4.4 Case Study 4
Secure Email and Blogging
Outline
An independent journalist reports on human rights violations in her country. She has a laptop on which she works from home and which she often takes with her on assignments. She writes mainly for foreign publications and uses a pseudonym, for it is dangerous to publish such information in her country, where the media are severely censored and the government is known to have sufficient expertise in tracking online journalists. She also runs a blog where all her articles are published, too.
She is finding it increasingly difficult to keep working. Her articles sent by email do not arrive at their destination, access to her blog site has been blocked and she is afraid of endangering the people whom she interviews and mentions in her reports. She fears that her email is being monitored. On one occasion, an editor wrote to her surprised by the content of her recent article. On re-reading it, she realises that the article has been altered by someone on the way from her email box to the newspaper.
Threats
Before deciding what actions to take, she lists all the current threats she is facing:
- cannot send articles by email
- cannot access her blog and update it
- her assumed identity could be compromised
- articles, stored on her laptop, are accessible to outsiders
- viruses or hackers could damage the articles on her laptop
Solutions
Secure email
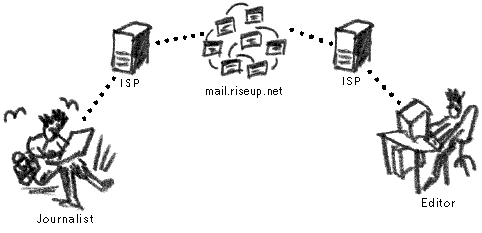
As the first priority, she decides to secure her email box, so that her messages could not be read or altered by an outsider. She writes to www.riseup.net and asks to create an account for her. This is a webmail email account that can only be accessed when she is on the Internet. The webmail operates over SSL and is therefore encrypted between her computer and the webmail server. She asks all her correspondents (recipients) to register a free account with www.riseup.net, too, so that her articles could reach them only via encrypted Internet tunnels. She decides to trust the people running www.riseup.net not to compromise or access her email.
This appears a simple and effective method for dealing the journalists’ concerns. As long as the address bar in the Internet browser through which she accesses her email account begins with ‘https:’, she knows that her communications are secure.
Secure communications over SSL Riseup.net email accounts
As a further precaution, she writes to www.riseup.net and asks them to send the fingerprint of their SSL certificate. They forward her to a page on their website where this fingerprint is shown. The precaution she is taking here is against a Man-in-the-Middle attack, whereby the adversary intercepts the communication line to www.riseup.net and attempts to fool the user into thinking they have arrived at the intended website. An SSL certificate is presented and, once the user accepts it, the connection is re-directed to the adversary’s website. However, an inspection of the SSL certificate will show whether or not it is different from the original.104
Securing information
Even though she has managed to secure her email box, she would still like to make the articles she sends unreadable to anyone but the designated recipient. This is done in case she loses her email password or it gets compromised. It is also a good precaution against Man-in-the-Middle attacks. By using the GnuPG program, she can encrypt her articles to the public key of the editor. This means that all the parties, with whom she normally communicates securely, will have to install and use a public key encryption system (like GnuPG), and swap their public keys with each other105.
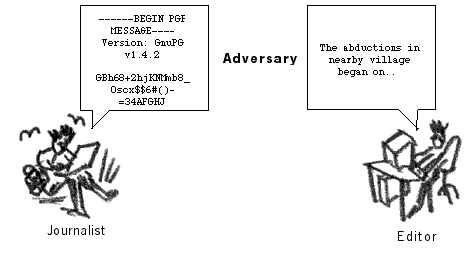
Using encryption to secure sent messages
Sometimes, the use of encryption may alert the monitoring body. She does not know whether encryption is legal in her country and whether using it will just attract a lot more unwanted attention to her. She decides to employ an alternative method that will not immediately appear cryptic and hence suspicious. By using a steganography program, she can embed her article in a photo and upload it to an inconspicuous website. As long as there is a prior arrangement, whereby the editors know where and when to look for this picture/article, this method can bypass many surveillance systems. It should be implemented by maintaining a regular stream of similar activity (uploading photos to the Internet) and should not appear irregular in her normal pattern of activity.106
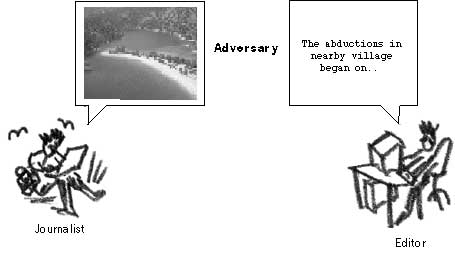
Using steganography to hide the presence of a message in your communications
Anonymous email
Another way of countering email blocking and censorship is to use an
array of popular free webmail services. Yahoo, Hotmail, Gmail and others
have millions of registered users. It is possible to create a completely
new account every time you wish to send an email. The registration
details can be random and, if sent from a public space (e.g. an Internet
café), the email would be very difficult to track.
