Key Findings
- We identified 10 different DDoS attacks targeting two Vietnamese websites protected by Deflect, viettan.org and baotiengdan.com, between the 17th of April and 15th of June 2018. These attacks happened in the context of an important lack of Internet Freedom in Vietnam with regular online attacks against activists and independent media.
- We sorted these attacks in four different groups sharing the same Tactics, Techniques, and Procedures (TTPs). Group A is comprised of 6 different attacks, against both viettan.org and baotiengdan.com, which tend to show that these two websites have common enemies even if they have different political perspectives.
- We found common IPs between this group and a DDoS attack analyzed by Qurium in June 2018 against Vietnamese independent media websites luatkhoa.org and thevietnamese.org. Having four different Vietnamese civil society websites targeted by DDoS in the same period supports the hypothesis that these attacks are part of a coordinated action to silence NGOs and independent media in Vietnam.
- For each of the attacks covered in this report, we have investigated their origin and the systems used as relays.
Introduction
This blog post is the first in a series called “News from Deflect” intended to describe attacks on Deflect protected websites, with the objective of continuing discussions about distributed denial of service (DDoS) attacks against civil society.
Deflect is a free DDoS mitigation service for civil society organizations (see our Terms of Service to understand who fits into this description). Our platform is filtering traffic between users and civil society websites to remove malicious requests, in this case, bots trying to overload systems in order to make the website unavailable and silence political groups or independent media.
We have been protecting two Vietnamese websites, viettan.org and baotiengdan.com on the Deflect platform. Việt Tân is an organization seeking to establish democracy through political reforms in Vietnam. Tiếng Dân is an independent online non-partisan media covering political news in Vietnam.
Over the past several months, we have seen a significant increase of DDoS attacks against these two websites. Although Việt Tân and Tiếng Dân websites and organizations are not related to each other by any means and have different political perspectives, our investigations uncovered several attacks targeting them simultaneously. It appeared to us that these attacks are driven by a coordinated campaign and sought the websites’ agreement to publish an overview of the discovered activities.
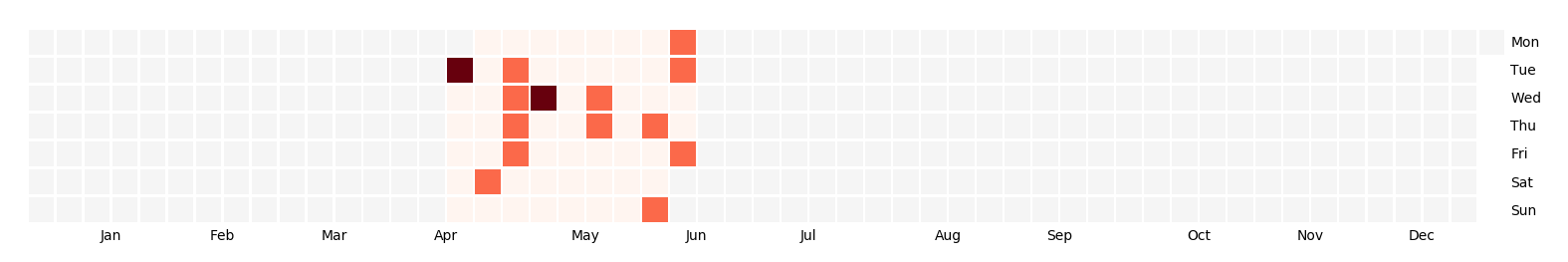 Figure 1: heatmap of DDoS incidents against Việt Tân and Tiếng Dân websites over the past months
Figure 1: heatmap of DDoS incidents against Việt Tân and Tiếng Dân websites over the past months
Internet and Media Freedom in Vietnam
For a more than a decade, there has been proof of online attacks against Vietnamese civil society. The earliest attacks we know focused on silencing websites either with DDoS attacks, like the attacks against the Bauxite Vietnam website in December 2009 and January 2010 or against Việt Tân in August 2011, or by compromising their platforms, as witnessed with Anh Ba Sam in 2013.
In 2013, the discovery by Citizen Lab of FinFisher servers installed in Vietnam indicated malware operations against activists and journalists. In March 2013, the managing editor of baotiengdan.com, Thu Ngoc Dinh, at that time managing editor of Anh Ba Sam, had her computer compromised and her personal pictures published online. Later that year, the Electronic Frontier Foundation documented a targeted malware operation against Vietnamese activists and journalists. This attack is now attributed to a group called OceanLotus (or APT32) that is considered to be Vietnam-based. Recently, an attack targeting more than 80 websites of civil society organizations (Human rights, independent media, individual bloggers, religious groups) was uncovered by Volexity in November 2017 and attributed to this same Ocean Lotus group.
At the same time, there is a strong suppression of independent media in Vietnam. Several articles in the Vietnamese constitution criminalize online publications opposing the Socialist Republic of Vietnam. They have been used regularly to threaten and condemn activists, like the blogger Nguyen Ngoc Nhu Quynh, alias ‘Mother Mushroom’ who was sentenced to 10 years in jail for distorting government policies and defaming the communist regime in Facebook posts in June 2017. Recently, Vietnamese legislators approved a cyber-security law requiring large IT companies like Facebook or Google to store locally personal data on users in Vietnam. This law has seen strong opposition by street protests and by human rights groups like Human Rights Watch and Amnesty International.
Vietnam is ranked 175th over 180 countries by Reporters without Border’s 2018 World Press Freedom Index and has a Freedom of the Net score of 75/100 in the Freedom of the Net report in 2017 by Freedom House.
10 different DDoS attacks
Since the 17th of April 2018, we have identified 10 different DDoS attacks targeting either Việt Tân or Tiếng Dân’s websites :
| Date | Target | |
|---|---|---|
| 1 | 2018/04/17 | viettan.org |
| 2 | 2018/04/17 | baotiengdan.com |
| 3 | 2018/05/04 | viettan.org |
| 4 | 2018/05/09 | viettan.org |
| 5 | 2018/05/09 | baotiengdan.com |
| 6 | 2018/05/23 | baotiengdan.com |
| 7 | 2018/06/07 | baotiengdan.com |
| 8 | 2018/06/10 | baotiengdan.com |
| 9 | 2018/06/12 | viettan.org |
| 10 | 2018/06/15 | baotiengdan.com |
These attacks were all HTTP flood attacks but came from different sources and with different characteristics (user agents, path requested etc.).
Identifying Groups of Attacks
From the beginning of the analysis, we saw some similarities between the different attacks, mainly through the user agents used by different bots, or the path requested. We quickly wanted to identify groups of attacks sharing the same Tactics, Techniques and Procedures (TTP).
We first described their characteristics in the following table :
| id | Target | Start time | End Time | #IP | #Hits | Path | User Agent | Query String |
|---|---|---|---|---|---|---|---|---|
| 1 | viettan.org | 2018-04-17 08:20:00 | 2018-04-17 09:10:00 | 294 | 63 830 | / | On random UA per IP | None |
| 2 | baotiengdan.com | 2018-04-17 8:30:00 | 2018-04-17 10:00:00 | 568 | 33 589 | / | One random UA per IP | None |
| 3 | viettan.org | 2018-04-28 00:00:00 | 2018-05-04 15:00:00 | 5001 | 2 257 509 | / or /spip.php | Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2) | if spip, /spip.php?page=email&id_article=10283 |
| 4 | viettan.org | 2018-05-09 02:30:00 | 2018-05-09 03:20:00 | 217 | 58 271 | / | One UA per IP | None |
| 5 | baotiengdan.com | 2018-05-09 08:30:00 | 2018-05-09 11:30:00 | 725 | 235 157 | / | One or several UA per IP | None |
| 6 | baotiengdan.com | 2018-05-23 15:00:00 | 2018-05-24 09:30:00 | 557 | 2 957 065 | / | One random UA per IP | None |
| 7 | baotiengdan.com | 2018-06-07 01:45:00 | 2018-06-07 05:30:00 | 70 | 17 131 | / | One random UA per IP | None |
| 8 | baotiengdan.com | 2018-06-10 05:45:00 | 2018-06-11 06:30:00 | 349 | 5 214 730 | / | python-requests/2.9.1 | ?&s=nguyenphutrong and random like |
| 9 | viettan.org | 2018-06-12 05:00:00 | 2018-06-12 06:30:00 | 1 | 9 978 | / | 329 different user agents | Random like ?x=%99%94%7E%85%7B%7E%8D%96 |
| 10 | baotiengdan.com | 2018-06-15 13:00:00 | 2018-06-15 23:00:00 | 1 | 518 899 | / | python-requests/2.9.1 | ?s=nguyenphutrong |
From this table, we can see that Incidents 8 and 10 clearly use the same tool identified by the user agent (python-requests/2.9.1) and do the same specific query /?&s=nguyenphutrong based on the name of Nguyễn Phú Trọng, the current General Secretary of the Communist Party of Vietnam. We gathered these two attacks in Group C.
Incidents 3 and 9 have different characteristics from other incidents, they seem to use two different custom-made tools for DDoS. We separated them into two different groups, B and D (see details in part 2).
We still have 6 different attacks that share common characteristics but not enough to confirm any linkages between them. They all query / without any query string, which is quite common in DDoS attacks. They use random User-Agents for each IP address, which is close to what legitimate traffic looks like.
