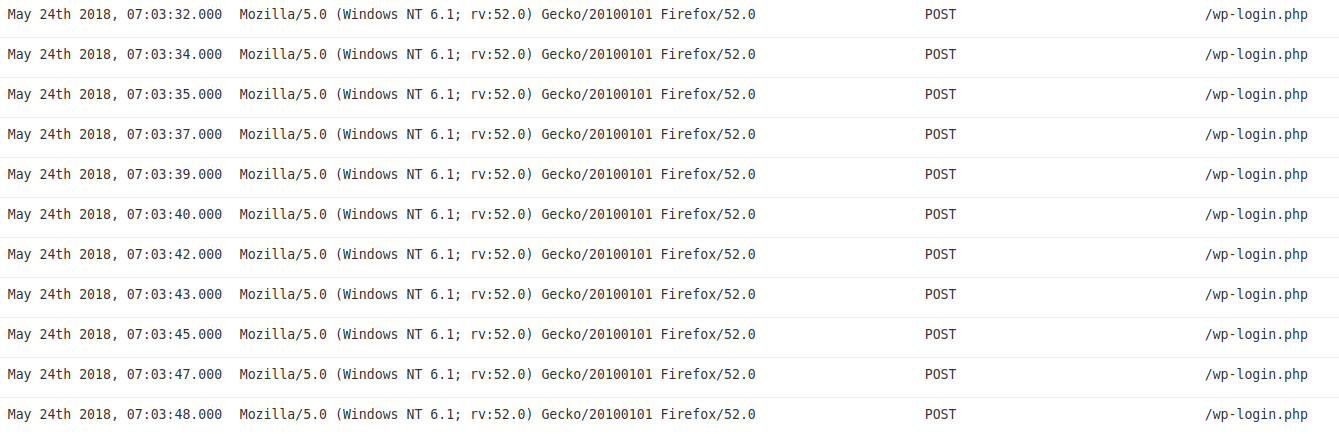
Then 168 different IP addresses were used to brute-force the password by doing POST queries to /wp-login.php :
Targeting beyond Deflect Users
The botnet’s large target list quickly made us think that it was not part of a political operation or a targeted attack, but rather an attempt to compromise any website available on the Internet. To confirm our hypothesis, we decided to share indicators of these attacks within threat intelligence groups as well as the GreyNoise platform to see if honeypots were targeted.
Shared Threat Intelligence
We shared indicators of attacks to other members of an Information Sharing and Analysis Center (ISAC) we are part of. Two members confirmed having seen the same attacks on their professional and personal websites. One of the members accepted to share logs and IP addresses with us, which confirmed the same type of attack with the same user-agent.
Using GreyNoise data
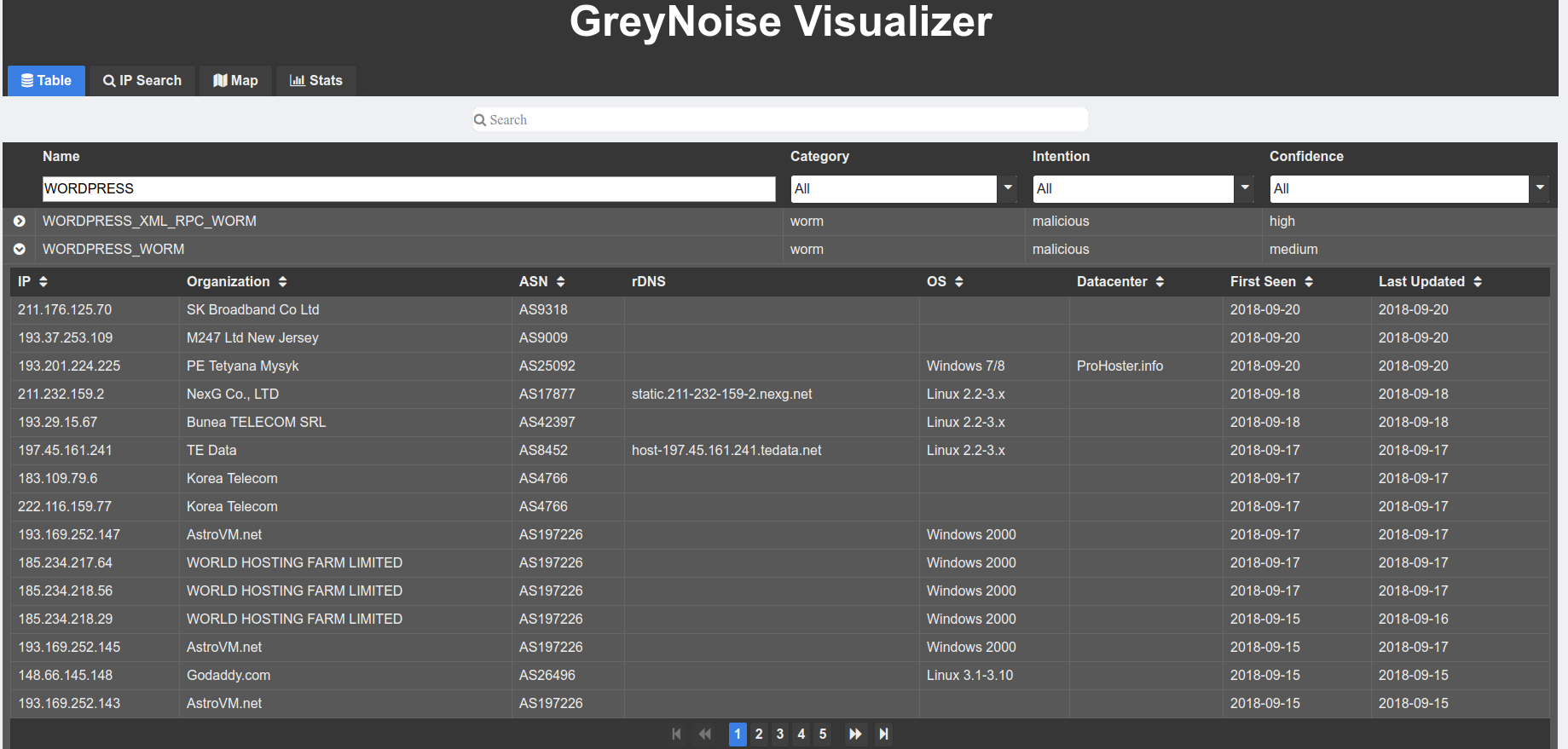
We used both the open and enterprise access of the GreyNoise platform to gather more data about this botnet. GreyNoise is a threat intelligence platform that focus on identifying the attack noise online through a large network of honeypots in order to differentiate targeted attacks from non-targeted attacks. (We got access to the Enterprise platform after an eQualit.ie member contributed to the development of tools for GreyNoise platform). GreyNoise works by gathering information on IPs that are scanning any GreyNoise’s honeypot, and tagging them based on the type of scan identified. We can see quickly in the GreyNoise visualizer that many IPs are identified as WORDPRESS_WORM :
We enumerated the list of IP addresses listed as WORDPRESS_WORM, and then queried detailed information for each IP in order to identify the one using the Firefox 52 user-agent characteristic of this botnet. We identified 725 different IP addresses from this data set among the last 5000 WordPress scanners available through the Enterprise API.
These two pieces of information confirm that this botnet is targeting websites far beyond the websites we protect with Deflect.