It is likely that secure email services (like www.riseup.net) may
already be blocked or will become blocked after frequent use. Only a
handful of countries block access to large free email systems, like
Yahoo. However, these global providers have in the past cooperated with
some governments (e.g. the Chinese government) in giving the latter
access to their users’ email accounts. Should our journalist decide to
use a large webmail provider, her usage must be limited to accessing it
from an Internet café or other public space, where her details are not
recorded and the IP address, from which the email is sent, cannot be
traced back to her. She can also create accounts using a pseudonym,
pre-arranged with her editor.
Circumventing website blocks
To access her blog site, the journalist will require different methods of circumventing the Internet block inside her country. The choice of tools will depend on the government’s blocking practice. For example, she could use a popular commercial product (e.g. ‘Anonymizer’) or search the Internet for publicly available anonymous proxy servers.107
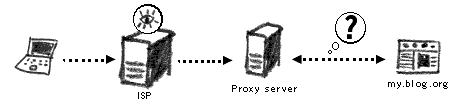
With an anonymous proxy, the destination website will not know where your computer is really located
On her laptop, she installs the Mozilla Firefox Internet browser and the switchproxy108 extension. The extension allows her to get to a particular website that lists and updates anonymous proxy server IPs. She sets the program to alternate between the different servers every 300 seconds. Not all servers will function properly all the time.
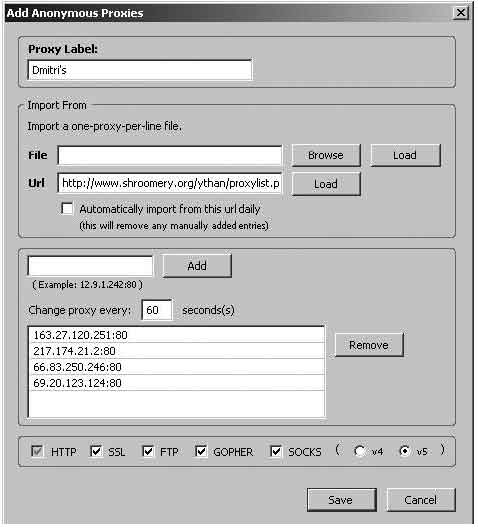
The switchproxy configuration screen
By installing the Tor program on a USB memory stick, she can operate without any blocking restrictions, but not all websites may function properly this way. Tor will anonymise her website requests and will penetrate the majority of national firewalls.
It is often easier and more practical to ask a friend from another country to upload your articles onto your blog. The articles can be transmitted by any of the above-listed secure or anonymous email methods.
Protecting identity
At present, the journalist does not wish her identity to be linked with her pseudonym. She is very careful to not include her real name in the emails and articles she sends through the Internet. Nor does she use her ISP email account, as it is linked directly to her. She only uses her home Internet connection to access a secure webmail account or does it in conjunction with an anonymous proxy server, when updating her blog.
Some Internet cafés in her town have begun to record their users’ names and times of access. She avoids these cafés, as Internet and email activity can traced back to the computer’s IP and eventually to her.
When using a computer in an Internet café, she is very careful not to allow the browser to remember her passwords and browsing history. At the beginning of her session, she spends a couple of minutes configuring the Internet browser to be more secure and deletes all saved information from the computer at the end109.
Securing laptop
All articles are written and stored on her laptop. She must secure herself against their loss, unauthorised entry and damage from viruses and spyware. She sets a BIOS password to prevent immediate access to her computer and installs a free anti-virus, anti-spyware and firewall program from the NGO in a Box - Security Edition CD. She updates her Windows software as soon as known fixes become available. Since her laptop has a CD writer, she buys some blank disks and creates a backup of her documents.
Passwords
Her laptop, BIOS, email accounts, blogs etc. require a password each. These passwords are essential to her security, as even the most advanced system is often only as good as the password that protects it. Since it is impossible to memorise all the passwords, she uses the Password Safe program to store them for her. She has a copy of the program and the password file on her laptop and USB memory sticks. To increase the securit yof her passwords, the Password Safe program creates them for her.
To sum up, she has a bag of different tricks and methods to use at her discretion. At first, they may appear laborious and time-consuming, but she knows that her security is paramount. Perhaps a secure laptop and email address will be enough for her to continue her work. As some methods of protection become obsolete or unavailable, she may choose different solutions. The Internet is a vast landscape, with many possibilities for both surveillance and anonymity.
|