Identifying shared IPs
We wanted to check if these different attacks were sharing IP addresses so we represented both IPs and Incidents in a Gephi graph to visualize the links between them (IPs are represented with red dots and incidents with green dots in the following figure) :
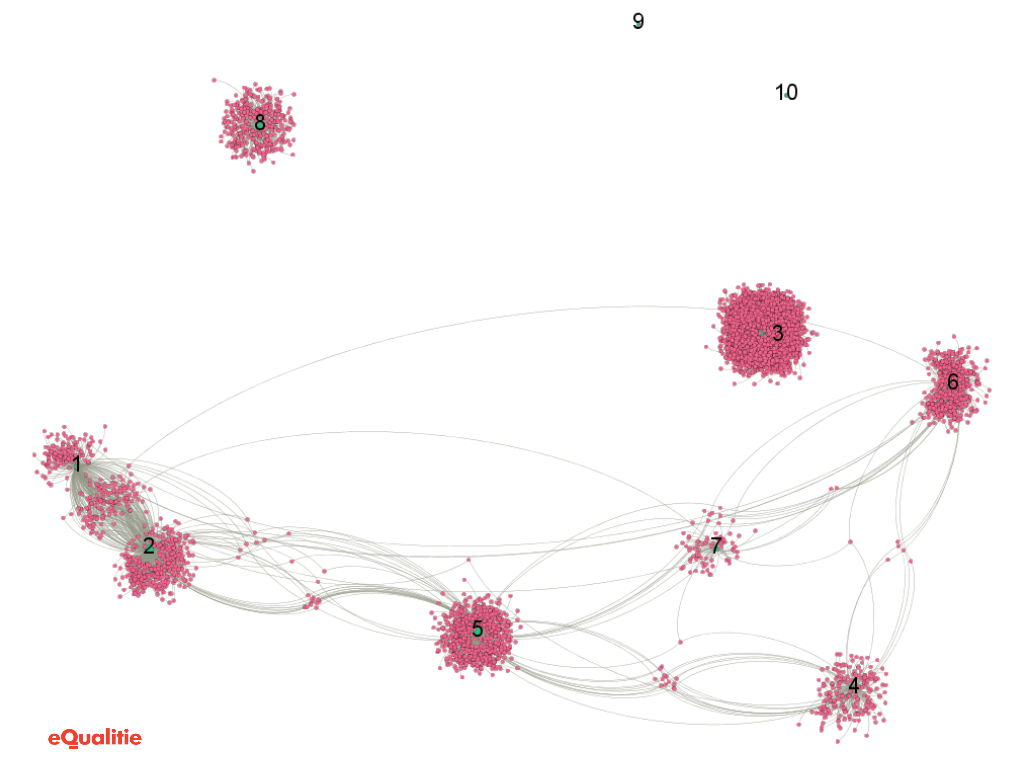
We have identified six incidents sharing common IPs in their botnets, and present them in the following table of Incident intersection IPs:
| incidents | Number of IPs | Intersection IP | % of total botnet IPs |
|---|---|---|---|
| 6 & 1 | 557 & 294 | 5 | 1.70 % |
| 6 & 4 | 557 & 217 | 6 | 2.76 % |
| 6 & 7 | 557 & 70 | 3 | 4.29 % |
| 6 & 5 | 557 & 725 | 8 | 1.44 % |
| 6 & 2 | 557 & 568 | 1 | 0.18 % |
| 1 & 4 | 294 & 217 | 1 | 0.46 % |
| 1 & 7 | 294 & 70 | 2 | 2.86 % |
| 1 & 5 | 294 & 725 | 9 | 3.06 % |
| 1 & 2 | 294 & 568 | 155 | 52.72 % |
| 4 & 7 | 217 & 70 | 2 | 2.86 % |
| 4 & 5 | 217 & 725 | 14 | 6.45 % |
| 4 & 2 | 217 & 568 | 1 | 0.46 % |
| 7 & 5 | 70 & 725 | 1 | 1.43 % |
| 7 & 2 | 70 & 568 | 1 | 1.43 % |
| 5 & 2 | 725 & 568 | 22 | 3.87 % |
There is a strong overlap of bots used in Incidents 1 and 2 (53%), which is telling considering that Incident 1 is targeting viettan.org and incident 2 is targeting baotiengdan.com. Its is a strong indication that a similar botnet was used to attack these two domains, particularly as the attacks were orchestrated at the same on April 17th.
Other attacks all share between 1 and 22 IP addresses in common (<10%) which is a quite small percentage of intersection and may have different explanations. For instance, the same system is compromised by several different malware turning them into bots, or that different compromised systems are behind the same public IP.
Identifying origin countries
Another link to consider is if these IPs used for different attacks are from the same countries. If we consider a botnet that would use specific ways to infect end systems, it is likely that they would be unevenly distributed over the world. For instance a phishing attack in one language would be more efficient in a country speaking this language, or an Internet wide scan for vulnerable routers would compromise more devices in countries using the targeted router.
We have geolocated these IPs using MaxMind GeoLite database and represented the origin in the following graph (countries having less than 5% IPs are categorized as “Other” for visibility) :
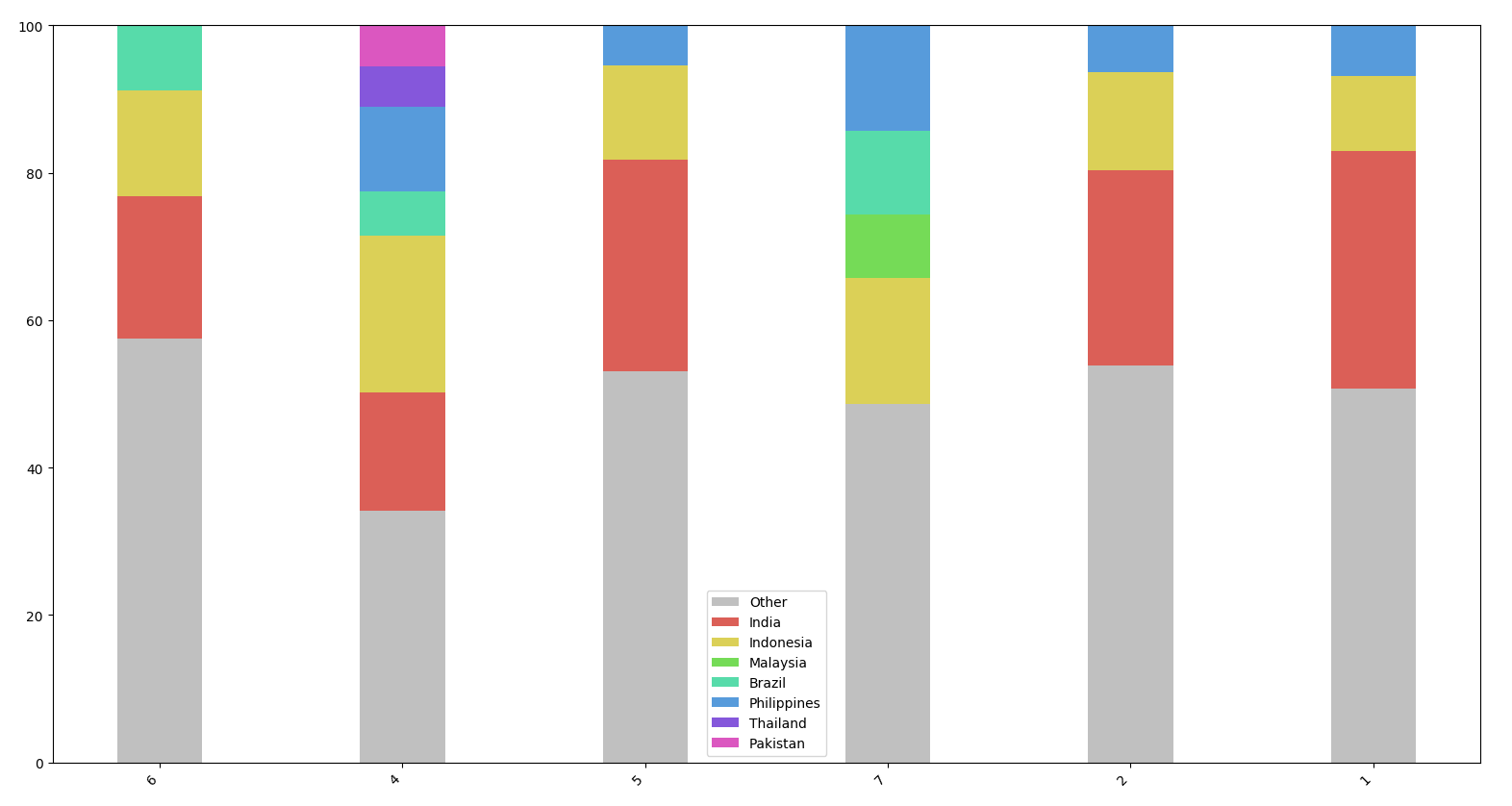
Besides Incident 7, these attacks clearly share the same profile : between 15 and 30% of IPs are from India, between 5 and 10% from Indonesia, then Philippines or Malaysia. Surprisingly, the 7th incident has only one IP coming from India (categorised as Other in this graph) but has a similar distribution in other countries. So the distribution seems quite similar.
Analyzing User-Agents
Another interesting characteristic of these attacks is that every IP is using a single user agent for all of its requests, presumably selected from a list of predefined user-agents. We listed User-Agents used in different incidents and checked the similarity between these lists :
| incidents | Number of UA | Number of identical UA | Percentage |
|---|---|---|---|
| 6 & 2 | 68 & 40 | 29 | 72.50 % |
| 6 & 1 | 68 & 54 | 32 | 59.26 % |
| 6 & 5 | 68 & 97 | 40 | 58.82 % |
| 6 & 4 | 68 & 57 | 32 | 56.14 % |
| 6 & 7 | 68 & 38 | 34 | 89.47 % |
| 2 & 1 | 40 & 54 | 23 | 57.50 % |
| 2 & 5 | 40 & 97 | 27 | 67.50 % |
| 2 & 4 | 40 & 57 | 17 | 42.50 % |
| 2 & 7 | 40 & 38 | 27 | 71.05 % |
| 1 & 5 | 54 & 97 | 32 | 59.26 % |
| 1 & 4 | 54 & 57 | 29 | 53.70 % |
| 1 & 7 | 54 & 38 | 28 | 73.68 % |
| 5 & 4 | 97 & 57 | 34 | 59.65 % |
| 5 & 7 | 97 & 38 | 31 | 81.58 % |
| 4 & 7 | 57 & 38 | 24 | 63.16 % |
Between 42 and 81% of user-agents are shared between every set of two incidents. Low intersections between two incidents could be due either to different versions of the same tool used in different attacks, or to interference with legitimate traffic.