Analysis of the traffic to Deflect
We identified the first query from this botnet on Deflect websites on the 27th of September 2017. We have graphed the number of requests done by this botnet to /wp-login.php over time :
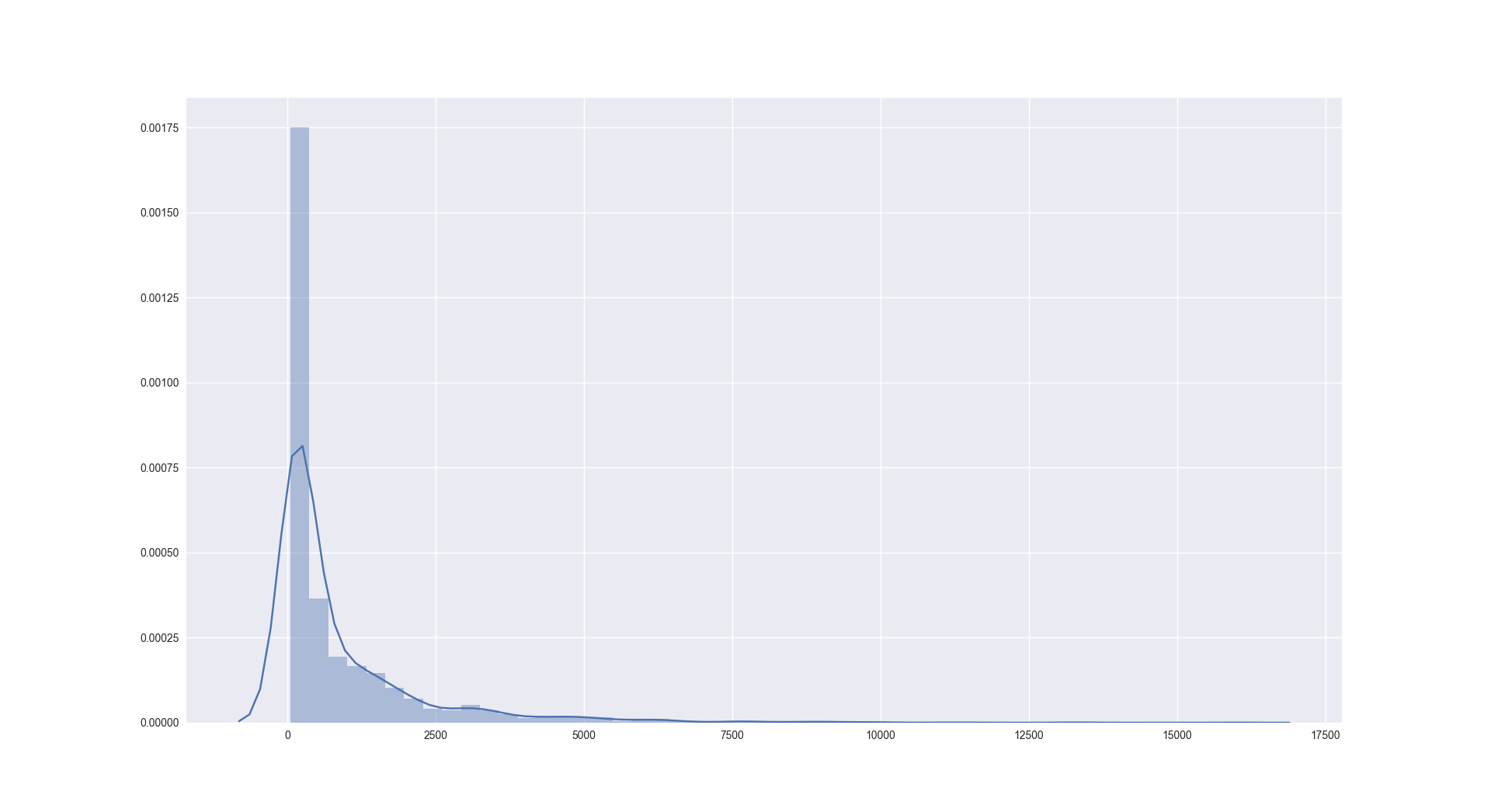
Looking more closely at the distribution of number of requests per IP addresses, we see that a small number of IP addresses are doing a large number of requests :
 Analysis of the botnet
Analysis of the botnet
We identified 3148 unique IPs belonging to this botnet from the following sources :
- 3011 targeting Deflect protected websites since September 2017
- 725 identified by GreyNoise as WordPress
- 7 from logs shared by people from different communities
Checking the origin Autonomous Systems, we can see that 39% of the IPs come from the AS 4134 (Chinanet backbone) and 4837 (China169) :
- 872 ASN4134 CHINANET-BACKBONE No.31,Jin-rong Street, CN
- 342 ASN4837 CHINA169-BACKBONE CHINA UNICOM China169 Backbone, CN
- 93 ASN9808 CMNET-GD Guangdong Mobile Communication Co.Ltd., CN
- 87 ASN18881 TELEFÔNICA BRASIL S.A, BR
- 86 ASN8452 TE-AS TE-AS, EG
- 82 ASN9498 BBIL-AP BHARTI Airtel Ltd., IN
- 50 ASN17974 TELKOMNET-AS2-AP PT Telekomunikasi Indonesia, ID
- 48 ASN3462 HINET Data Communication Business Group, TW
- 47 ASN4766 KIXS-AS-KR Korea Telecom, KR
- 40 ASN24445 CMNET-V4HENAN-AS-AP Henan Mobile Communications Co.,Ltd, CN
If we look at the origin countries of these IP’s, we see that 53% of them are based in China :
- 1654 China
- 171 Brazil
- 168 India
- 102 Russia
- 94 Indonesia
- 87 Egypt
- 82 Republic of Korea
- 65 United States
- 62 Taiwan
- 43 Vietnam
We queried ipinfo.io to get the type of Autonomous Systems these IP’s are part of :
- 2743 : Internet Service Providers
- 271 : Business
- 132 : Hosting
- 2 : Unknown
To identify the operating system of these bots, we used another interesting feature of GreyNoise, which is the identification of the operating system at the origin of these requests through passive fingerprinting techniques (using p0f signatures). By querying all the IPs from this botnet in GreyNoise and filtering on the one using the Firefox 52 user agent, we checked which operating systems these IPs used (1370 IP’s from our list were identified in GreyNoise with Firefox 52 user agent) :