15 different user agents were used in all of the 6 incidents:
| User-Agent | Description |
|---|---|
| Mozilla/5.0 (Windows NT 5.1; rv:5.0.1) Gecko/20100101 Firefox/5.0.1 | Firefox 5 on Windows XP |
| Mozilla/5.0 (X11; U; Linux x86_64; de; rv:1.9.2.8) Gecko/20100723 Ubuntu/10.04 (lucid) Firefox/3.6.8 | Firefox 3.6 on Ubuntu Linux 10 |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.116 Safari/537.36 | Chrome 53 on Windows 10 |
| Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.116 Safari/537.36 | Chrome 53 on Windows 7 |
| Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36 | Chrome 45 on Windows 7 |
| Mozilla/5.0 (Windows NT 6.3; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0 | Firefox 41 on Windows 8.1 |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.84 Safari/537.36 | Chrome 63 on Windows 10 |
| Mozilla/5.0 (Windows NT 6.1; WOW64; rv:41.0) Gecko/20100101 Firefox/41.0 | Firefox 41 on Windows 7 |
| Mozilla/5.0 (Windows NT 6.0) AppleWebKit/535.1 (KHTML, like Gecko) Chrome/13.0.782.112 Safari/535.1 | Chrome 13 on Windows Vista |
| Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.116 Safari/537.36 | Chrome 53 on Mac OS X (El Capitan) |
| Mozilla/5.0 (Windows NT 6.1; WOW64; rv:13.0) Gecko/20100101 Firefox/13.0.1 | Firefox 13 on Windows 7 |
| Mozilla/5.0 (Windows NT 6.1; rv:5.0) Gecko/20100101 Firefox/5.02 | Firefox 5 on Windows 7 |
| Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.132 Safari/537.36 | Chrome 63 on Windows 7 |
| Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.116 Safari/537.36 | Chrome 53 on Windows 10 |
| Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko | Internet Explorer 11 on Windows 7 |
Analyzing Traffic Features
For a long-time, we have been using visualization and machine learning tools to analyze DDoS attacks (for instance in the report on attacks against Black Lives Matter). We find it is more reliable to consider information about the whole session of an IP (all the requests done by an IP over a period of time) rather than per request. So we generate features describing each IP session and then visualize and cluster these IPs to identify bots. This approach is really interesting to confirm the link between these different attacks, here were are relying on the four following features to compare the sessions from the different groups:
- Number of different user-agents used
- Number of different query strings done
- Number of different paths queried
- Size of the requests
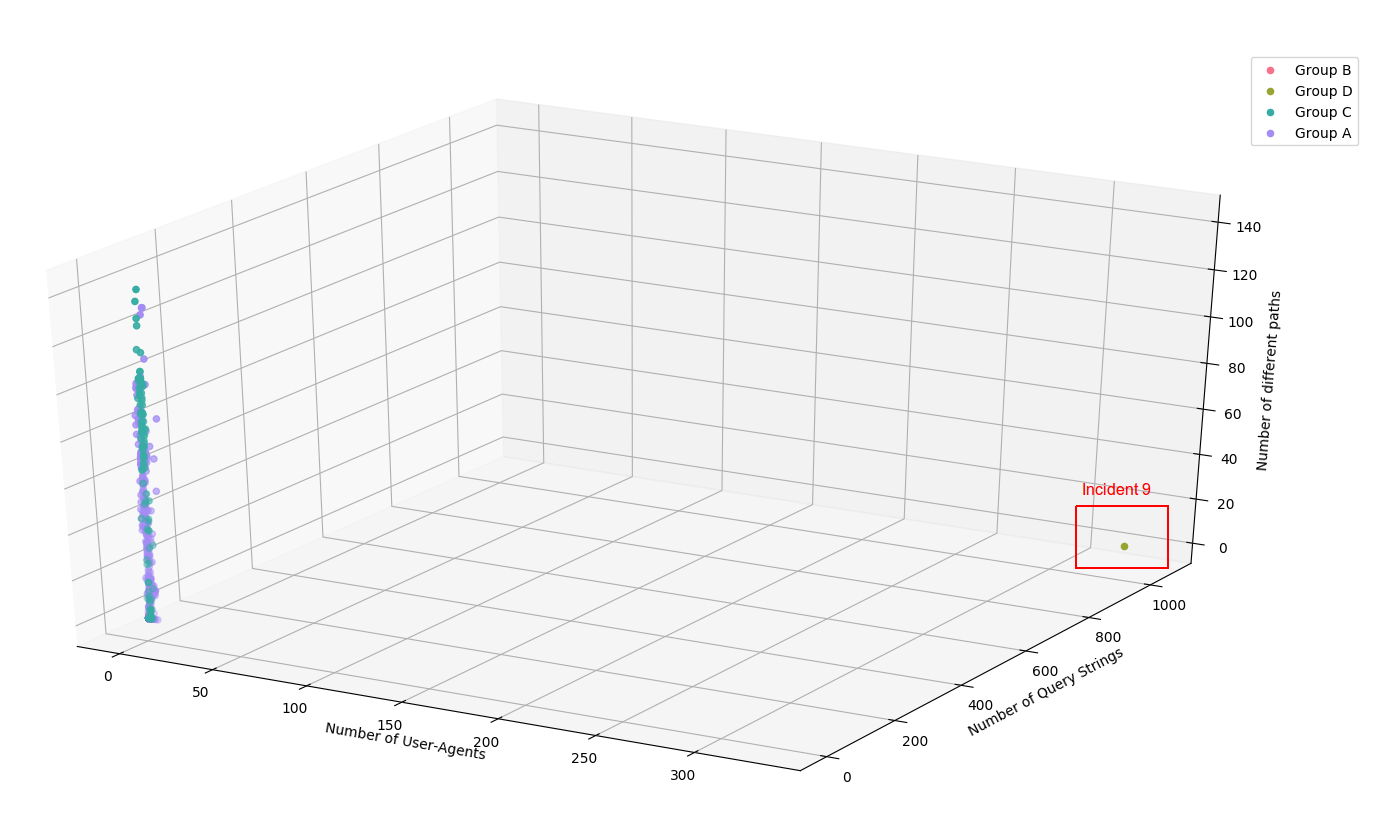
First, we can clearly see that the Incident 8 has an identifiable signature due to the utilization of a specifically crafted tool generating random user agent and random query strings (1058 query strings and 329 user-agents) :
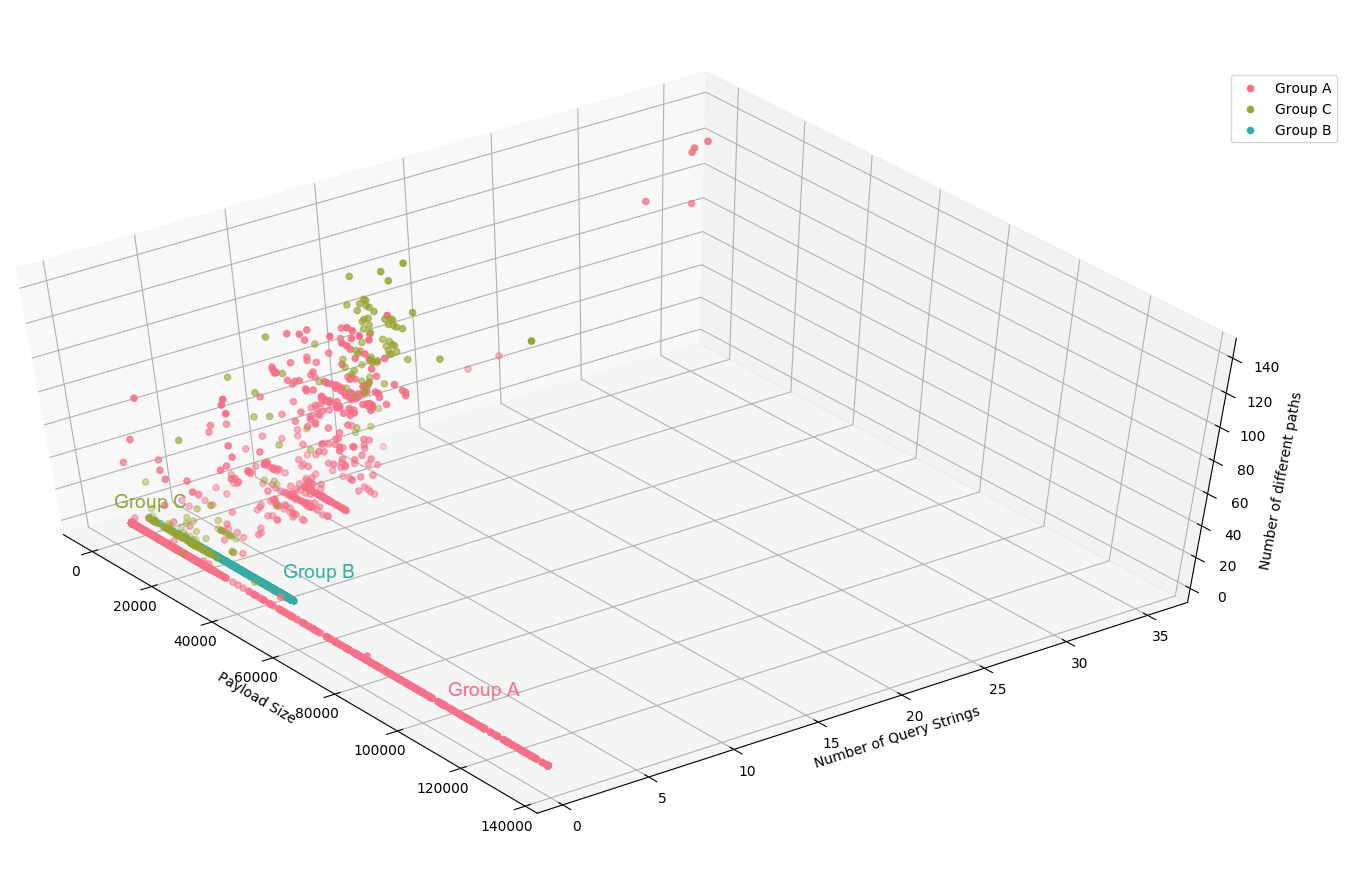
Considering other attacks now, the identification is not that clear, mainly because some IPs seems to do both legitimate visits of the website and attacks at the same time. But for most of the IPs, we clearly see that the number of query string and the payload size is discriminant :
Summary of the Different Attack Groups
Overall, we identified four different groups of attacks sharing the Same TTPs :
| Date | Target | Attack Group | |
|---|---|---|---|
| 1 | 2018/04/17 | viettan.org | Group A |
| 2 | 2018/04/17 | baotiengdan.com | Group A |
| 3 | 2018/05/04 | viettan.org | Group B |
| 4 | 2018/05/09 | viettan.org | Group A |
| 5 | 2018/05/09 | baotiengdan.com | Group A |
| 6 | 2018/05/23 | baotiengdan.com | Group A |
| 7 | 2018/06/07 | baotiengdan.com | Group A |
| 8 | 2018/06/10 | baotiengdan.com | Group C |
| 9 | 2018/06/12 | viettan.org | Group D |
| 10 | 2018/06/15 | baotiengdan.com | Group C |
Let’s enter into the detail of TTP for each group :
- Group A : TTPs for this group seem to be quite generic and we have only a moderate confidence that the attacks are linked. All these attacks are querying
/(which is pretty common) with on user agent per IP (regularly an empty user agent). The IPs from these groups are coming from Asia, mostly India, Indonesia, Philippines or Malaysia. Attacks in this group are often reusing the same user-agents which could indicate several versions of the same payload. - Group B : this attack used the user-agent
Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2)to query eitherGET /orPOST /spip.php?page=email&id_article=10283 - Group C : two attacks with the user-agent
python-requests/2.9.1(showing the utilization of a python script with the requests library) querying either/?&s=nguyenphutrongor a random search term like/?s=06I44M - Group D : One attack with a tool using a random value among a list of 329 user-agents, and random query strings (like
?x=%99%94%7E%85%7B%7E%8D%96) to bypass caching
Analyzing Attack Groups
Group A
Group A attacks were definitely the most frequent case we saw since April, with six different attacks done on both Việt Tân and Tiếng Dân’s websites.
Two simultaneous incidents
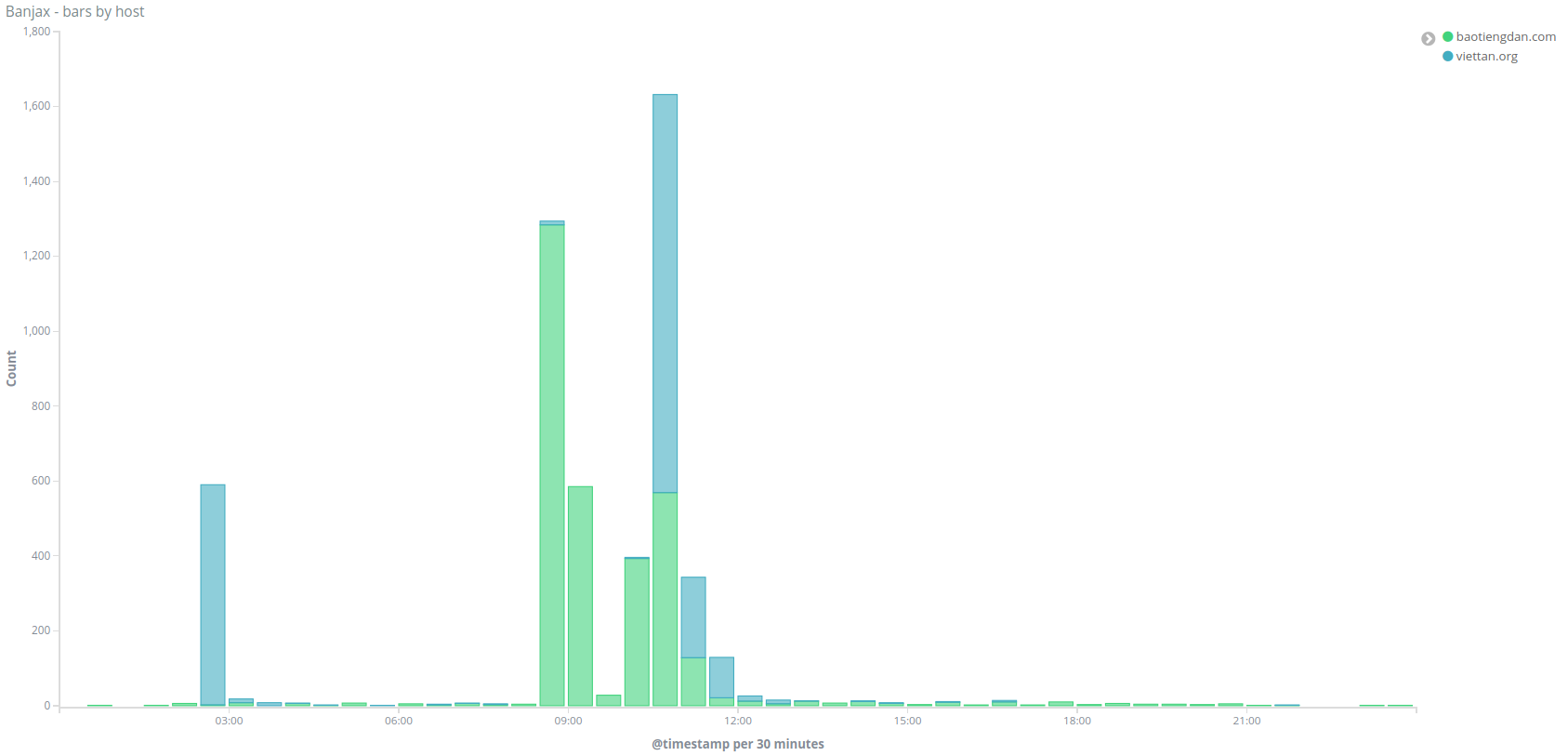
On the 9th of May for instance, we saw a peak of banned IPs first on attacks against viettan.org, then baotiengdan.com :
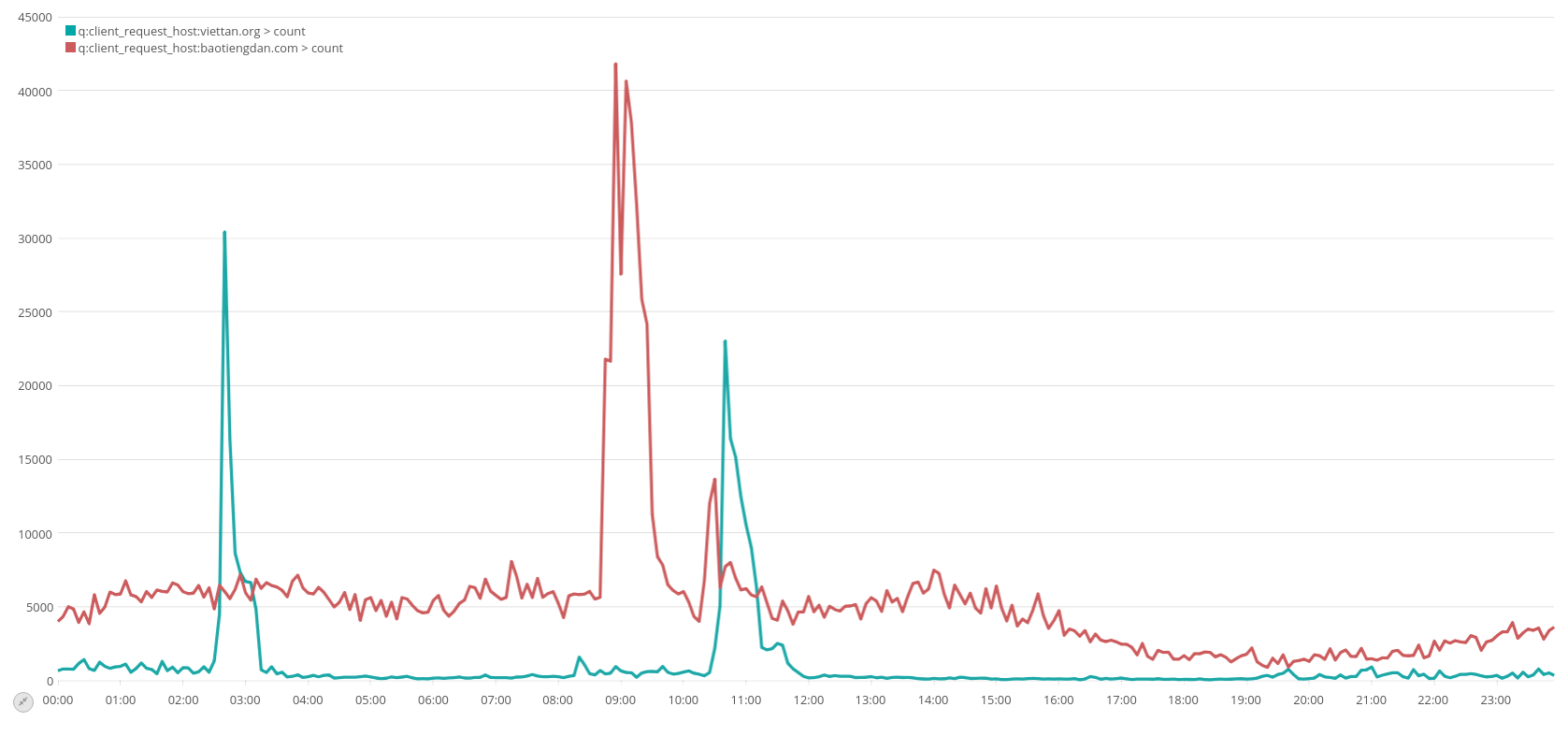
We can confirm that there was also a peak of traffic to both websites :
Looking at the traffic more closely, we see that the majority of IPs generating most of the traffic are only making requests to the / path, like this IP 61.90.38.XXX which did 4253 GET requests to/ with user agent Mozilla/5.0 (Windows NT 6.1; WOW64; rv:13.0) Gecko/20100101 Firefox/13.0.1 (this user agent means that the request came from a Firefox 13 browser on Windows 7, Firefox 13 was released in April 2012, it is pretty unlikely to see people using it today) over 30 minutes :
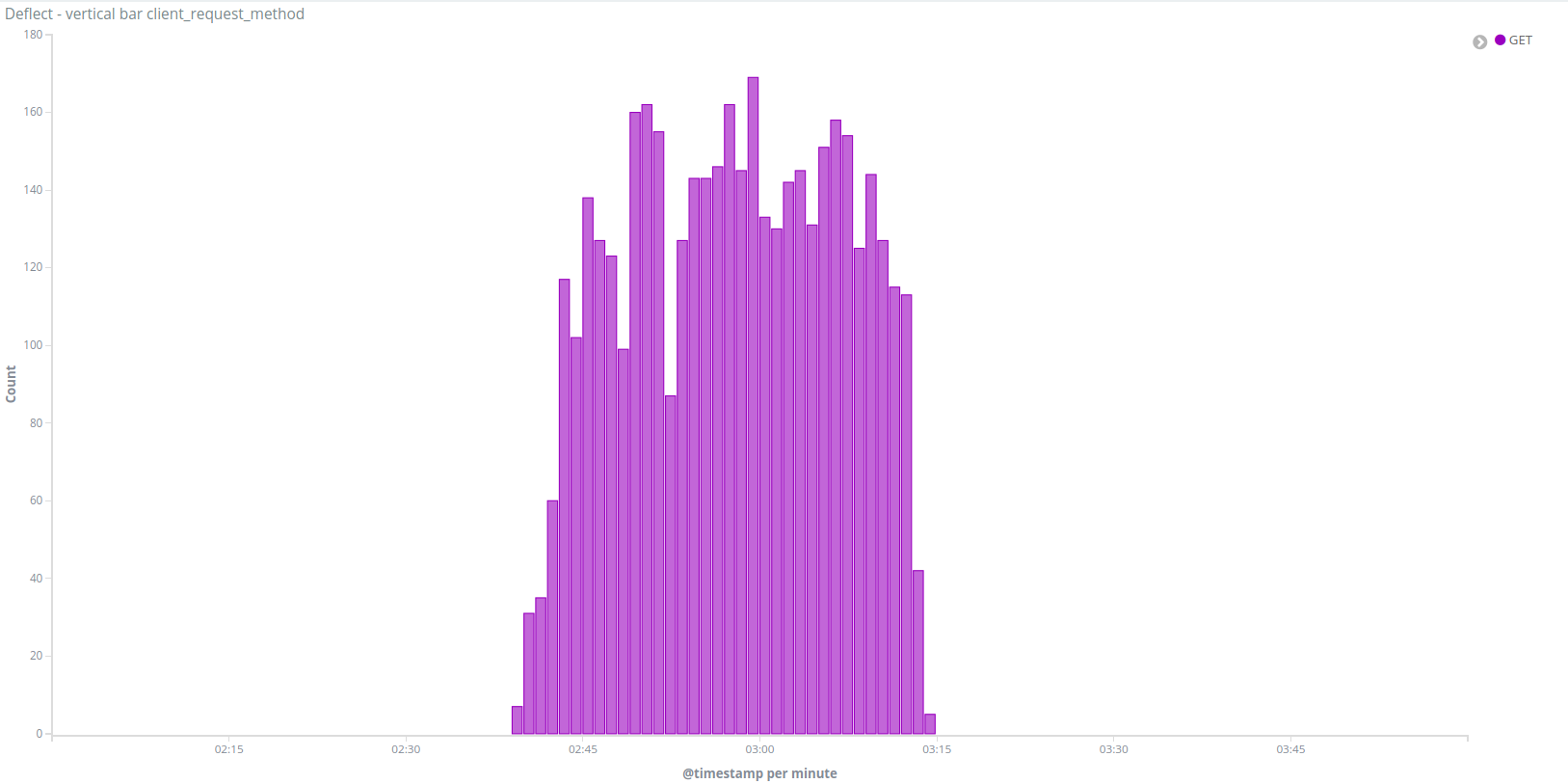
We identified as bots all the IPs displaying an unusual number of queries to “/” (more than 90% of their traffic), and ended up with a list of 217 IPs targeting viettan.org and 725 IPs targeting baotiengdan.com, with 14 in common between both incidents.
Checking where these IPs are located, we can see that they are mainly in India and Indonesia :
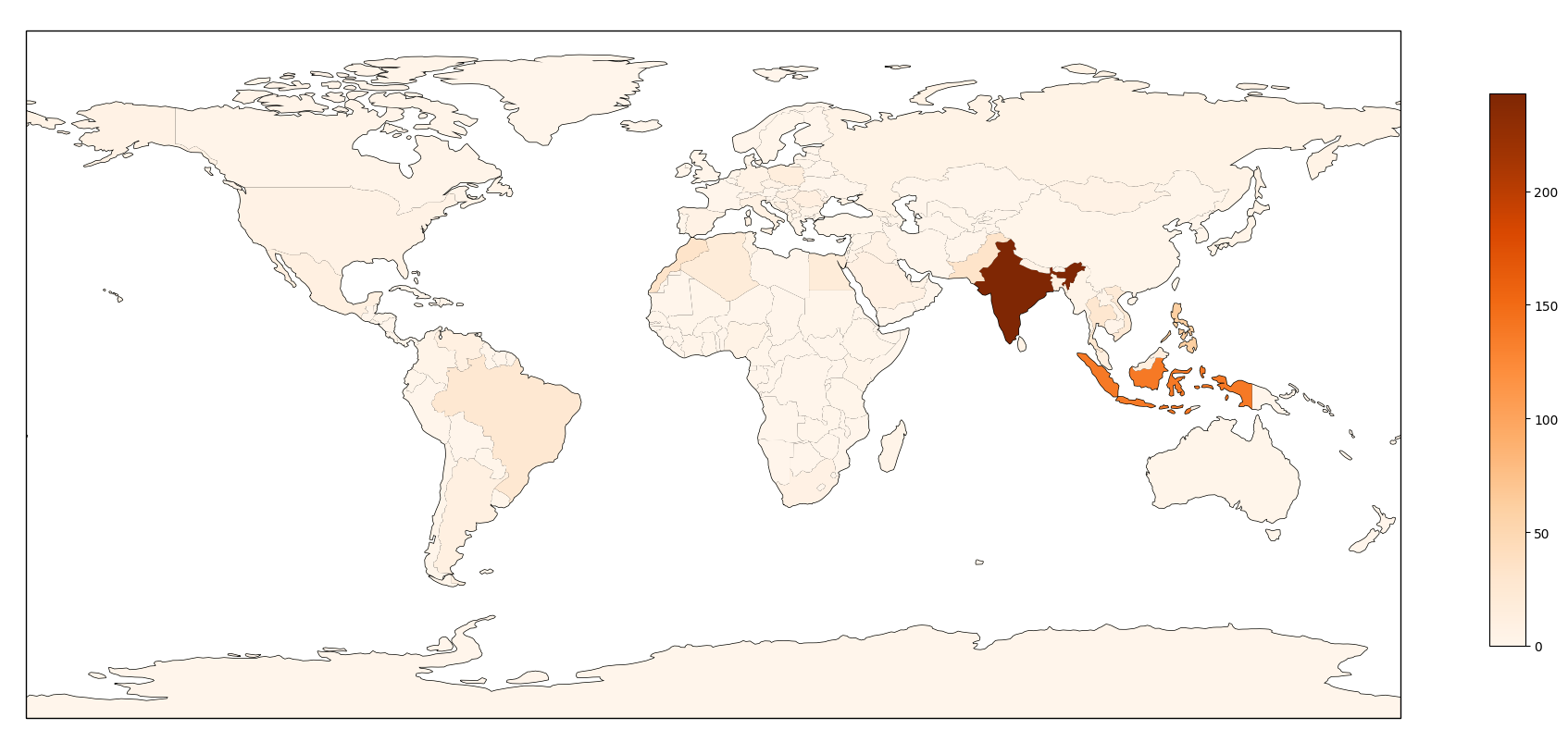
Top 10 countries :
- 243 India
- 138 Indonesia
- 61 Philippines
- 34 Morocco
- 34 Pakistan
- 29 Thailand
- 27 Brazil
- 22 Vietnam
- 19 Algeria
- 19 Egypt
Analyzing the source of these incidents
We then wanted to understand what is the source of these incidents and we have four major hypothesis :
- Servers rented by the attackers
- Compromised Servers
- Compromised Routers
- Compromised end-points (Windows workstations, android phones etc.)
We aggregated the 2212 IP addresses of these 6 incidents and identified their Autonomous System. To distinguish between servers and internet connections, we used ipinfo.io classification of Autonomous Systems :