- 662 unknown
- 238 Linux 2.6
- 209 Linux 2.4.x
- 88 Linux 3.1-3.10
- 63 Linux 2.4-2.6
- 51 Linux 2.2-3.x
- 17 Linux 3.11+
- 12 Linux 2.2.x-3.x (Embedded)
- 9 Linux 3.x
- 8 Mac OS X 10.x
- 6 Windows 7/8
- 4 FreeBSD
- 1 Linux 2.0
- 1 Windows 2000
- 1 Windows XP
Another interesting fact shown by GreyNoise data is that over these IPs, 2105 were also identified for other of types scans, mostly for the following suspicious activities :
- WEB_SCANNER_LOW: 1404,
- SSH_SCANNER_LOW: 1037
- SSH_WORM_LOW: 950
- WEB_CRAWLER: 705
- TELNET_SCANNER_LOW: 117
- TELNET_WORM_HIGH: 80
- SSH_WORM_HIGH: 77
- HTTP_ALT_SCANNER_LOW: 52
- SMB_SCANNER_LOW: 44
- SSH_SCANNER_HIGH: 33
We have used this data to map the activity identified by GreyNoise over time, first only for the WordPress brute-force traffic, then second for any suspicious activity :
We can see that this botnet is not used only to attack WordPress or that most of these devices are compromised by more than one malware.
Impact on Deflect
We have not identified any impact from this botnet on Deflect protected websites. The first reason is that any heavy traffic going beyond the threshold defined in our Banjax rules would automatically ban the IP for some time. A large part of the traffic from this botnet was actually blocked automatically by Deflect.
The second reason is that most websites using Deflect use the Banjax admin page protection, which requires an extra shared password to access administrator parts of a website (for WordPress, /wp-admin/)
Protection Against Bruteforce
The WordPress documentation describes several ways to protect your website against such brute-force attacks. The first one is to use a strong password, preferable a passphrase that would resist dictionary attacks used most of the time.
Many WordPress plugins also exist to ban an IP address after several failed attempts, like Brute Force Login Protection, Ninja Firewall or SiteGuard (see the full list of extensions here).