- 1988 ISP
- 163 business
- 38 hosting
- 23 Unknown
This set of IPs is then mostly coming from personal Internet access networks around the world, either from compromised routers or compromised end-devices. For a long time, most botnets were comprised of compromised Windows systems infected through worms, phishing or backdoored applications. Since 2016 and the appearance of the Mirai botnet it is clear that Internet-Of-Things botnets are becoming more and more common and we are are seeing compromised routers or compromised digital cameras being used for DDoS attacks regularly.
The main difference between these two cases, is that IoT systems are reachable from the Internet and often compromised through open ports. To differentiate these two cases, we used data from the Shodan database. Shodan is a platform doing regular scans of all IPv4 addresses, looking for specific ports (most of them specific to IoT devices) and storing the results in a database that you can query through their search engine or through their API. We have implemented a script querying the Shodan API and using signatures over the results to fingerprint systems running on the IP address. For instance MikroTik routers often expose either a telnet, SNMP or web server showing the brand of the router. Our script downloads data from Shodan for an IP, and checks if there are matches on different signatures from MikroTik routers. Shodan allows to get historical data for these scans, so we included data for the past 6 months for each IP in order to maximize information to fingerprint the system.
There are definitely limitations to this approach as a MikroTik router could be secure but routing traffic from a compromised end-system. But our hypothesis is that we would identify similar routers or IoT systems for a large part of IP address in the case of an IoT botnet.
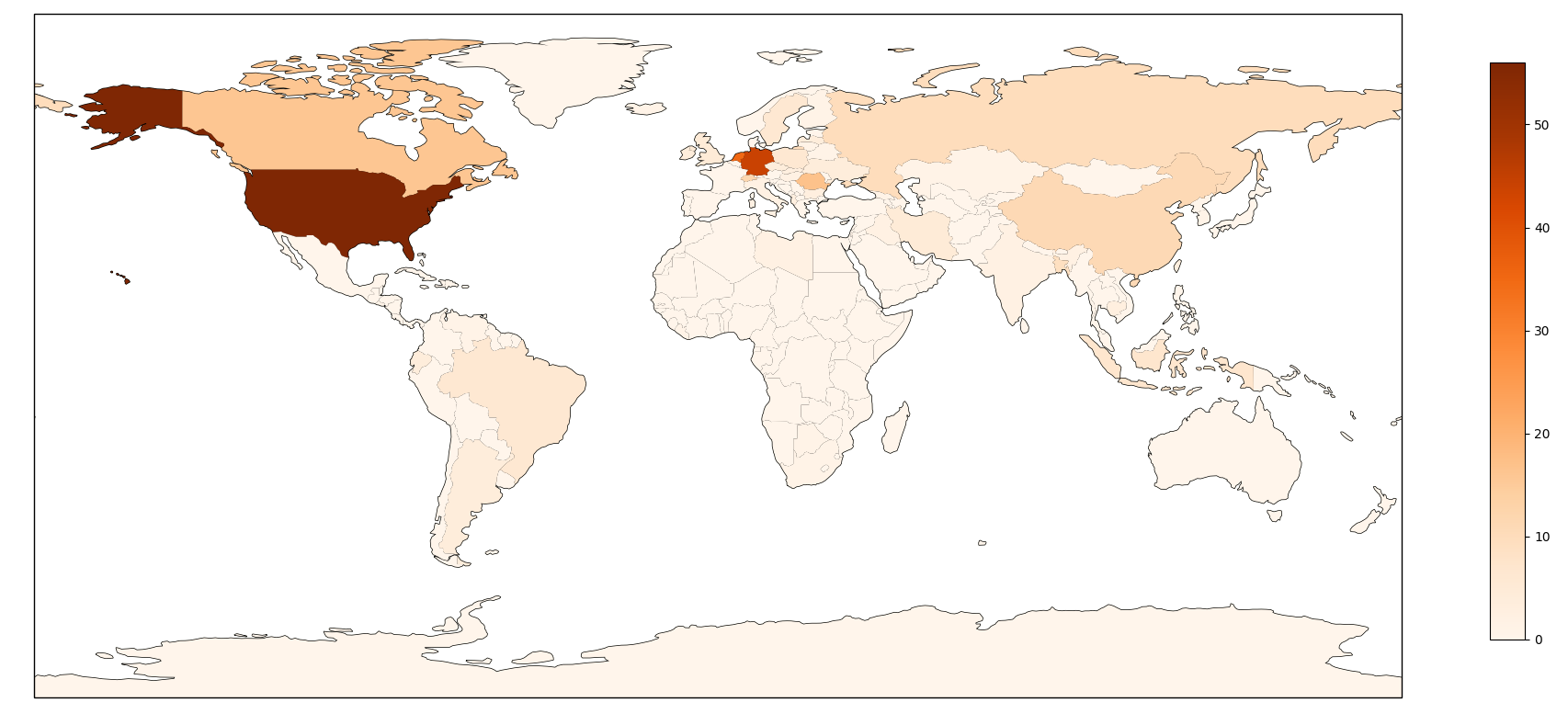
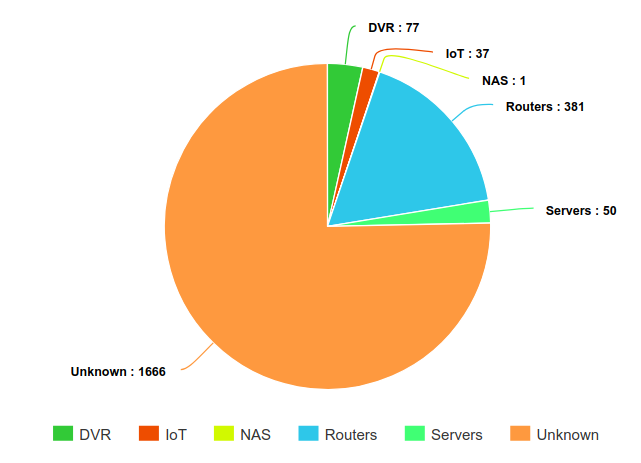
By running this script over 2212 IP addresses for the group A, we identified 381 routers, 77 Digital Video Recorders and 50 routers over 2212 IPs. 1666 of them did not have any open port according to Shodan, which tends to show that they were not servers but rather professional or personal Internet access points. So in the end, our main hypothesis is that these IPs are mostly compromised end-systems (most likely Windows systems).
Regarding location, we used MaxMind Free GeoIP database to identify the source country, and found that 50% of the IPs are located in India, Indonesia, Brazil, Philippines, and Pakistan.
Group B
The second group was responsible for one DDoS attack against Viettan.org from the 29th of April to the 4th of May using 5000 different IP addresses :
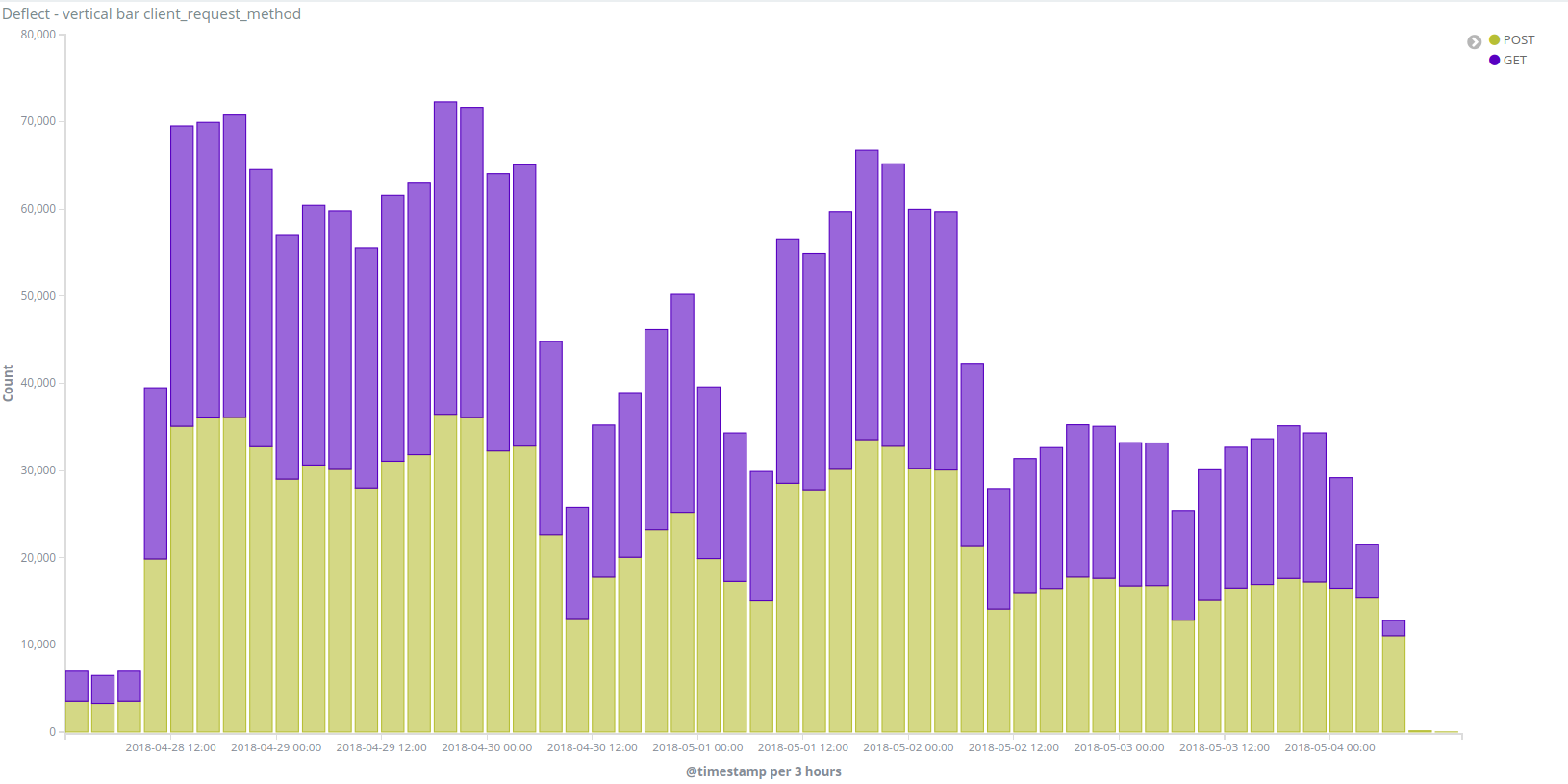
The attack tool has specific characteristics :
- All bots were using the same User-Agent :
Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2) - Bots were querying only two different paths
- GET
/ - POST
/spip.php?page=email&id_article=10283It seems to query a page on the web framework SPIP which could exploiting a known SPIP vulnerability but it is curious as viettan.org is not running SPIP
- GET
If we look at the Autonomous System of each IP, we see that 97.7% of them are coming from the AS 4134 which belongs to the state-owned company China Telecom for Internet access in China :
- 4885 ASN4134 CHINANET-BACKBONE No.31,Jin-rong Street, CN
- 42 ASN62468 VPSQUAN – VpsQuan L.L.C., US
- 40 ASN55933 CLOUDIE-AS-AP Cloudie Limited, HK
- 20 ASN53755 IOFLOOD – Input Output Flood LLC, US
- 5 ASN38197 SUNHK-DATA-AS-AP Sun Network (Hong Kong) Limited – HongKong Backbone, HK
- 3 ASN45102 CNNIC-ALIBABA-CN-NET-AP Alibaba (China) Technology Co., Ltd., CN
- 2 ASN9902 NEOCOMISP-KH-AP NEOCOMISP LIMITED, IPTX Transit and Network Service Provider in Cambodia., KH
- 1 ASN9873 TELECOM-LA-AS-AP Lao Telecom Communication, LTC, LA
- 1 ASN132839 POWERLINE-AS-AP POWER LINE (HK) CO., LIMITED, HK
- 1 ASN58879 ANCHNET Shanghai Anchang Network Security Technology Co.,Ltd., CN
We fingerprinted the systems using the Shodan-based tool described in 2.1, and identified 901 systems as routers (884 of them being Mikrotik routers), and 512 systems as servers (mostly Windows servers and Ubuntu servers)
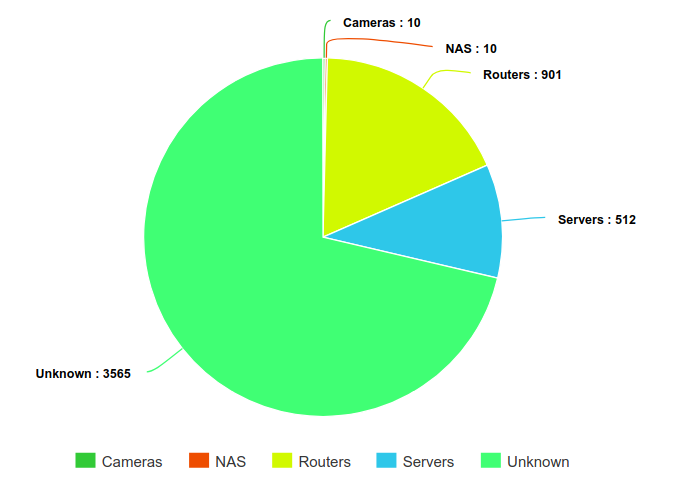
It is interesting to see Mikrotik routers here as many people observed botnets compromising MikroTik routers back in March this year exploiting some known vulnerabilities. But still, having 884 MikroTik routers only represent 17.6% of the total number of IPs involved in this attack. Our main hypothesis is that this botnet is mostly comprised of compromised end-systems (Windows or Android likely). It is also possible that we have here a botnet using a mix of compromised end-systems and compromised MikroTik routers.