It is also possible to add an extra password (a bit like Banjax does) to the administration part of your website by using HTTP authentication. See the WordPress documentation for more information. (If you choose this option, it is recommended to install a tool preventing HTTP brute-force like fail2ban).
For professional WordPress hosting, a strong counter-measure to these attacks is to separate WordPress’ live PHP code from rendered WordPress code by hosting the administration part of the website on a different domain (for instance using django-wordpress). We plan to implement this strategy on our own WordPress hosting in the coming months.
Conclusion
In this blog post, we have described a botnet targeting WordPress website all around the world. The number of devices part of the attack is quite large (more than 3000), which shows that it is a well organized activity. We have no information on the malware used to compromise these devices or on the objective of this group. We are definitely interested to be in touch with anyone having more information about this group, or interest in continuing this investigation. Please contact us at outreach AT equalit.ie.
Appendix
Acknowledgement
We would like to thank member of the NGO ISAC, ipinfo.io and the Greynoise.io team for their support.
Indicators Of Compromise
You can look for the following indicators in your traffic :
- User-Agent :
Mozilla/5.0 (Windows NT 6.1; rv:52.0) Gecko/20100101 Firefox/52.0 - url:
POST /wp-login.phpandGET /?author=1(testing authors between 1 and 60)
We have no information on the post-compromise actions.
As with our last report, we have to not share public IP addresses used by this botnet, as they are likely compromised systems and we cannot control the potential side-effect of sharing these IP to owners of these systems. We are open to share them privately. We are aware of the challenges for sharing DDoS threat intelligence and we are also interested in starting a discussion about this topic. Please contact us at outreach AT equalit.ie.