The most surprising specificity of this botnet is that it is coming almost only from one Autonomous System, AS4134, which is not common in DDoS attacks (most of the times targets are distributed over different countries). A third hypothesis is that this traffic could come from traffic injection by the Internet Service Provider in order to cause clients to do requests to this website. Such attack was already identified once by Citizen Lab in 2015 in their China’s Great Cannon report against github.com and GreatFire.org. We consider this third hypothesis unlikely as this 2015 attack is the only documented case of such an attack, and it would require a collaboration between Vietnamese groups likely at the origin of these attacks and this Chinee state-owned Internet provider, for a costly attack with little to no impact on the targeted website.
Group C
The third group consists of two attacks targeting baotiengdan.com on the 10th and the 15th of June, using a specially crafted tool. We identified it first on the 10th of June 2018 when a peak of traffic created issues on the website. We quickly identified that there was an important number of requests done from different IPs all with the same user agent python-requests/2.9.1
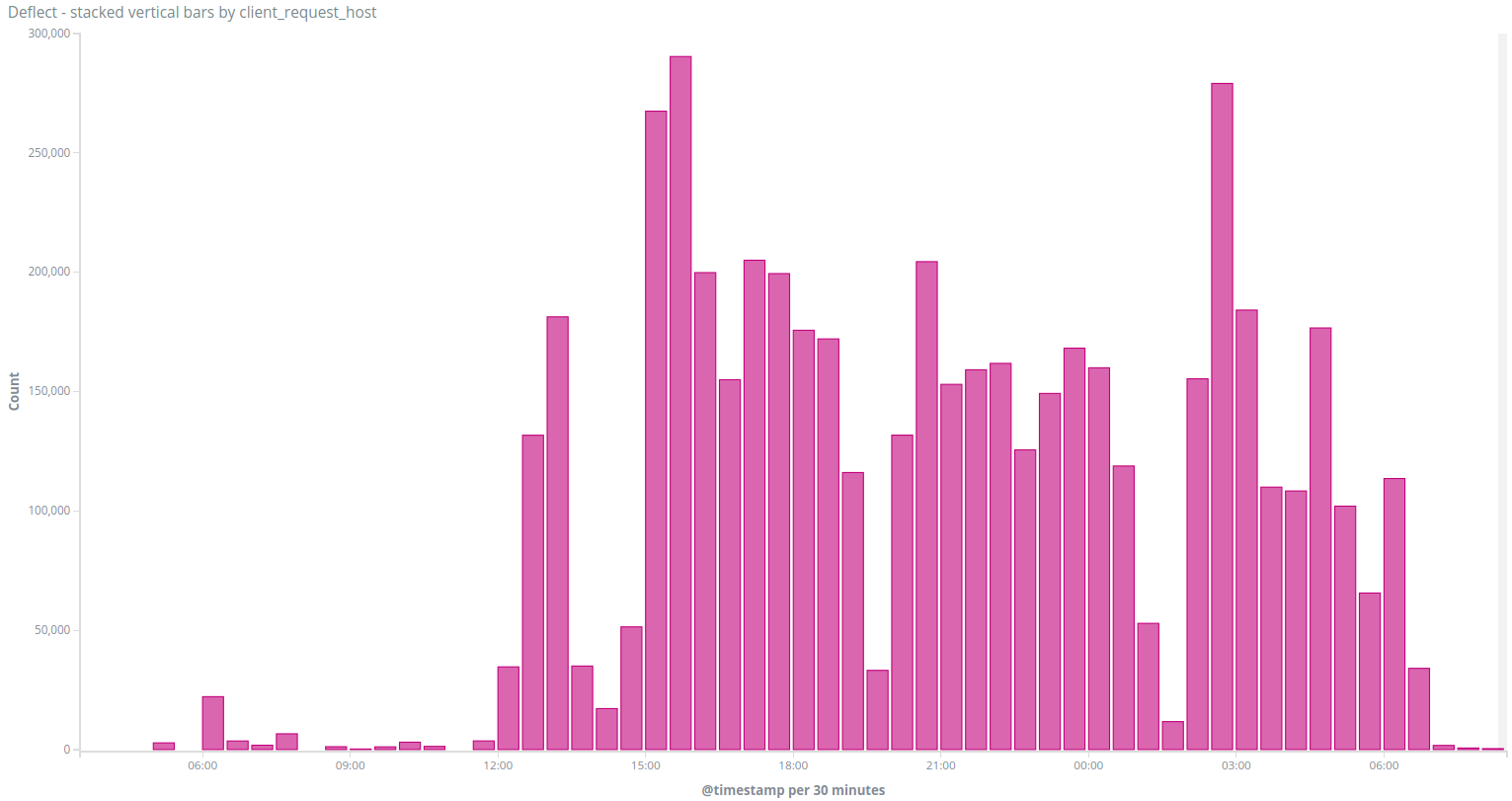
Over 5 million requests were done that day by 349 IP addresses. In order to bypass the caching done by Deflect, the bots were configured to query the search page, half of them with the same query /?&s=nguyenphutrong, which is a research for the name of Nguyen Phú Trọng , the actual General Secretary of the Communist Party of Vietnam. The other half of bots were doing random search queries like ?s=046GYH or ?s=04B9BV.
These 349 IPs were distributed in different countries (top 10 only mentioned here):
- 56 United States
- 43 Germany
- 35 Netherlands
- 30 France
- 17 Romania
- 16 Canada
- 12 Switzerland
- 11 China
- 10 Russia
- 9 Bangladesh
Looking more closely at the hosts, we identified that 180 of them are actually Tor Exit Nodes (the list of tor exit nodes is public). We used the same fingerprint technique based on Shodan to identify the other hosts and found that 89 of them are routers (mostly MikroTik routers) and 51 servers :
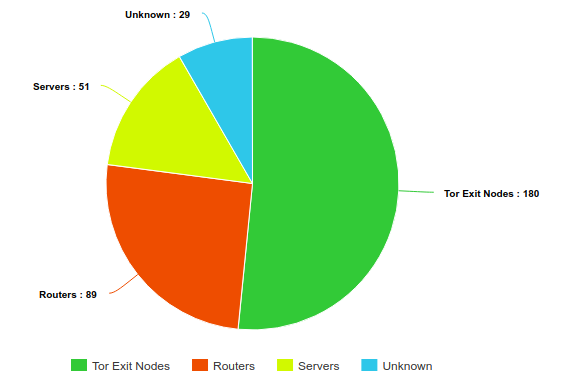
This mix of routers and servers is confirmed by ipinfo.io AS Classification on these non-Tor IPs:
- 68 ISP
- 52 Hosting
- 42 Business
- 7 Unknown
So this attack used two different types of relays at the same time: the Tor network and compromised systems, routers or servers.
The second attack by this group was surprisingly different, we identified a peak of traffic on the 15th of June on baotiengdan.com again, coming from a single IP 66.70.255.195 which did 560 030 requests over a day:
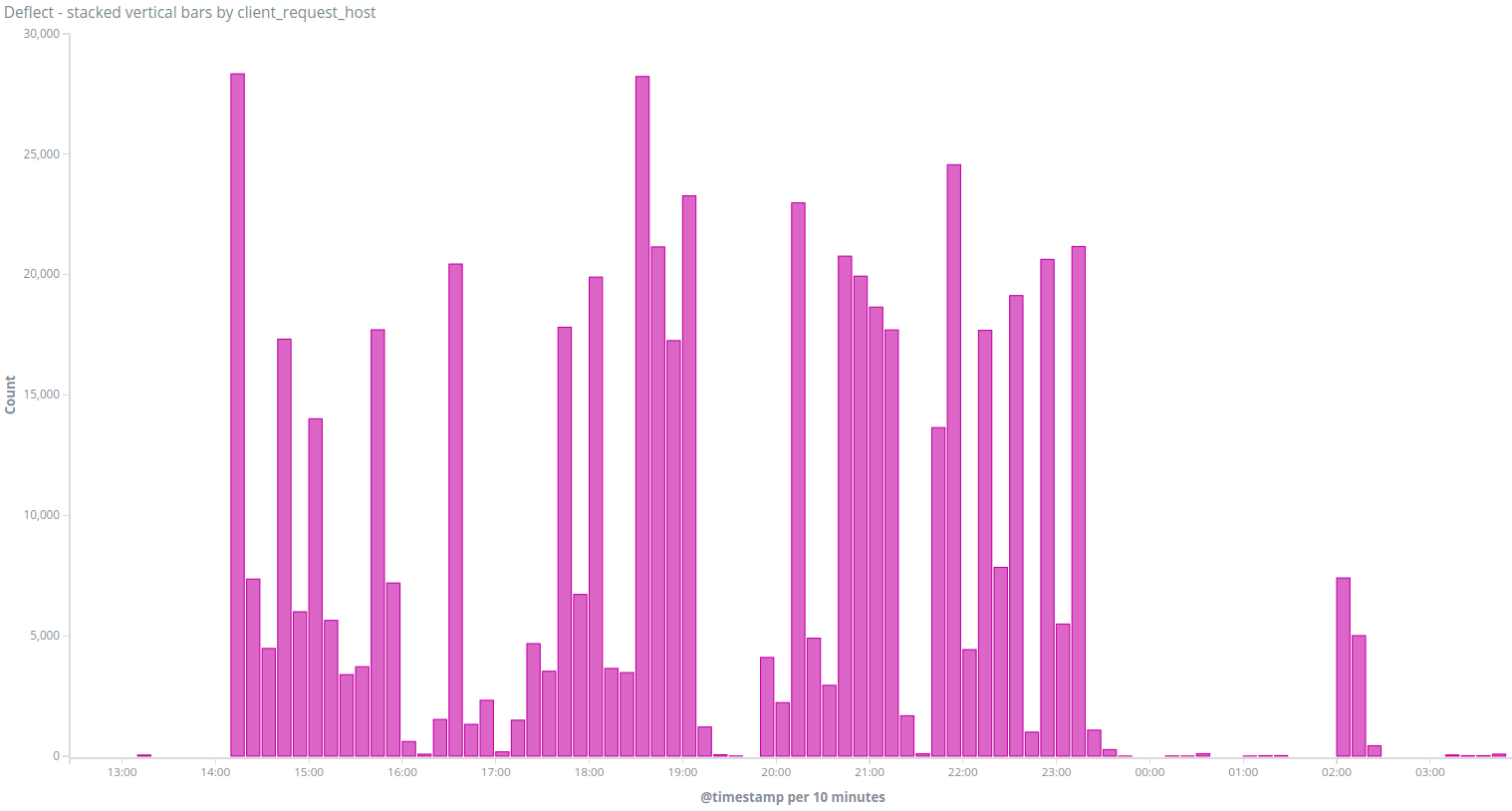
This traffic was definitely coming from the same attack group as it was using the same user agent (python-requests/2.9.1) and requesting the same page /?s=nguyenphutrong.
The IP 66.70.255.195 is an open HTTP proxy located in the OVH network in Montreal, and listed in different proxy databases (like proxydb or proxyservers). It is surprising to see an HTTP proxy used here considering the heavy attack done 5 days before by the same group. Using an open HTTP proxy definitely brings anonymity to the attack but it also limits the bandwidth for the attack to the proxy bandwidth (in that case 5000 requests per minutes at its maximum). Our hypothesis is that a group of people with different skills and resources are sharing the same tool to target baotiengdan.com. It is also possible that one person or one group is trying different attacks to see what is the most effective.
Group D
The fourth group only consists of one attack coming from an IP address in Vietnam on the 12th of June 2018, when we saw a peak of requests from the IP 113.189.169.XXX on the website viettan.org :
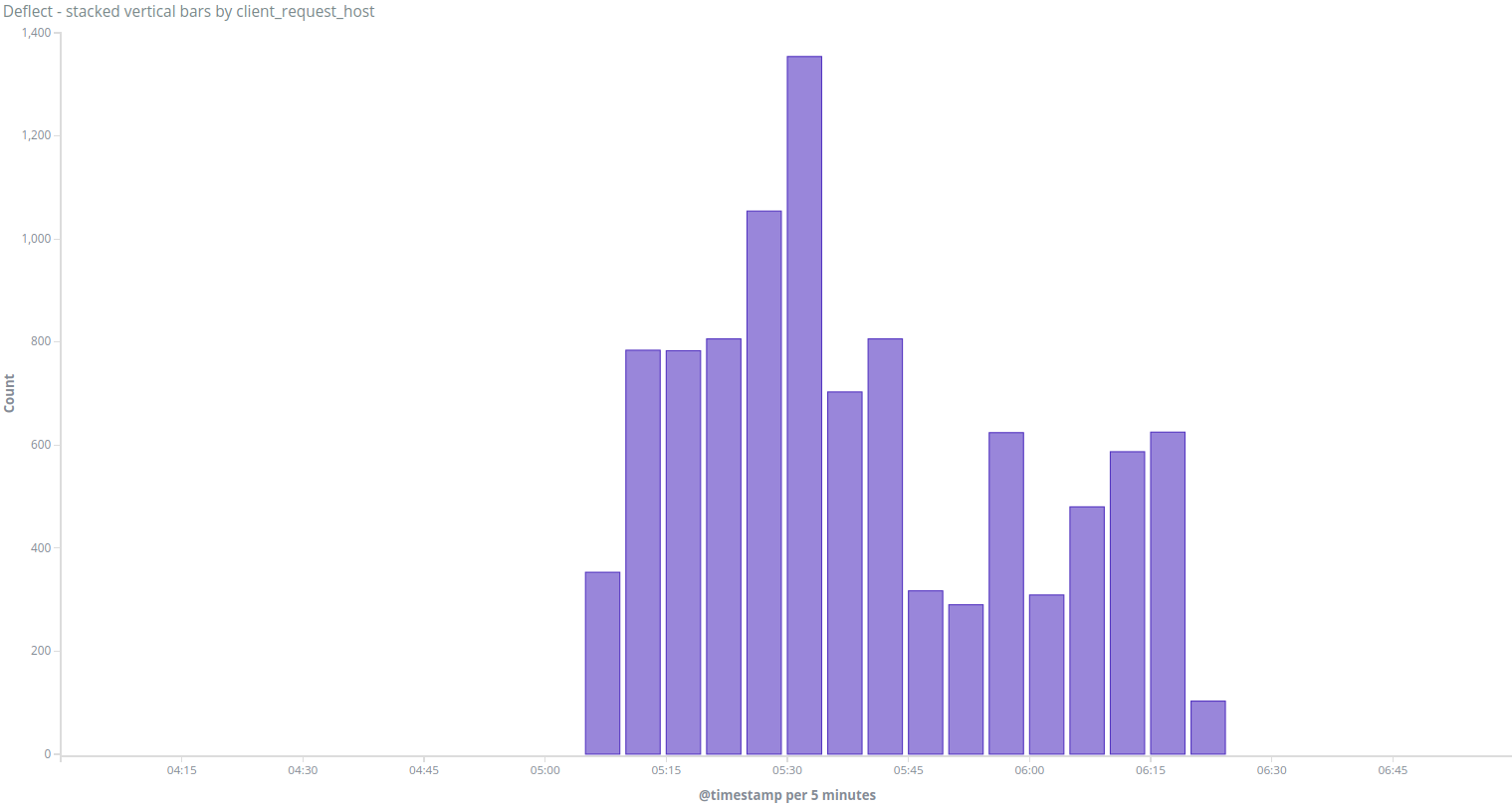
This attack had the following characteristics :
- Query / with a random query (like
?%7F) in order to avoid Deflect caching - Using a random user agent from a list of 329 user agents values.
These are pretty clear characteristics that we have not seen in other attacks before. This IP address belongs to the AS 45899 managed by the state-owned Vietnam Posts and Telecommunications Group company. It seems to be a standard domestic or business Internet access in Haiphong, Vietnam. Considering the low level of the attack, it is completely possible that it came from an individual from their personal or professional Internet access.
Links with other attacks
On the 10th of July, Qurium published a report about DDoS attacks against two vietnamese websites : luatkhoa.org and thevietnamese.org on the 11th of June 2018. Luật Khoa tạp chí is an online media covering legal topics and human rights in Vietnamese. The Vietnamese is an independent online magazine in Vietnam aiming at raising public awareness on the human rights situation and politics in Vietnam among the international community.
Qurium was able to confirm with us lists of IPs responsible for most traffic during this DDoS attack and we found that 4 of these IPs were also used in the incidents 1, 5, 6 and 7, all parts of the Group A.
Comparing the list of User-agents listed in the article with the list of user-agents used by incidents from Group A, we see that between 22 and 42 percents are similar :
| Compared with incident | Number of UA | Number of similar UA | Percentage |
|---|---|---|---|
| 1 | 54 & 42 | 16 | 38.10 % |
| 2 | 42 & 40 | 9 | 22.50 % |
| 4 | 57 & 42 | 15 | 35.71 % |
| 5 | 97 & 42 | 18 | 42.86 % |
| 6 | 68 & 42 | 14 | 33.33 % |
| 7 | 42 & 38 | 11 | 28.95 % |
As described before, it is hard to attribute these attacks to the same group, but they definitely share some similar TTPs. Seeing DDoS attacks with similar TTPs used during the same period of time to target 4 different political groups or independent media’s websites definitely confirms the coordinated nature of these attacks, and their particular interest in attacking Vietnamese media and civil society groups.
Mitigation
Our mitigation system uses the Banjax tool, an Apache Traffic Server plugin we wrote to identify and ban bots based on traffic patterns. For instance, we ban IP addresses making too many queries to /. This approach is efficient in most cases, but not when the DDoS is coming from multiple hosts staying under the Banjax’s thresholds. In these different incidents, half of them were mitigated automatically by our Banjax rules. For the other incidents, we had to manually add new rules to Banjax or enable the Banjax javascript challenge which requires browsers to compute mathematical operations before being allowed to access the website (hence blocking all automated tools that are not implementing javascript).
Overall, these attacks created limited downtime on the targeted websites, and when it happened, we worked in collaboration with Viettan and Tieng Dan to mitigate them as soon as possible.
Conclusion
In this report, we presented attacks that targeted Việt Tân and Tiếng Dân’s websites since mid-April this year. It shows that Distributed Denial of Service attacks are still a threat to civil society in Vietnam and that DDoS is still used to silence political groups and independent media online
On a technical level, HTTP flood is still commonly used for DDoS and is still quite effective for websites without filtering solutions. Investigating the origin of these attack is an ongoing mission for us and we are constantly looking for new ways to understand and classify them better.
One objective of publishing these reporting is to foster collaborations around analyzing DDoS attacks against civil society. If you have seen similar attacks or if you are working to protect civil society organizations against them, please get in touch with us at outreach AT equalit.ie
Acknowledgements
We would like to thank Việt Tân and Tiếng Dân for their help and collaboration during this investigation. Thanks to ipinfo.io for their support.
Appendix
Indicators Of Compromise
It is common to publicly share Indicators of Compromise (IOCs) in attack reports. Sharing IOCs related to DDoS attacks is more challenging as these attacks are often done through relays (whether proxies or compromised systems), so sharing lists of IP addresses can have side-effects over victims we cannot control. We have thus decided not to share IOCs publicly but we are open to share them privately with organizations or individuals who could be targeted by the same groups. Please contact us at outreach AT equalit.ie.
Fingerprinting systems based on Shodan data
As described earlier in this report, we have developed a script to fingerprint systems based on Shodan data. This script is published on github and released under MIT license. Feel free to open issues or submit Pull Requests.